NIS2 Directive Update Taking Effect in October 2024
The NIS2 Directive is a significant update to the original NIS Directive which was implemented in 2016. It aims to bolster cybersecurity resilience across the European Union (EU) by introducing stricter regulations and expanding its reach.
EU member states have until October 17, 2024, to translate the NIS2 Directive into their national laws.
This means businesses have just a bit more than 60 days (about 2 months) to ensure compliance.
Article 21 has its complete list of policies for the protection of network and information systems, as well as the physical environment of those systems from incidents.
Below is the entitlement of the requirements:
Article 21 of the NIS2 directive to protect networks, information systems & physical environment from incidents.
Why is this Security Update Important for European Businesses?
The NIS2 Directive represents a major shift in cybersecurity regulations for European businesses.
Here's why it's critical:
Fortress Against Rising Cyberattacks
Europe is a prime target for cyberattacks, with a documented surge in incidents across critical infrastructure. According to Deloitte, attacks skyrocketed by 45% globally and a staggering 220% within the EU between 2020 and 2021. NIS2 compliance strengthens your organization's online defenses and fosters a collective EU bulwark against emerging threats.
Proactive Risk Management and Business Continuity
NIS2 mandates proactive risk management strategies to identify and mitigate cyber threats before they disrupt operations. Furthermore, compliance promotes business continuity planning to ensure minimal disruption and maintain customer trust even in a cyberattack.
Improved Threat Response and Collaboration
The directive fosters better incident reporting, allowing you to notify relevant authorities about security breaches and their potential consequences. This timely information sharing safeguards other organizations and fosters collaboration within the business community to exchange best practices and threat prevention experiences.
New Industries Under the NIS2
One of the significant changes in the NIS2 Directive is the expansion of its scope. The updated directive now includes more industries than the original version.
Previously, the NIS Directive targeted sectors like energy, transport, banking, and health.
NIS2 extends to cover additional industries such as:
Food and water supply chains
Digital infrastructure
Public administration
Space industry
Waste management
This expansion means that more businesses will need to align with the new cybersecurity standards, ensuring a wider net of protection across the EU.
Fines & Penalties
Non-compliance with NIS2 can lead to significant financial penalties that vary depending on the classification of your organization (essential entity).
Here's a breakdown of the potential consequences:
Essential Entities
Failing to comply can result in fines of up to €10 million, or less, a penalty reaching 2% of your total global annual turnover. That's a significant financial blow that could cripple your business.
Important Entities
The penalties are still substantial, with fines reaching €7 million or 1.4% of your global annual turnover.
Beyond hefty fines, NIS2 also enforces stricter accountability on management. Company leaders can be held personally liable for infringements, facing potential temporary bans and even the suspension of services. This underscores the seriousness with which the EU views cybersecurity and the importance of implementing robust security measures.
NIS2 Compliance Directive with Gart: Tips & Recommendations
At Gart Solutions, we understand the challenges businesses face in navigating complex regulations like NIS2. Here are some tips to help you achieve compliance:
Identify Your Compliance Status
The first step is to determine whether your organization falls under the scope of NIS2. We will help you to conduct a thorough assessment of your industry and activities.
Perform a Security Risk Assessment
Identification and evaluation of potential cybersecurity risks is a must. Gart can manage this journey within your organization.
Develop a Cybersecurity Strategy
We will help to evaluate your security posture and design a cybersecurity strategy that addresses the risk management profile.
Invest in Employee Training
As Gart is an IT Consulting provider — we also dedicate our efforts to educate your employees on cybersecurity best practices to prevent social engineering attacks and phishing attempts.
Seek Expert Guidance
Partnering with a trusted cybersecurity solutions provider like Gart Solutions can ensure you have the resources and expertise necessary to achieve and maintain NIS2 compliance.
Contact us for a Free Consultation.
Download our Free Checklist
See how we can help to comply with the latest NIS2 requirements
Download
NIS2-Compliance-Checklist-A-Comprehensive-Guide-to-Audit_Free-PDFDownload
Choosing the EU Cloud Solutions Provider: What is The Way to Be Prepared for the Update?
Choosing the EU cloud provider is one of the options to be prepared for the NIS2 compliance update.
