Kubernetes has become the de facto standard for containerized application deployment, but its rise also attracts malicious actors. Kubernetes security is now a top priority as the attack surface expands with increasing adoption. This comprehensive guide explores the state of Kubernetes security, analyzing the major risks, vulnerabilities, and essential best practices to fortify your cloud-native infrastructure.
[lwptoc]
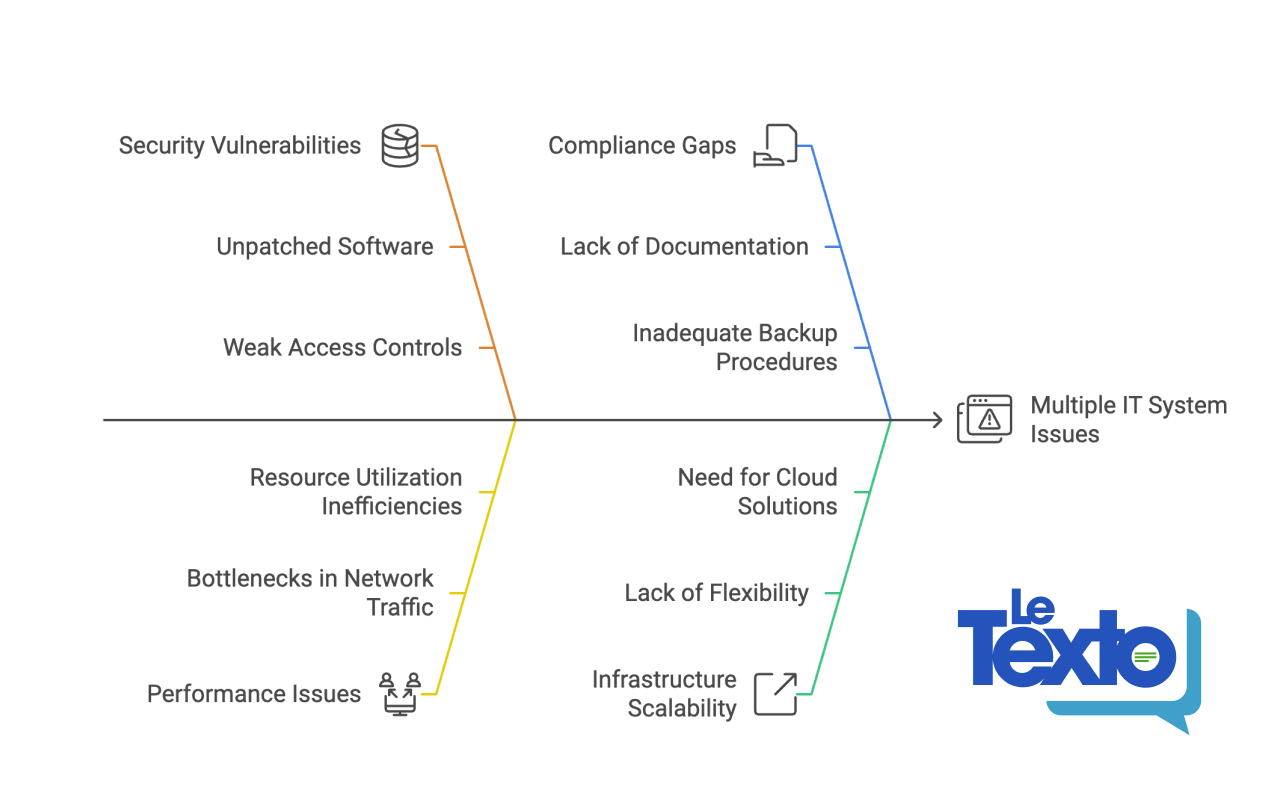
The explosive growth of Kubernetes has not been without consequences - it is increasingly becoming a target for various attacks. The situation is compounded by the fact that a typical Kubernetes cluster accumulates many components necessary for its full operation. This integration complicates the infrastructure, expanding the range of directions for attacks by malicious actors.
According to the Red Hat 2023 State of Kubernetes Security Report, security issues have a significant impact on businesses:
Slowed Deployments: 67% of organizations reported delaying or halting deployments due to security concerns. Security becoming an afterthought negates the agility benefits of containerization.
