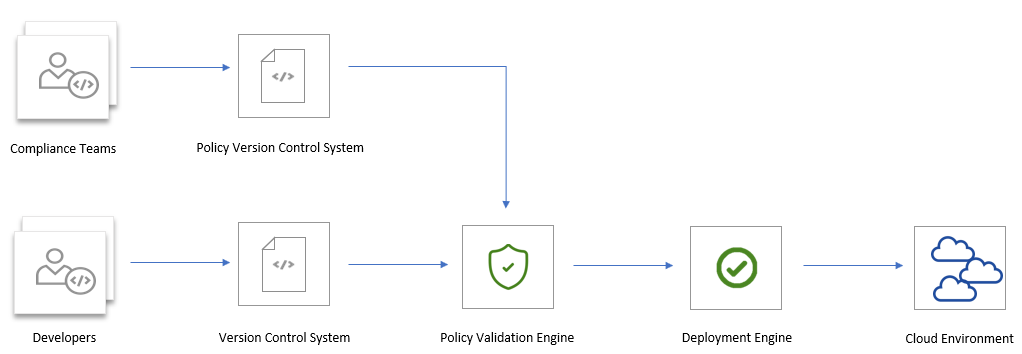
At Gart, we recognize the paramount importance of maintaining a secure and compliant environment while harnessing the scalability and agility of cloud infrastructure. This realization has led us to adopt the Policy as Code approach, a transformative methodology that empowers us to define, enforce, and manage policies governing our IT systems and operations through code.
- Understanding the Policy as Code Approach
- Key Principles and Benefits of Implementing the Policy as Code Approach
- Comparison with Traditional Policy Management Approaches
- Compliance Policies as a Prime Use Case for Policy as Code (PaC)
- Infrastructure as Code (IaC) and its Synergy with the Policy as Code Approach
- Harnessing Policy as Code (PaC) for Security Policies
- Tools and Technologies for the Policy as Code Approach
- Policy as Code (PaC) for CI/CD
In this comprehensive exploration of the Policy as Code approach, we will delve deep into its core principles, practical implementation, and its profound impact on enhancing security and compliance in our DevOps and cloud-centric workflows.
Understanding the Policy as Code Approach
As a DevOps expert and cloud architect deeply entrenched in the ever-evolving world of IT, I’ve had the privilege of witnessing the transformative power of the Policy as Code approach. It’s a paradigm shift that has not only shaped our operations at Gart but is reshaping the industry as a whole. Let’s delve into a fundamental understanding of this approach, explore its key principles and benefits, and compare it to traditional policy management methods.
Policy as Code, often abbreviated as PaC, is a contemporary methodology that reimagines the way policies governing IT systems and operations are defined and enforced. At its core, it’s about translating these policies into machine-readable code, making them integral to the very fabric of your IT infrastructure. This approach hinges on the use of declarative languages, such as Rego in the case of the popular Open Policy Agent (OPA), to express policies in a manner that computers can understand and apply consistently.
Key Principles and Benefits of Implementing the Policy as Code Approach
Immutable Policies
In the Policy as Code approach, policies are treated as immutable code artifacts. This ensures that policy changes are versioned, tracked, and auditable, aligning with modern DevOps practices.
Automated Enforcement
Automation lies at the heart of PaC. Policies are automatically enforced in the deployment pipeline, reducing the room for human error and ensuring consistent compliance.
Shift-Left Approach
PaC encourages the integration of policy definition and enforcement as early as possible in the software development lifecycle, fostering a “shift-left” culture of security and compliance.
Scalability and Flexibility
With PaC, policies can be dynamically adjusted to adapt to the ever-changing IT landscape, ensuring that they remain relevant and effective.
Enhanced Collaboration
PaC promotes collaboration between development, security, and operations teams, fostering a shared responsibility for policy management.
Audit Trail
Every policy change and enforcement action leaves a clear audit trail, simplifying compliance reporting and incident response.
Real-time Compliance Monitoring
PaC enables real-time monitoring of policy compliance, allowing for immediate remediation of policy violations.
Comparison with Traditional Policy Management Approaches
Traditionally, policy management relied heavily on documentation and manual audits. Traditional approaches were heavily reliant on human interpretation and enforcement, which introduced the potential for errors and inconsistency.