Gart Solutions, together with our partner — vBoxx, a renowned EU cloud solutions provider, offers a range of managed hosting and cloud server services that can significantly support businesses in their digital transformation journey.
vBoxx is an expert in the data journey part of NIS2 and has outlined how to simplify your data security compliance:
1. Understanding the NIS2 Directive
The NIS2 Directive represents a significant evolution in EU cybersecurity regulation, broadening the scope of compliance requirements to include a wider array of sectors. This directive underscores the necessity of not only securing data but also understanding its entire journey.
Organizations must be vigilant about tracking their data flow to mitigate risks and meet the stringent new standards imposed by NIS2.
2. Comprehensive Data Tracking
Compliance with NIS2 requires an in-depth understanding of where and how data is processed, stored, and transferred. This involves documentation of every stage of the data lifecycle — from creation and processing to storage and eventual deletion. By mapping out the data journey, organizations can better identify vulnerabilities and ensure that all parties involved in data handling adhere to high security standards.
3. The Challenge of Sub-processors
One of the most complex challenges introduced by NIS2 is the need for organizations to maintain visibility over all sub-processors involved in data processing. Each sub-processor, regardless of their role, must meet the same rigorous cybersecurity standards. This requires thorough vetting and ongoing monitoring to ensure compliance, making it critical for businesses to establish strong relationships and clear communication channels with their sub-processors.
4. Strategic Shifts in the Market
In response to NIS2, many businesses are re-evaluating their reliance on third-party sub-processors, especially those located outside the EU. By consolidating data operations within the EU, organizations can better manage compliance and reduce the risk of data breaches.
This trend towards localized data handling is reshaping the market, as companies seek to simplify their data ecosystems and enhance security.
5. Practical Steps for Compliance
To align with NIS2, businesses must take proactive measures, such as engaging closely with their service providers, conducting comprehensive risk assessments, and considering a shift to EU-based data centers and services. These steps not only facilitate compliance but also strengthen the overall cybersecurity posture, ensuring that the organization is well-prepared to meet current and future regulatory demands.
How Not to Repeat Mistakes: Case of Microsoft
If you say, we are using public data providers, there’s still are pitfalls we have to consider.
Let’s take, for example, Microsoft. Microsoft's products continue to be widely used, but they present significant challenges in transparency and data security.
At the time of writing, Microsoft lists 47 subprocessors and 36 data centers, but details on their operations and data handling are unclear. This is concerning given Microsoft's ongoing GDPR violations and multiple security breaches last year.
Moreover, the global spread of subprocessors, often linked to parent companies in various countries, adds complexity and potential security risks, making it difficult for companies to verify compliance and data safety.
Learn more about Microsoft’s Data Practices and the numerous DDoS attacks they responded to. This is a good case of how not to repeat their mistakes.
Final words
Prepare your business for the NIS2 compliance update with the expert guidance of Gart Solutions and our partner — vBoxx. Download our Free Checklist — a comprehensive guide to the NIS2 audit, and ensure your organization is ready for the upcoming changes.
Partner with Gart Solutions and vBoxx — overcome the security challenges and align with NIS2 in this ever-evolving cybersecurity landscape.
Wanna know how? Contact us.
Schedule a Free Consultation
See how we can help to overcome the challenges of NIS2 compliance.
Contact us

The business world feels like it's on fast forward these days. New tech pops up all the time, and keeping your data safe is getting trickier by the minute. No wonder businesses need to make sure their IT infrastructure is in tip-top shape! An IT infrastructure audit is basically a checkup for your tech systems, making sure they're ready for whatever comes next.
Key Objectives of an IT Infrastructure Audit
An IT infrastructure audit plays a crucial role in shaping an organization's technical and business development plans. The technical plan outlines the requirements, goals, architecture, and resources for IT infrastructure development. An audit helps identify the strengths and weaknesses of the current system, define requirements for future development and improvement of IT infrastructure, and plan the necessary resources and budget to accomplish these tasks.
Core Objectives of an IT Infrastructure Audit:
Security Evaluation
An audit enables a comprehensive analysis of security levels, including the assessment of protective measures, data confidentiality, and prevention of potential threats. This is crucial for safeguarding information both within the organization and against external cyberattacks.
Resource Optimization
An audit helps uncover opportunities to optimize IT resources, enhance the performance and efficiency of IT systems, and streamline resource utilization within the organization
Compliance Assessment
An audit facilitates the evaluation of IT infrastructure's adherence to standards, regulatory documents, and legislation governing information systems. This helps confirm the organization's compliance with security, data privacy, and data integrity requirements.
Development Planning
The findings of an IT infrastructure audit serve as the foundation for developing an organization's technical and business development plans. The audit aids in identifying IT system strengths and weaknesses, prioritizing development needs, and planning system changes and upgrades based on concrete results and recommendations.