Financial Losses: 37% of companies experienced revenue or customer loss due to a Kubernetes security incident. Security breaches can disrupt critical projects and damage customer trust.
Employee Impact: Security incidents can even lead to employee terminations (21%) and organizational fines (25%).
The report highlights the pervasiveness of security threats throughout the application lifecycle:
All Phases Affected: While runtime is the most common attack point (49%), the build and deployment phases are almost equally vulnerable (nearly 45%).
Security Misconfigurations: A worrying 45% of respondents admitted to experiencing misconfiguration incidents, highlighting the need for robust security practices.
Unpatched Vulnerabilities: Another 42% discovered major vulnerabilities requiring remediation, indicating a lack of thorough security testing.
Main Kubernetes Security Risks
Container Escape is one of the most frequently exploited vulnerabilities in Kubernetes. Implementing security standards for pods (e.g. seccomp mode enabled by default starting in Kubernetes 1.22) and using Linux security modules like AppArmor and SELinux can help mitigate this risk.
The 2023 Sysdig Cloud-Native Security and Usage Report is based on data collected from billions of containers, thousands of cloud accounts, and hundreds of thousands of applications their customers ran over the past year. It highlights these main security threats:
Supply Chain Risks: 87% of images have high or critical vulnerabilities. Teams must prioritize as there are so many. Interestingly, 85% of critical vulnerabilities have fixes available but don't make it to the container runtime for various reasons. Teams spend time on non-applicable threats while real risks go unaddressed. They recommend prioritizing vulnerabilities that actually impact the runtime environment.
Shortened Container Lifecycles: 72% of containers live less than 5 minutes, up 28% from 44% in 2021. Such short lifespans make debugging applications or infrastructure issues difficult.
Security Issues Continue Impacting Business
67% of companies delayed or slowed deployment due to security concerns. As organizations adopt cloud-native like Kubernetes and microservices architectures, unforeseen security challenges often arise. When security is an afterthought, the agility gained from containerization is negated. Some are overwhelmed by security needs across the application lifecycle.
Security Incidents Impact Employees and Revenue
21% of respondents said an incident led to employee termination, and over a third experienced revenue or customer loss. Compliance violations or data breaches can result in talent loss, experience loss, regulatory fines, and negative publicity. 37% cited revenue/customer loss from a Kubernetes security incident, which could delay projects, product releases, and lose market share.
Incidents Impact All Lifecycle Phases
90% experienced at least one security incident in the last year across all phases - 49% in runtime, but nearly as many in build/deploy. Kubernetes prioritized developer productivity over security, so hardening like SELinux is challenging to customize and integrate. 45% had a misconfiguration incident, 42% a major vulnerability, and 27% failed an audit.
Security Remains a Top Concern
38% think security investment is inadequate as containers/Kubernetes add complexity. Containers emphasize agility, so security testing may not be prioritized as much as deployment speed. Properly investing means understanding Kubernetes risks and implementing controls across all layers.
Decentralized Security Responsibility
Less than a third consider the security team responsible for Kubernetes security. Securing Kubernetes requires different teams to own parts of the lifecycle - DevOps for infrastructure, security for policies/controls, developers for app/image security, operations for access controls, etc.
Embracing DevSecOps
45% have advanced DevSecOps integration with automated security practices across the lifecycle. 39% more are early-stage. However, 17% still separate DevOps and security, likely making them more reactive.
Top Concerns: Misconfigurations and Vulnerabilities
Over 50% worry about misconfigurations and vulnerabilities due to Kubernetes customizability. The complex environments with rapid scaling make consistent security posture challenging. The shared kernel means one vulnerability can impact multiple containers/hosts. Automating security scanning for common issues like privileged containers, vulnerable dependencies, and insecure defaults can mitigate risks.
The Majority Address Misconfiguration Concerns
Exposed/unprotected sensitive data is the most worrying misconfiguration at 32%. With configuration a leading cause for concern, respondents did not single out any one misconfiguration as significantly more worrisome than others. This underscores the need for a comprehensive approach to securing all Kubernetes components. Encouragingly, organizations are taking steps to address risks - 75% who worried about default configurations are working to remediate them.