Traditional methods were often reactive, addressing policy violations after they occurred, rather than preventing them in real-time.
As IT environments grew in complexity, manual policy management became increasingly burdensome and prone to oversight.
Traditional methods struggled to scale with the dynamic nature of modern IT operations.
In contrast, the Policy as Code approach addresses these limitations by codifying policies, automating enforcement, and aligning with the principles of DevOps. It’s a paradigm shift that empowers organizations to embrace security and compliance as integral components of their IT infrastructure, driving efficiency, consistency, and resilience in an ever-evolving digital landscape.
Compliance Policies as a Prime Use Case for Policy as Code (PaC)
The Policy as Code approach is a versatile framework that can be tailored to a wide range of use cases. It not only bolsters security and compliance but also enhances the reliability and efficiency of IT operations, especially when integrated seamlessly with Infrastructure as Code practices.
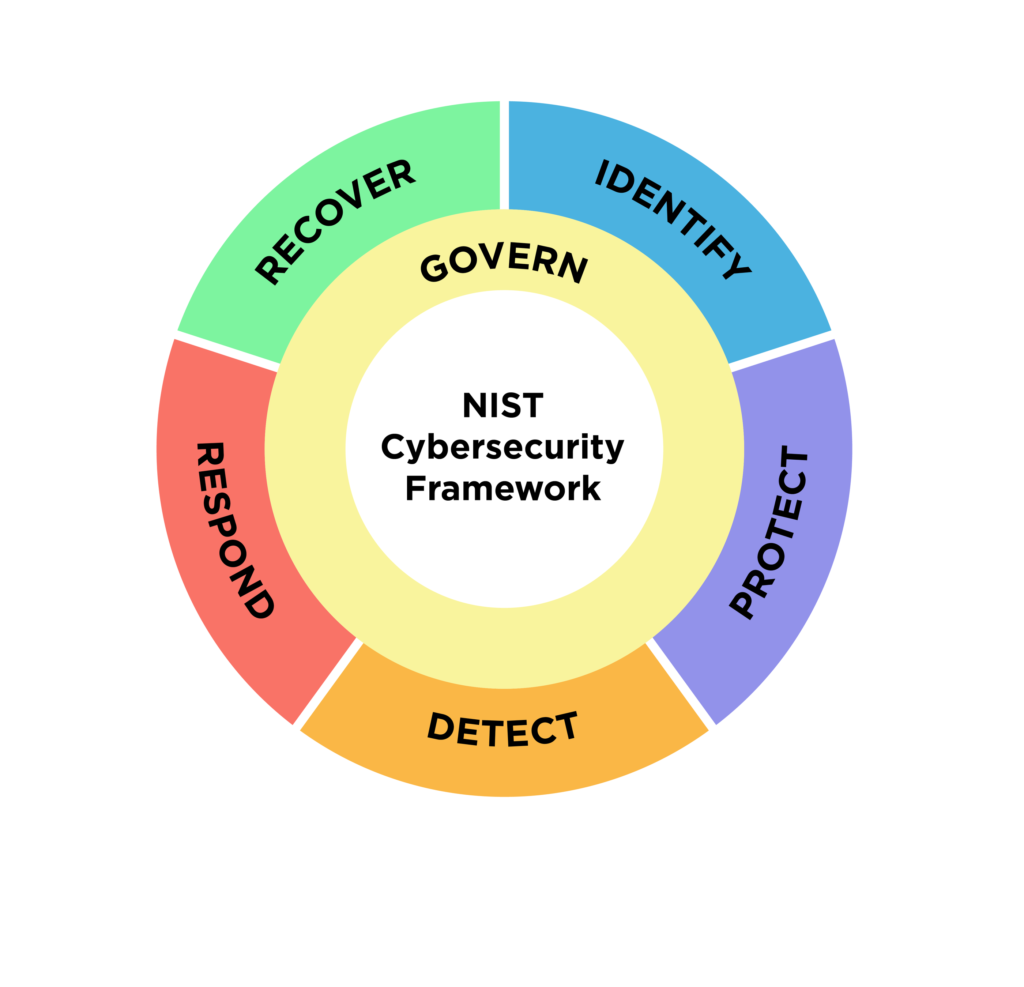
Industry-Specific Standards (e.g., PCI DSS, NIST)
Different industries have unique compliance standards. Whether it’s the Payment Card Industry Data Security Standard (PCI DSS) for financial services or the National Institute of Standards and Technology (NIST) framework for cybersecurity, Policy as Code provides a structured approach to implementing and maintaining these standards. It allows organizations to stay compliant while also simplifying audit processes.