Technical debt
Technical debt is the accumulation of legacy systems, software, and hardware that can negatively impact the performance, security, and scalability of the IT infrastructure. An IT infrastructure audit can also be used to assess and manage technical debt.
Loss and Disruption Prevention
An audit helps identify potential risks and vulnerabilities in IT infrastructure, enabling proactive measures to mitigate them. Conducting an audit contributes to preventing potential disruptions and issues, and allows for the development of backup, data recovery, and business continuity plans.
When an IT Infrastructure Audit is Essential
Alright, let's talk about when you'd want to get that IT infrastructure audit done. These audits are crucial for organizations these days - they help make sure your tech is running smoothly and can handle whatever comes your way.
Here are some key times when you'd definitely want to get an audit going:
Implementing new systems and tech
Bringing in new software, hardware, or information systems? Get an audit done first. It'll help you catch any potential issues or risks before you roll everything out, so you can make sure the new stuff integrates seamlessly and operates safely.
Your business is growing or changing
If your company is expanding, shifting gears, or just generally evolving, an audit can tell you if your IT infrastructure is ready to support those changes. It'll help you identify any problem areas, optimize your processes, and make sure your tech can keep up with the new business demands.
Beefing up your security
With all the cyberthreats out there these days, evaluating your system security is huge. An audit will show you where your vulnerabilities lie so you can shore up your defenses and protect your critical data and resources.
Streamlining operations
Audits don't just check for risks and problems - they can also uncover opportunities to optimize your processes and resources. Having that detailed look at how your tech is being used can help you cut costs, boost efficiency, and set the right performance metrics.
So in a nutshell, IT infrastructure audits are essential for organizations dealing with growth, changes, security concerns, or just a need to run a tighter, more cost-effective tech operation. They give you the insights you need to keep your systems performing at their best.
If you skip the audits, problems will just start piling up over time. Here's what can happen:
Lack of info and unreliable data
No IT audits means limited intel on the current state of your systems. You could end up using outdated or just plain wrong data when making important decisions. That makes planning a real headache and can lead to some seriously misguided strategic calls.
Security risks and vulnerabilities
Without regular audits, your organization is wide open to cyberattacks, data breaches, and other security issues. If you're not checking for weaknesses on the regular, you'll have no idea where you're vulnerable - and that's a disaster waiting to happen.
Wasted resources
No audits means you could be over- or underutilizing your resources, which kills productivity and wastes money on ineffective solutions. That's a surefire way to lose your competitive edge.