Consequences Can Be Serious
Ransomware from misconfigurations is the top cited concern at 40%. Human error behind most breaches can increase breach cost and detection time. 41% worry most about ransomware, and 53% of those experienced a ransomware attack last year. For each cited consequence, a larger percentage had actually experienced it, like 46% with data deletion despite only 34% worried about it. This may indicate being inundated with concerns, lack of resources, or decentralized security ownership.
Software Supply Chain Risks
35% most worry about supply chain software vulnerabilities. Supply chain security is a hot topic after incidents like SolarWinds and Log4Shell. Respondents are concerned about vulnerabilities and open source usage, which are understandable risks if components contain flaws or are unmaintained.
Their concerns are well-founded - over half experienced virtually every supplied chain issue, with vulnerable components at 69% and CI/CD weaknesses at 68% most common.
Scanning and Attestation Are Key Controls
Nearly half identified artifact signing as most important for supply chain security. Attestation ensures software meets standards and is uncompromised, building trust across the supply chain participants like internal teams, vendors, and open source.
Scanning and attestation are two of the most important security controls for software supply chain security:
47% Vulnerability scanning
43% Security attestation (image signing, deployment signing, pipeline attestation, etc.)
40% Access and authentication
34% Configuration management
31% CI/CD integration and security automation
29% Registry governance
20% IDE scanning
Popular Open Source Security Tools
KubeLinter at 37% and Kube-hunter at 32% are the top used open source Kubernetes security tools. Open Policy Agent, a policy engine for Kubernetes and more, ties Kube-hunter at 32% usage.
37% KubeLinter
32% Kube-hunter
32% Open Policy Agent (OPA)
29% Kube-bench
19% Falco
14% Terrascan
14% StackRox
10% Clair
9% Kyverno
8% Checkov
Common Mistakes in Kubernetes Security
The Fairwinds Security, Cost and Reliability Workload Results report evaluates statistics from over 150,000 workloads across hundreds of companies using Fairwinds Insights. Its authors also believe Kubernetes security is deteriorating. The stats show users often neglect best practices:
Enabled Risky Linux Capabilities: Like CHOWN, DAC_OVERRIDE, FSETID, FOWNER etc. Some are enabled by default though most workloads don't need them. Only 10% of companies disabled them in 2022, down from 42% in 2021. A third run almost all workloads in an insecure mode. This is compounded by security-enhancing settings like allowPrivilegeEscalation being disabled by default.
44% run 71%+ of workloads as root, up 22% from last year - puzzling given the CVE count in this area.
62% of organizations have at least half their workloads potentially vulnerable to image vulnerabilities, up significantly.
Outdated Helm Charts: 46% have half or more workloads on outdated Helm charts, up from 33%.
Privilege Excess: Sysdig data shows 90% of privileges go unused despite cloud security and zero trust best practices.
Have Security Concerns About Your Kubernetes Environment? Contact Gart Solutions for Expert DevOps and Cloud-Native Security Guidance.
Recommendations to improve Kubernetes security
When security is an afterthought, organizations risk negating the core benefit of faster application development and deployment by not ensuring their cloud-native environments are built, deployed, and managed securely. Our findings show events in the build and deploy stages significantly impact security, underscored by the prevalence of misconfigurations and vulnerabilities across organizations. Security must therefore shift left, imperceptibly embedding into DevOps workflows instead of being "bolted on" when an application nears production deployment.
Use Kubernetes-Native Security Architectures and Controls
Kubernetes-native security leverages the rich declarative data and native controls in Kubernetes to deliver key security benefits. Analyzing Kubernetes' declarative data yields better risk-based insights into configuration management, compliance, segmentation, and Kubernetes-specific vulnerabilities. Using the same infrastructure and controls for application development and security reduces the learning curve and supports faster analysis and troubleshooting. It also eliminates operational conflicts by ensuring security gains the same automation and scalability advantages Kubernetes provides infrastructure.