Regulatory Compliance (e.g., GDPR, HIPAA)
Adhering to ever-evolving regulatory mandates like GDPR and HIPAA is a complex endeavor. Policy as Code simplifies compliance by translating these regulations into executable code. This ensures that data handling practices, consent management, and security controls comply with legal requirements, reducing the risk of non-compliance fines and penalties.
? Here’s a short example of Policy as Code (PaC) for HIPAA compliance based on the case study of CI/CD Pipelines and Infrastructure for an E-Health Platform
In the context of our E-Health Platform project, ensuring compliance with HIPAA regulations is of paramount importance to protect patient health information (PHI). To achieve this, we’ve implemented Policy as Code (PaC) to codify and enforce key HIPAA compliance policies within our CI/CD pipelines and infrastructure.

Policy 1: Access Control for PHI
package hipaa_policies
deny[msg] {
input.resource == "PHI"
input.user.role != "Authorized"
msg = "Unauthorized access to PHI detected."
}
This policy ensures that only authorized users with the appropriate role can access PHI. If an unauthorized user attempts to access PHI, this policy will deny access and generate an alert.
Policy 2: Encryption of PHI in Transit
package hipaa_policies
deny[msg] {
input.resource == "PHI"
not input.data.is_encrypted
msg = "Unencrypted transmission of PHI detected."
}
This policy checks that PHI is always transmitted in an encrypted form. If unencrypted transmission is detected, it triggers a denial and notification.
Policy 3: Data Masking for Dev and Test Environments
package hipaa_policies
deny[msg] {
input.environment == "Dev"
input.resource == "PHI"
not input.data.is_masked
msg = "Unmasked PHI in Dev environment violates HIPAA compliance."
}
In compliance with HIPAA standards, this policy mandates data masking for PHI in non-production environments (Dev and Test). If unmasked PHI is found in these environments, it will be flagged as non-compliant.
Infrastructure as Code (IaC) and its Synergy with the Policy as Code Approach
Infrastructure as Code (IaC) is the practice of defining and managing infrastructure through code. PaC and IaC are natural allies, and their synergy unlocks powerful capabilities:
Consistent Infrastructure Policies
PaC can be used to define and enforce policies for infrastructure resources created through IaC. For example, you can ensure that all cloud instances have encryption enabled or that specific security groups are applied uniformly.
Automated Remediation
PaC can automatically remediate policy violations in the infrastructure. If an IaC deployment violates a security policy, PaC can detect it and trigger corrective actions, minimizing manual intervention.
Policy-Driven Scaling
When combined, PaC and IaC enable policy-driven scaling. For instance, policies can dictate auto-scaling rules based on resource utilization, ensuring infrastructure adapts to demand while adhering to security and compliance requirements.
Harnessing Policy as Code (PaC) for Security Policies
- Access Control: In the modern digital landscape, controlling who has access to critical resources is paramount. Policy as Code allows organizations to codify access control policies, defining who can access what resources and under what conditions. This fine-grained control minimizes the risk of unauthorized access and data breaches.
- Authentication and Authorization: Policy as Code extends its reach to authentication and authorization processes. Through code, organizations can specify how users authenticate, what actions they’re authorized to perform, and enforce these policies consistently across their IT ecosystem.
- Data Protection: Protecting sensitive data is a top priority for organizations. PaC enables the creation of policies that govern data protection, ensuring encryption, masking, or redaction of sensitive information in accordance with regulatory requirements and internal security standards.