Doing those IT audits lets you get out in front of problems, optimize your resources, lock down your security, and make sure your tech is running like a well-oiled machine. It helps you make smart decisions, minimize risks, and keep up with your current needs.
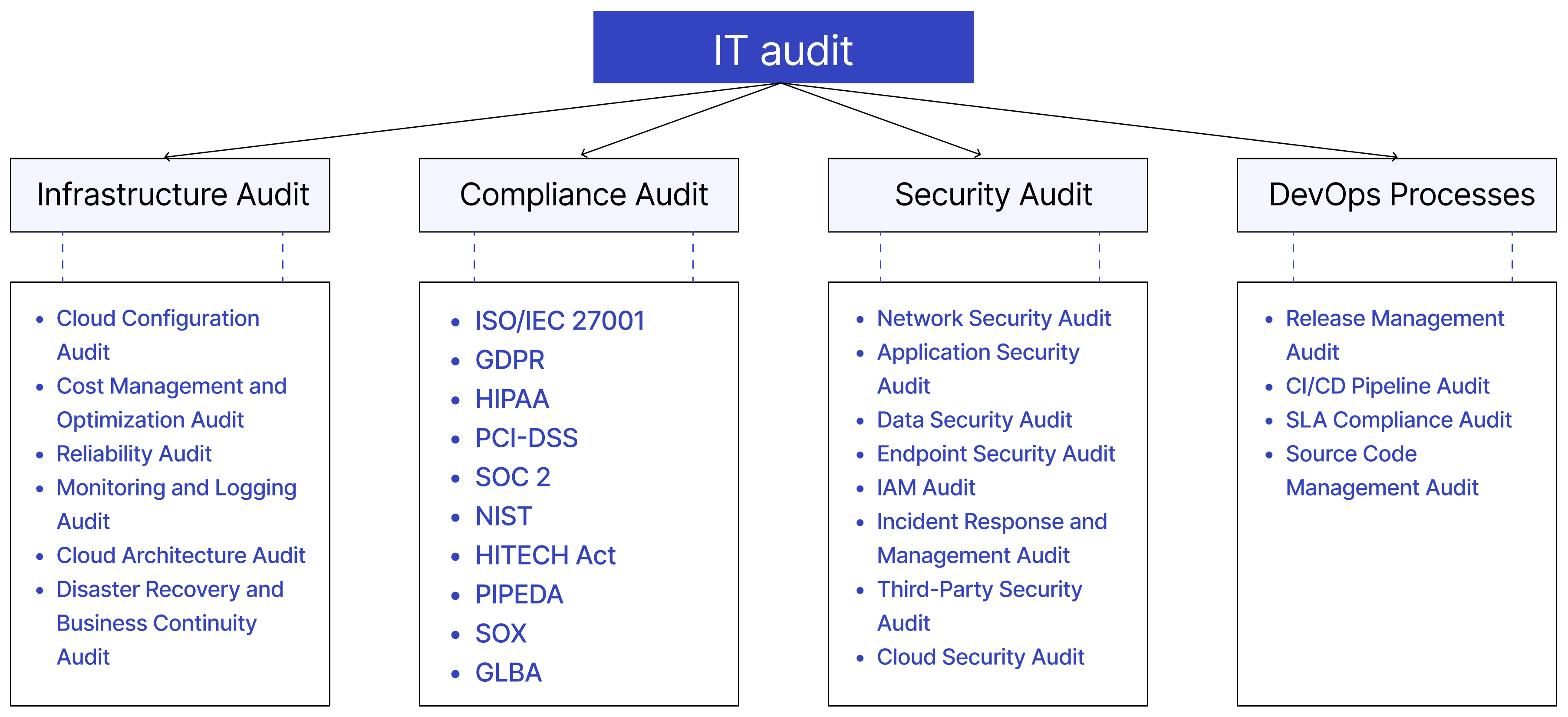
IT Infrastructure Audit Checklist
Alright, on top of that stuff about the challenges of selecting an IT auditor, we've also put together an IT infrastructure audit checklist for you. This is like a handy reference guide to make sure you've covered all your bases when getting that audit done.
The checklist hits on all the major areas an auditor is gonna want to dig into - things like your cloud infrastructure, virtual environment, data storage, and overall service architecture. We break down the key things that need to be evaluated in each of those domains.
Cloud IT Infrastructure AuditDownload
It's a comprehensive list, but easy to follow along with. Helps ensure the audit is thorough and you're not missing any critical components of your IT setup. Just go through it step-by-step and you'll have a clear roadmap for the auditor to follow.
Key Considerations when Vetting IT Infrastructure Auditors
Alright, let's talk about the common issues and challenges that organizations face when selecting an IT infrastructure auditor:
Auditor Qualifications. One of the main problems is determining the true qualifications and professionalism of the auditor. Customers often have a hard time evaluating the auditor's actual experience.
Accuracy and Objectivity. Ensuring the auditor will provide an unbiased, objective assessment is crucial. Customers want to be confident the auditor will thoroughly evaluate all aspects of the IT infrastructure without any preconceptions or subjectivity. Finding a reliable, responsible auditor who can guarantee the accuracy and objectivity of their work is a tricky task.
Service Costs. The cost of the auditor's services is another significant challenge. Customers need to strike the right balance between service quality and price. Comprehensive IT infrastructure audits can be quite expensive, putting them out of reach for some organizations. However, the lowest price isn't always the best criteria, as rock-bottom costs may signal low-quality work.
Availability and Timelines. Auditor availability and their ability to complete the work on schedule are other problems. Auditors are often booked on other projects or have time constraints, making it hard to find one who can fit the customer's schedule. Flexibility on timelines is important.
Trust Issues. Trusting the auditor is a core challenge. Customers need to be confident in the auditor's reliability and their ability to provide an accurate assessment. Checking references, reviews, and credentials can help address this.
Selecting an IT infrastructure auditor is a complex, high-stakes process. Thoroughly researching the auditor's background, experience, and reputation online can provide valuable insights. For example, at Gart Solutions, we publish client reviews and share details on our completed audit engagements.
Get a sample of IT Audit
Sign up now
Get on email
Loading...
Thank you!
You have successfully joined our subscriber list.
How Often Should You Conduct IT Infrastructure Audits?