Security Across the Full Lifecycle
Security has long been viewed as inhibiting business, especially by developers and DevOps teams mandated to deliver code quickly. With containers and Kubernetes, security should accelerate business by helping developers build strong security into assets from the start. Look for a platform that incorporates DevOps best practices and internal controls into its configuration checks. It should also assess Kubernetes' configuration for a secure posture, so developers can focus on feature delivery.
Bridge DevOps and SecOps
Given no clear role or team is solely responsible for container/Kubernetes security at most organizations, your tooling must bridge teams from Security and Ops to DevOps and Development. To be effective, the platform must have security controls relevant to containerized, Kubernetes environments. It should also assess risk appropriately - telling a developer to fix all 39 vulnerabilities with a CVSS score ≥7 is inefficient. Identifying the 3 deployments exposed to that vulnerability, showing why they're risky, will significantly improve posture.
Other Tips:
Follow least privilege when assigning roles/privileges to users and service accounts to limit attacker ability to gain excessive access if breached. Use specialized tooling to find and remove excessive privileges.
Use defense in depth techniques to hinder lateral movement and data exfiltration by attackers.
Continuously scan manifest files, registries, and clusters for vulnerabilities.
Regularly update cluster software. After vulnerability disclosures, attackers hunt for unpatched clusters. The Log4J vulnerability saw over 840,000 attempted exploits within 72 hours of disclosure.
Conclusion
As a leading DevOps provider, Gart Solutions specializes in helping organizations bolster their Kubernetes security posture and implement robust best practices across the entire cloud-native stack. Our team of seasoned experts can assess your current security risks, vulnerabilities, and misconfigurations, then provide tailored solutions to safeguard your containerized applications and Kubernetes clusters.
Don't leave your business exposed to emerging threats. Reach out to Gart Solutions today to ensure your mission-critical cloud-native infrastructure remains secure and compliant in 2024 and beyond.

At Gart, we recognize the paramount importance of maintaining a secure and compliant environment while harnessing the scalability and agility of cloud infrastructure. This realization has led us to adopt the Policy as Code approach, a transformative methodology that empowers us to define, enforce, and manage policies governing our IT systems and operations through code.
[lwptoc]
In this comprehensive exploration of the Policy as Code approach, we will delve deep into its core principles, practical implementation, and its profound impact on enhancing security and compliance in our DevOps and cloud-centric workflows.
Understanding the Policy as Code Approach
As a DevOps expert and cloud architect deeply entrenched in the ever-evolving world of IT, I've had the privilege of witnessing the transformative power of the Policy as Code approach. It's a paradigm shift that has not only shaped our operations at Gart but is reshaping the industry as a whole. Let's delve into a fundamental understanding of this approach, explore its key principles and benefits, and compare it to traditional policy management methods.
Policy as Code, often abbreviated as PaC, is a contemporary methodology that reimagines the way policies governing IT systems and operations are defined and enforced. At its core, it's about translating these policies into machine-readable code, making them integral to the very fabric of your IT infrastructure. This approach hinges on the use of declarative languages, such as Rego in the case of the popular Open Policy Agent (OPA), to express policies in a manner that computers can understand and apply consistently.
Key Principles and Benefits of Implementing the Policy as Code Approach
Immutable Policies
In the Policy as Code approach, policies are treated as immutable code artifacts. This ensures that policy changes are versioned, tracked, and auditable, aligning with modern DevOps practices.
Automated Enforcement
Automation lies at the heart of PaC. Policies are automatically enforced in the deployment pipeline, reducing the room for human error and ensuring consistent compliance.
Shift-Left Approach
PaC encourages the integration of policy definition and enforcement as early as possible in the software development lifecycle, fostering a "shift-left" culture of security and compliance.
Scalability and Flexibility
With PaC, policies can be dynamically adjusted to adapt to the ever-changing IT landscape, ensuring that they remain relevant and effective.
Enhanced Collaboration
PaC promotes collaboration between development, security, and operations teams, fostering a shared responsibility for policy management.
Audit Trail
Every policy change and enforcement action leaves a clear audit trail, simplifying compliance reporting and incident response.
Real-time Compliance Monitoring
PaC enables real-time monitoring of policy compliance, allowing for immediate remediation of policy violations.