Tools and Technologies for the Policy as Code Approach
When diving into the world of Policy as Code (PaC), understanding the tools that enable its implementation is crucial. PaC tools provide the framework and engine for defining, enforcing, and managing policies as code. Here’s a brief introduction to some of the popular PaC tools:
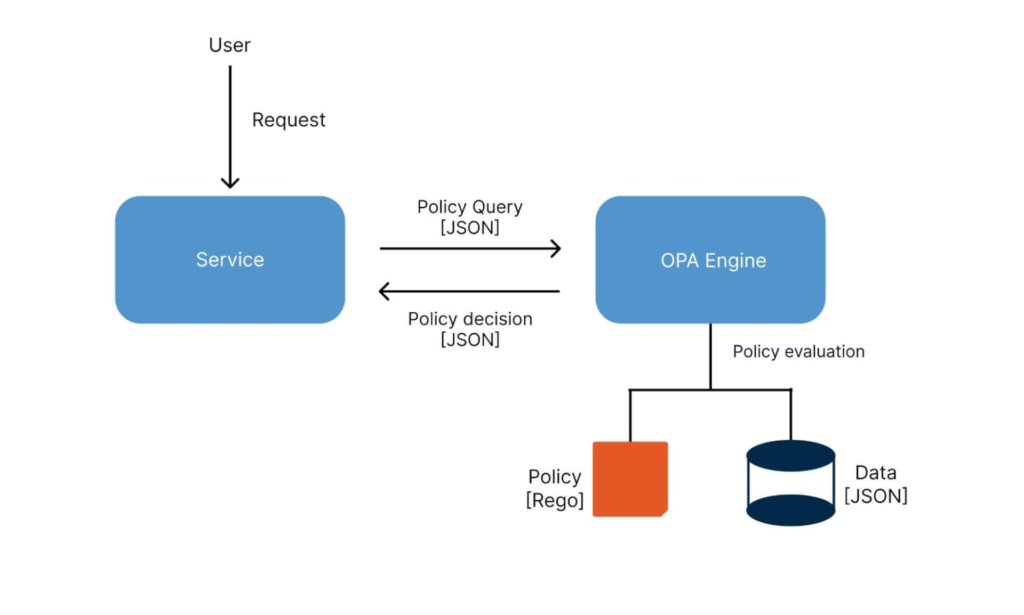
Open Policy Agent (OPA): OPA is an open-source, general-purpose policy engine that has become a cornerstone of PaC. It uses a policy language called Rego to define policies and is highly extensible, making it suitable for a wide range of use cases.
Rego is a declarative policy language used with OPA. It allows you to express complex policies in a readable and maintainable manner. Rego policies are easy to version control, test, and integrate into various systems.
Developed by HashiCorp, Sentinel is a policy as code framework designed specifically for their infrastructure provisioning tool, Terraform. It enables users to define and enforce policies to ensure infrastructure compliance and security.
One of the strengths of Policy as Code is its compatibility with infrastructure provisioning tools like Terraform and Kubernetes. Integrating PaC with these tools enhances the control and security of infrastructure deployments:
PaC can be integrated into Terraform pipelines using tools like Sentinel to enforce policies during infrastructure provisioning. This ensures that infrastructure configurations align with defined policies before deployment.
Kubernetes supports PaC through tools like OPA Gatekeeper. With Gatekeeper, you can validate Kubernetes configurations against policies before they are applied, preventing misconfigurations and security risks.
Policy as Code (PaC) for CI/CD
In the world of modern software development and deployment, Continuous Integration/Continuous Deployment (CI/CD) pipelines are at the heart of efficient and rapid software delivery. Here, we explore how the Policy as Code approach seamlessly integrates with CI/CD workflows, enhancing security and compliance while streamlining the development process.
Key Benefits of PaC for CI/CD
Automated Compliance
PaC allows organizations to automate compliance checks at every stage of the CI/CD pipeline. This ensures that software and infrastructure adhere to security and regulatory standards without manual intervention.
Real-time Policy Validation
PaC tools provide real-time validation of policies, allowing issues to be detected and addressed immediately, reducing the risk of security vulnerabilities or compliance violations going unnoticed.
Policy as Code Templates
PaC enables the creation of reusable policy templates, making it easier to enforce consistent policies across different projects and environments.
Shift-Left Security
PaC encourages a “shift-left” approach to security and compliance, where policy checks are integrated into the early stages of development. This reduces the likelihood of costly issues arising later in the pipeline.
Audit Trail
PaC maintains a comprehensive audit trail, providing visibility into policy enforcement, violations, and remediation actions. This documentation is invaluable for compliance reporting and audits.
Different stages of the deployment pipeline require unique policy checks to ensure that software is developed, tested, and deployed securely and in compliance with organizational standards. We delve into the importance of policy enforcement at each stage of the pipeline.