As a general rule, companies should conduct an IT infrastructure audit at least once a year. However, in some cases, more frequent audits might be necessary. For instance, companies handling sensitive data may require audits every six months or even quarterly.
The results of an IT infrastructure audit should lead to a series of action items, such as:
Addressing security vulnerabilities: The audit should identify any security weaknesses within the IT infrastructure, and steps should be taken to close those gaps.
Enhancing performance: The audit should pinpoint areas where IT infrastructure performance can be improved, and actions should be taken to implement those improvements.
Reducing costs: The audit should identify areas where IT infrastructure costs can be lowered, and actions should be taken to achieve those cost savings.
Developing a Business Continuity Plan (BCP): A BCP outlines how the company will continue operations in case of an IT outage. The audit should contribute to developing or updating an existing BCP.
A well-conducted IT infrastructure audit can significantly help businesses maintain a secure, performant, and cost-effective IT infrastructure.
The final report's got the full scoop on any issues or weaknesses they found in the infrastructure. This gives the leadership team a clear, unbiased view of where things are at and what needs to be fixed. Armed with those audit results, they can put together an action plan to boost the efficiency of the tech, optimize the processes, and shore up any vulnerabilities in the system.
The key is using that audit as a roadmap to getting the IT infrastructure operating at peak performance. No more guesswork - just cold, hard data to drive the improvements.
Gart Solutions - Your Trusted DevOps & Cloud Services Provider.
We have extensive experience conducting IT infrastructure audits that deliver the insights organizations need.
Our case studies:
Infrastructure Optimization and Data Management in Healthcare
AWS Infrastructure Optimization and CI/CD Transformation for a Crypto Exchange
New Infrastructure Design and GCP Cost Optimization for Telecom SaaS Application
AWS Migration & Infrastructure Localization for Sportsbook Platform

Information security is crucial in the business world. Companies choose various approaches to address tasks related to the storage and processing of confidential data. One of them is ISO 27001.
ISO 27001 is an international standard that defines requirements for the creation, implementation, improvement, and maintenance of an Information Security Management System (ISMS).
[lwptoc]
Recently, we successfully prepared our client for ISO 27001 certification. Based on a recent case, we want to share with you the procedure.
This standard establishes frameworks and principles for safeguarding confidential information within an organization, covering various aspects such as
financial data
intellectual property
personal employee data
and other information about third parties.
Over an extended period globally, efforts have been made to create uniform rules for protecting personal data, leading to the adoption of the General Data Protection Regulation (GDPR). All companies processing data of individuals from the European Union must comply with this regulation. While the document exists, there is no certificate confirming adherence to these standards. This is where ISO 27001 comes to the rescue, as its standards partially align with the requirements of GDPR, and compliance can be validated with a certificate.
ISO 27001 for Businesses
The certification of ISO 27001 is becoming increasingly relevant not only for large organizations but also for small and medium-sized companies in the context of technological advancement.
Every modern enterprise, to some extent, has tools for managing information security risks. In simpler terms, every company takes measures to secure its informational assets and restrict access to its systems. The Information Security Management System (ISMS) aligns all components of the organization's information security system to ensure that all system policies, procedures, and strategies work as a cohesive unit.
It's important to note that certificates do not provide an absolute guarantee of security but rather confirm adherence to specific criteria set by the accrediting body. For instance, the presence of an ISO/IEC 27001 certificate does not ensure 100% data security; it simply attests that the company meets certain information security standards.
Need assistance on your ISO 27001 journey? Reach out to Gart for personalized support and ensure your company's information security is top-notch.
Why is standardization important for business? Advantages of ISO 27001 Certification
ISO 27001 certification is a powerful tool for building and maintaining trust in the client-supplier relationship. The competitive advantage gained through ISO 27001 extends beyond marketing, influencing real success and the resilience of the business.
Obtaining the certificate comes with numerous benefits. Firstly, it confirms that the company takes information security seriously, a crucial factor for clients and partners. The certificate enhances trust and demonstrates adherence to established standards.
Cost Savings
It sounds incredible, but the certification process can actually lead to substantial cost savings for the company in the future. When ISO 27001 certification is conducted properly, it results in long-term economic benefits. For instance, Gart's strategic approach streamlines processes, allowing teams to focus on higher-level tasks, ultimately reducing costs associated with compliance audits.
A clear understanding of risks enables cost optimization and the formulation of effective security policies.