Comparison with Traditional Policy Management Approaches
Traditionally, policy management relied heavily on documentation and manual audits. Traditional approaches were heavily reliant on human interpretation and enforcement, which introduced the potential for errors and inconsistency.
Traditional methods were often reactive, addressing policy violations after they occurred, rather than preventing them in real-time.
As IT environments grew in complexity, manual policy management became increasingly burdensome and prone to oversight.
Traditional methods struggled to scale with the dynamic nature of modern IT operations.
In contrast, the Policy as Code approach addresses these limitations by codifying policies, automating enforcement, and aligning with the principles of DevOps. It's a paradigm shift that empowers organizations to embrace security and compliance as integral components of their IT infrastructure, driving efficiency, consistency, and resilience in an ever-evolving digital landscape.
Compliance Policies as a Prime Use Case for Policy as Code (PaC)
The Policy as Code approach is a versatile framework that can be tailored to a wide range of use cases. It not only bolsters security and compliance but also enhances the reliability and efficiency of IT operations, especially when integrated seamlessly with Infrastructure as Code practices.
Industry-Specific Standards (e.g., PCI DSS, NIST)
Different industries have unique compliance standards. Whether it's the Payment Card Industry Data Security Standard (PCI DSS) for financial services or the National Institute of Standards and Technology (NIST) framework for cybersecurity, Policy as Code provides a structured approach to implementing and maintaining these standards. It allows organizations to stay compliant while also simplifying audit processes.
Regulatory Compliance (e.g., GDPR, HIPAA)
Adhering to ever-evolving regulatory mandates like GDPR and HIPAA is a complex endeavor. Policy as Code simplifies compliance by translating these regulations into executable code. This ensures that data handling practices, consent management, and security controls comply with legal requirements, reducing the risk of non-compliance fines and penalties.
? Here's a short example of Policy as Code (PaC) for HIPAA compliance based on the case study of CI/CD Pipelines and Infrastructure for an E-Health Platform
In the context of our E-Health Platform project, ensuring compliance with HIPAA regulations is of paramount importance to protect patient health information (PHI). To achieve this, we've implemented Policy as Code (PaC) to codify and enforce key HIPAA compliance policies within our CI/CD pipelines and infrastructure.
Policy 1: Access Control for PHI
package hipaa_policies
deny[msg] {
input.resource == "PHI"
input.user.role != "Authorized"
msg = "Unauthorized access to PHI detected."
}
This policy ensures that only authorized users with the appropriate role can access PHI. If an unauthorized user attempts to access PHI, this policy will deny access and generate an alert.
Policy 2: Encryption of PHI in Transit
package hipaa_policies
deny[msg] {
input.resource == "PHI"
not input.data.is_encrypted
msg = "Unencrypted transmission of PHI detected."
}
This policy checks that PHI is always transmitted in an encrypted form. If unencrypted transmission is detected, it triggers a denial and notification.
Policy 3: Data Masking for Dev and Test Environments
package hipaa_policies
deny[msg] {
input.environment == "Dev"
input.resource == "PHI"
not input.data.is_masked
msg = "Unmasked PHI in Dev environment violates HIPAA compliance."
}
In compliance with HIPAA standards, this policy mandates data masking for PHI in non-production environments (Dev and Test). If unmasked PHI is found in these environments, it will be flagged as non-compliant.
Infrastructure as Code (IaC) and its Synergy with the Policy as Code Approach
Infrastructure as Code (IaC) is the practice of defining and managing infrastructure through code. PaC and IaC are natural allies, and their synergy unlocks powerful capabilities:
Consistent Infrastructure Policies
PaC can be used to define and enforce policies for infrastructure resources created through IaC. For example, you can ensure that all cloud instances have encryption enabled or that specific security groups are applied uniformly.
Automated Remediation
PaC can automatically remediate policy violations in the infrastructure. If an IaC deployment violates a security policy, PaC can detect it and trigger corrective actions, minimizing manual intervention.
Policy-Driven Scaling
When combined, PaC and IaC enable policy-driven scaling. For instance, policies can dictate auto-scaling rules based on resource utilization, ensuring infrastructure adapts to demand while adhering to security and compliance requirements.