Increased Sales
ISO 27001 certification is a significant marketing asset. Clients are drawn to the commitments a business makes by obtaining the certificate. The enhanced reputation attracts new clients and partners, fostering business growth.
Reputation Protection
Certification elevates the level of company security, introducing improved policies and technologies. A modern security system helps avoid the detrimental impact of malicious actors on your business. ISO 27001 certification allows you to demonstrate a commitment to information security, ensuring data confidentiality and integrity. It also contributes to attracting clients and serves as a competitive advantage for your business. Regular audits help identify risks and respond to changes in the environment.
How to Prepare Your Company for ISO 27001 Certification?
Achieving ISO 27001 certification is a complex task that requires thorough preparation and involves various types of work. This process demands the involvement of a significant number of employees and entails lengthy and costly preparations.
Therefore, at the initial stage, it is crucial to develop a detailed action plan outlining specific tasks, who will be working on them, when they will be accomplished, and how the project will be executed.
Appoint a dedicated team responsible for the certification process, including representatives from different departments. Conduct training for staff on information security and the implementation of an Information Security Management System (ISMS).
Start by understanding the ISO 27001 standard and its requirements. It is essential to carefully study the ISO 27001 standard, which consists of two parts:
The main part, which contains the core content of the standard.
Appendix A, which includes a list of 114 potential control measures.
Ready to elevate your information security standards? Gart is here to guide you through ISO 27001 certification. Let's strengthen your defense against cyber threats together.
Approximate ISO 27001 Preparation Plan
Analysis
Assess the current state of your Information Security Management System (ISMS). Identify gaps between existing practices and ISO 27001 requirements. Also, crucially, determine which part of your organization falls under the scope of ISO 27001.
Documentation
Develop and document policies, processes, and procedures aligned with ISO 27001. Create a Statement of Applicability (SoA) defining the scope of your ISMS.
Risk Assessment
Conduct a thorough risk analysis to identify potential security threats. Develop a risk treatment plan to manage and mitigate the identified risks.
Implementation
Ensure employee training and awareness regarding their roles in preserving information security.
Internal Audit
Conduct an internal audit to assess the effectiveness of implemented measures. Identify areas for improvement and corrective actions. At this stage, you may consider engaging external consultants with the necessary expertise, and companies like Gart offer professional services for ISO 27001 certification preparation.
It's also important to note that ISO 27001 is related to several other standards, such as ISO 22301, ISO 31000, and ISO 27003.
External Audit
Demonstrate compliance with ISO 27001 standards. Select an auditor or certification body to conduct the final audit and issue a certificate if your company meets the requirements. After successfully completing the external audit, obtain the ISO 27001 certificate.
What is the cost of obtaining an ISO 27001 certificate?
The cost of obtaining an ISO 27001 certificate can vary significantly and depends on various factors, including the size of the company, the complexity of its information systems, the industry, geographical location, and other considerations. Typically, it's a bespoke matter that is discussed with the agency or organization overseeing the certification process. Even with an approximate cost estimate, it's advisable to include a contingency reserve in the budget.
ISO 27001 vs. SOC 2 table
AspectISO 27001SOC 2ScopeInformation security management system (ISMS)Controls relevant to security, availability, processing integrity, confidentiality, and privacy of information stored in the cloudFocusComprehensive security frameworkSpecific emphasis on cloud securityRequirementsBroad range covering risk assessment, policies, procedures, and continual improvementFocus areas include security, availability, processing integrity, confidentiality, and privacyApplicabilityApplicable to all types of organizationsEspecially relevant for service organizations hosting data in the cloudCertificationISO 27001 certificationSOC 2 complianceBenefitsDemonstrates commitment to information security and data protectionProvides assurance to clients and stakeholders regarding security controls in placeMarket RecognitionGlobally recognized standardIncreasingly recognized and sought after, particularly in tech and service sectorsCustomizabilityHighly customizable to fit organizational needsAllows flexibility in selecting applicable trust services criteriaContinuous ImprovementRequires continual assessment and improvementEncourages ongoing monitoring and refinement of controlsRegulatory ComplianceHelps organizations comply with various regulationsCan assist in meeting regulatory requirements, especially in data privacy and security standards
Conclusion
ISO 27001 certification is not just a compliance requirement; it is a journey towards excellence in the realm of information security. Preparing for ISO 27001 certification is a task that demands dedication, collaboration, and systematic efforts from the entire company.
Ready to embark on your ISO 27001 journey? Contact Gart for expert guidance and let's achieve information security excellence together.