Harnessing Policy as Code (PaC) for Security Policies
Access Control: In the modern digital landscape, controlling who has access to critical resources is paramount. Policy as Code allows organizations to codify access control policies, defining who can access what resources and under what conditions. This fine-grained control minimizes the risk of unauthorized access and data breaches.
Authentication and Authorization: Policy as Code extends its reach to authentication and authorization processes. Through code, organizations can specify how users authenticate, what actions they're authorized to perform, and enforce these policies consistently across their IT ecosystem.
Data Protection: Protecting sensitive data is a top priority for organizations. PaC enables the creation of policies that govern data protection, ensuring encryption, masking, or redaction of sensitive information in accordance with regulatory requirements and internal security standards.
Tools and Technologies for the Policy as Code Approach
When diving into the world of Policy as Code (PaC), understanding the tools that enable its implementation is crucial. PaC tools provide the framework and engine for defining, enforcing, and managing policies as code. Here's a brief introduction to some of the popular PaC tools:
Open Policy Agent (OPA): OPA is an open-source, general-purpose policy engine that has become a cornerstone of PaC. It uses a policy language called Rego to define policies and is highly extensible, making it suitable for a wide range of use cases.
Rego is a declarative policy language used with OPA. It allows you to express complex policies in a readable and maintainable manner. Rego policies are easy to version control, test, and integrate into various systems.
Developed by HashiCorp, Sentinel is a policy as code framework designed specifically for their infrastructure provisioning tool, Terraform. It enables users to define and enforce policies to ensure infrastructure compliance and security.
One of the strengths of Policy as Code is its compatibility with infrastructure provisioning tools like Terraform and Kubernetes. Integrating PaC with these tools enhances the control and security of infrastructure deployments:
PaC can be integrated into Terraform pipelines using tools like Sentinel to enforce policies during infrastructure provisioning. This ensures that infrastructure configurations align with defined policies before deployment.
Kubernetes supports PaC through tools like OPA Gatekeeper. With Gatekeeper, you can validate Kubernetes configurations against policies before they are applied, preventing misconfigurations and security risks.
Policy as Code (PaC) for CI/CD
In the world of modern software development and deployment, Continuous Integration/Continuous Deployment (CI/CD) pipelines are at the heart of efficient and rapid software delivery. Here, we explore how the Policy as Code approach seamlessly integrates with CI/CD workflows, enhancing security and compliance while streamlining the development process.
Key Benefits of PaC for CI/CD
Automated Compliance
PaC allows organizations to automate compliance checks at every stage of the CI/CD pipeline. This ensures that software and infrastructure adhere to security and regulatory standards without manual intervention.
Real-time Policy Validation
PaC tools provide real-time validation of policies, allowing issues to be detected and addressed immediately, reducing the risk of security vulnerabilities or compliance violations going unnoticed.
Policy as Code Templates
PaC enables the creation of reusable policy templates, making it easier to enforce consistent policies across different projects and environments.
Shift-Left Security
PaC encourages a "shift-left" approach to security and compliance, where policy checks are integrated into the early stages of development. This reduces the likelihood of costly issues arising later in the pipeline.
Audit Trail
PaC maintains a comprehensive audit trail, providing visibility into policy enforcement, violations, and remediation actions. This documentation is invaluable for compliance reporting and audits.
Different stages of the deployment pipeline require unique policy checks to ensure that software is developed, tested, and deployed securely and in compliance with organizational standards. We delve into the importance of policy enforcement at each stage of the pipeline.

The NIS2 (Network and Information Security Directive) is a comprehensive directive that mandates organizations to implement robust security measures and document compliance to protect critical assets and ensure community continuity.
For organizations subject to NIS2 requirements, CISOs, and IT security officers must ensure robust internal compliance preparedness.
Why NIS2 Compliance Matters
NIS2 aims to enhance the overall level of cybersecurity in the EU by:
Improving the resilience of critical infrastructure.
Enhancing the security of network and information systems.
Ensuring rapid response to and recovery from cyber incidents.
For organizations subject to NIS2 requirements, compliance is not just a legal obligation but a vital component of risk management and operational continuity. Failing to comply can result in significant financial penalties, reputational damage, and operational disruptions.
Who is affected by NIS2?
NIS2 affects all big organizations that work in the European Union and are considered important to society. This includes organizations that:
Have 50 or more employees, or
Make over €10 million in revenue each year
NIS2 puts these organizations into two groups:
Essential organizations - These are very important sectors like energy, healthcare, transportation, and water supply.
Important organizations - These are sectors like manufacturing, food production, waste management, and postal services.
So in simple terms, if your fairly large organization operates in the EU and provides crucial services or products to society, then NIS2 applies to you. The directive aims to ensure these vital entities have strong cybersecurity measures in place.
The penalties for not following NIS2 rules are different depending on whether an organization is labeled as "essential" or "important".
For essential organizations:
They can be fined up to €10 million, or
They can be fined at least 2% of their total worldwide revenue from the previous year, whichever amount is higher.
For important organizations:
They can be fined up to €7 million, or
They can be fined at least 1.4% of their total worldwide revenue from the previous year, whichever amount is higher.
Gart’s NIS2 Solution
Gart offers a solution that simplifies the complexity of NIS2 compliance. The solution provides a systematic approach tailored to your ongoing operations and compliance efforts. By adopting Gart’s solution, you gain access to:
A systematic compliance framework for analyzing and documenting the security of critical assets.
Assurance of effective compliance work throughout your organization, aligned with good security practices and NIS2 requirements by applying ISO/EIC 27001/2 security principles.
Use of questionnaires to review the directive's requirements and ensure all documentation requirements are met, preparing you for audits.
Clear guidance on how to register significant security incidents with CSIRT, ensuring a proactive approach.
Read more: Gart’s Expertise in ISO 27001 Compliance Empowers Spiral Technology for Seamless Audits and Cloud Migration
How Does Gart Solution Support NIS2 Compliance?
NIS2 Requirement 1: Have policies for analyzing risks and information security
Gart can find and evaluate all assets, systems, weaknesses, and cyber/operational risks in critical infrastructure environments. It uses this detailed visibility to automatically create and enforce network security policies that reduce exposure to those identified risks.
In simple terms, Gart's solution allows organizations to:
Discover all their critical assets, systems, and potential vulnerabilities
Assess the cyber and operational risks in their environments
Automatically define security policies to protect against those risks
Enforce those security policies across their networks
NIS2 Requirement 2: Dealing with Security Incidents
Gart Solutions constantly keeps watch over all critical infrastructure systems for any signs of potential threats, both known and new. It analyzes all security alerts in detail to prioritize the most important issues. Gart also integrates with existing security tools like SIEM and SOAR to extend an organization's security processes across all of its critical systems.
In simpler terms, Gart's solution allows organizations to:
Continuously monitor all their vital systems and networks
Quickly detect any potential cyber threats, even new unidentified ones
Understand the context and importance of every security alert
Work seamlessly with their existing security tools and workflows
Expand their incident response capabilities to cover all critical infrastructure
NIS2 Requirement 3: Managing Crises
Gart provides:
A complete, up-to-date list of all critical systems
Logging of all changes and unusual activity in assets and networks
Ability to create and enforce security policies to separate networks and control access
Ready integration with backup and recovery tools
All of these capabilities from Gart help organizations improve their overall crisis management and ensure the continuity of essential operations.
In simpler terms, Gart's solution allows organizations to:
Know exactly what critical assets they have at all times
Track all activity so they can investigate incidents
Lock down systems by enforcing strict security controls
Quickly backup and restore systems if needed
NIS2 Requirement 4: Security of Networks and Information Systems
By utilizing Gart's capabilities, customers can effectively:
Identify vulnerabilities and insecure configurations in their critical networks and systems
Assess and manage the cyber risks to their operational environments
Allow remote access for personnel to do their work securely
In simple terms, Gart helps organizations implement robust security measures for their networks and information systems as required by NIS2. This includes finding and fixing vulnerabilities, evaluating risks, and controlling access - all crucial for securing vital operational technology.
NIS2 Requirement 5: Basic Cybersecurity Practices and Training
Gart's solution helps organizations:
Identify areas where they need to improve their basic cybersecurity habits and procedures based on risk assessments.
Ensure all personnel, whether employees or vendors, follow proper access controls, password management, and other essential cybersecurity practices.
Use the recommendations to develop training programs to raise cybersecurity awareness and skills.
NIS2 Requirement 6: Policies and Procedures for Data Encryption
Gart provides:
1) Encryption of all user data, critical system data, and other sensitive information in compliance with NIS2, GDPR, and other regulations.
2) Alerts when sensitive data like personal health records is being processed in a way that violates security policies or could lead to a data breach.
Here's a rewording in simple language:
NIS2 Requirement 7: Using Multi-Factor Authentication and Secure Communications
Gart helps organizations:
- Enforce strong access controls like multi-factor authentication across their workforce and supply chain vendors/partners
- Allow only authorized and verified personnel to access critical systems remotely or on-site
- Ensure all communications to operational technology are fully secured
- Meet audit requirements by recording all access sessions
Get a sample of IT Audit
Sign up now
Get on email
Loading...
Thank you!
You have successfully joined our subscriber list.
Key Features:
Mapping of Critical Assets
We will create an overview of the various types of critical assets within your value chain and document their security levels.
Risk Assessment of Critical Assets, Systems, and Processes
We will conduct a risk assessment based on the current threat landscape, the assets' placement within the value chain, and their potential societal consequences.
GAP Analysis
We will obtain a clear overview of your current compliance level and implementation, identifying the essential control objectives required for NIS2.
Automated Processes
We will automate control follow-ups and communication with internal stakeholders to ensure all relevant tasks are carried out correctly and on time.
Compliance Control and Scope of SoA
We will begin with an initial compliance review, prioritize, and scope the Statement of Applicability (SoA) based on NIS2 requirements.
Create Awareness and Communicate Directly with Stakeholders
We will create awareness and directly communicate with stakeholders to keep everyone informed about policy and procedural changes, ensuring everyone understands their role.
Overview of Reporting to CSIRT
We will establish a process for reporting significant incidents and threats to the organization or its supply chain to CSIRT, protecting critical assets quickly and efficiently.
Ongoing Auditing
We will document internal compliance with NIS2 via dedicated management controls and functionality for auditing critical suppliers.
About the NIS2 Directive or NIS2 framework
The NIS 2 Directive, also referred to as the NIS2 framework, is a European Union regulation aimed at enhancing cybersecurity across the bloc. Here's a breakdown of the key points:
Goals:
Improve overall cybersecurity posture in the EU.
Strengthen existing cybersecurity measures in critical sectors.
Ensure a consistent approach to cybersecurity risk management across member states.
Key Features:
Broader Scope: NIS2 applies to a wider range of sectors compared to the previous NIS Directive. This includes essential services (energy, transport, water, etc.) and important entities in sectors like waste management, postal services, manufacturing, and more.
Enhanced Risk Management: Organizations must implement robust cybersecurity measures to manage risks to their network and information systems. This includes measures to prevent incidents, minimize their impact, and report them effectively.
Incident Reporting: Entities are required to report significant incidents to relevant authorities. This allows for faster response and improved coordination across member states.
Supply Chain Security: The directive emphasizes the importance of supply chain security. Organizations need to consider the cybersecurity risks associated with their suppliers and vendors.
Cooperation and Information Sharing: Increased cooperation and information sharing among member states and relevant authorities are crucial aspects of NIS2.
Current Status:
Adopted in December 2022 and came into effect in January 2023.
EU member states have until October 17, 2024 to transpose the NIS2 Directive into national law.
By April 17, 2025, member states need to establish a list of essential entities falling under the directive.
NIS2-Compliance-Checklist-A-Comprehensive-Guide-to-Audit_Free-PDFDownload
Conclusion
The European Union's Network and Information Security Directive, known as NIS2, sets stringent requirements for organizations to safeguard their critical assets and ensure the continuity of essential services.
Gart is here to guide you through every step of the process, providing the expertise, tools, and support you need to achieve and maintain compliance. With our systematic approach, you can focus on your core business operations, confident that your information security is in capable hands.
Are you ready to simplify your NIS2 compliance journey? Contact Gart today to learn more about how we can help you strengthen your information security and achieve regulatory compliance with ease.