The bigger your product and the more people and companies it serves, the more it becomes a juicy target for hackers itching to mess with your infrastructure. They might mess up your system performance or even swipe users’ personal data.
Within the framework of DevOps, there exists DevSecOps, a response to contemporary security challenges while also addressing the need for rapid software development.
In this content, I will elaborate on the importance of DevSecOps, how to assess its relevance for your organization, and the necessary actions to integrate this practice into your company.
What is DevSecOps?
DevSecOps is an approach to product development that integrates security from the very beginning. The main goal is to reduce the number of defects in the final product by addressing security concerns proactively throughout the software development process. Instead of dealing with the consequences of existing issues, the focus is on preventing their occurrence altogether.
It can be likened to planning for a warm house during construction rather than insulating it after realizing it’s too cold. With DevSecOps, the emphasis is on avoiding vulnerabilities and weaknesses in the first place and taking necessary measures at every stage of development to ensure a secure and robust end product.
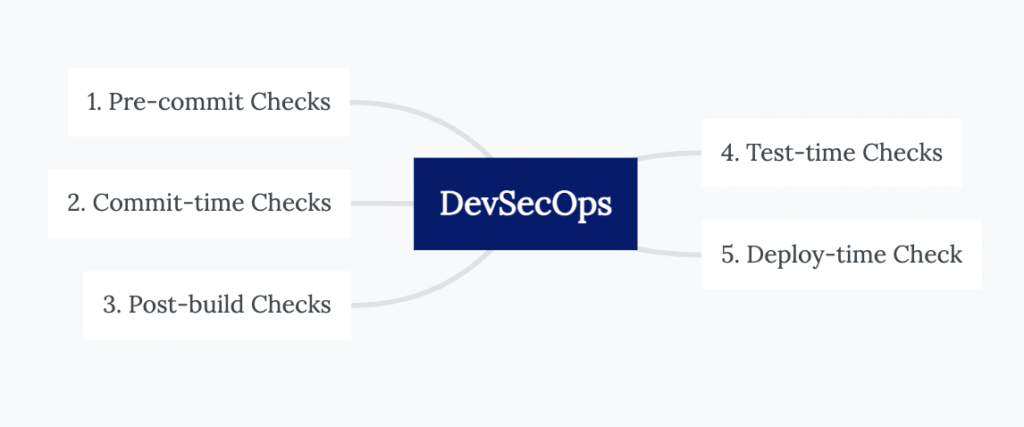
Pre-commit Checks. Code inspection to detect the presence of sensitive information (such as passwords, secrets, tokens, etc.) that should not be included in the Git history.
Commit-time Checks. Checks performed during the commit process to ensure the correctness and security of the code in the repository.
Post-build Checks. Checks carried out after the application has been built, including artifact testing (e.g., docker images).
Test-time Checks. Vulnerability testing of the deployed application (e.g., API scanning for common vulnerabilities).
Deploy-time Checks. Checks performed during the application deployment to assess the infrastructure for vulnerabilities.
A few years ago, DevSecOps was primarily relevant for large companies with numerous products and extensive development teams. However, today, its importance is gradually extending to smaller players in the industry.
Previously, development efforts prioritized swiftly creating a pilot version and dealing with security concerns later. Yet, investors now grasp the significance of airtight security and raise their inquiries. As a result, DevSecOps becomes increasingly relevant for a broader audience. However, for teams with fewer than 50 developers, security concerns may not be as pressing, and they are often handled through simpler, standard methods (in practice). Their main focus is on business functionality, with security addressed in fragments after product creation. Vulnerabilities are often identified in finished products using free scanners and penetration testing, and then remedied. As businesses grow and demand higher quality, security gains paramount importance and becomes deeply ingrained in the development process.
Consequently, companies reach a new level with their unique requirements. The market demands faster responses, driving the significance of the Time To Market metric. This urges the automation of every feasible aspect. Code is written, built, and deployed swiftly, showcasing DevOps in full effect – automating build, delivery, and deployment processes. As the transition to a pipeline-driven development occurs, security becomes a critical concern, leading us to the world of DevSecOps.
What are the Business Benefits?
The advantages for businesses are evident. As development speeds up with business growth, security should also keep pace, preferably taking a proactive approach. This is where DevSecOps becomes invaluable. When security practices are well-established and seamlessly integrated into the pipeline, automation becomes the norm. Detecting and rectifying bugs during the product’s creation phase prevents a cascade of issues in subsequent products, saving significant resources.
Furthermore, meeting investor and client demands for prompt product delivery is crucial. Discovering errors at the final stage can lead to time-consuming fixes, causing delivery delays, contract breaches, and potential penalties. Hence, prioritizing security throughout ensures smoother product development without setbacks.
? Ready to Strengthen Your Application Security? Learn How to Implement DevSecOps Best Practices Today! Contact Us
Security in Software Development
The industry is well acquainted with various practices that aid in ensuring security at different development stages. But what exactly is security? Can there be a scenario where no vulnerabilities exist? Unfortunately, the notion of being entirely free of vulnerabilities is implausible, given the constant emergence of new ones and the vigilance of security researchers. Thus, the primary objective is to minimize the number of “holes,” swiftly detecting and rectifying them before malicious actors exploit them.
To achieve this goal, the implementation of security practices becomes vital. Drawing an analogy with an automotive assembly line, we can better understand the importance of security throughout the development process.
During the blueprint phase, which is akin to the design stage in software development, we assess the software’s architecture for correctness, authentication elements, database integration, and appropriate platform selection.
As we proceed to the parts stage, which corresponds to the integration of third-party libraries, we must ensure their functionality and check for any vulnerabilities or licensing issues.
The framework phase mirrors the creation of our own code, where we adhere to secure coding practices, prioritize data protection, and encryption.
The installation of parts phase relates to the assembly of the software, allowing us to conduct basic dynamic tests, verifying assembly correctness and library usage.
Subsequently, in the testing stage, we perform comprehensive tests to observe how the software functions in its infrastructure and interacts with users.
Finally, the production phase marks the product’s release to the world, where constant monitoring ensures its performance under real-world conditions.
Throughout each development stage, security should be thoroughly evaluated, much like checking for installed airbags, a functioning steering wheel, a key for the door, working seatbelts, and appropriate brakes in a car.
Conducting timely and continuous checks at each stage is essential to ensure security is ingrained within the development process, avoiding last-minute fixes and mitigating potential risks.
The Path of Application Security Practices Transformation
Application Security has gained widespread acceptance as a mainstream concern in the cybersecurity landscape. The evolving market demands more innovative and efficient solutions, especially with the rise in API attacks and software supply chain vulnerabilities. As technology advances and market requirements change, new tools and modifications in the cybersecurity toolkit are emerging. To understand the current trends and the level of development in cybersecurity tools, we can refer to the Gartner Hype Cycle for Application Security, 2023 report.
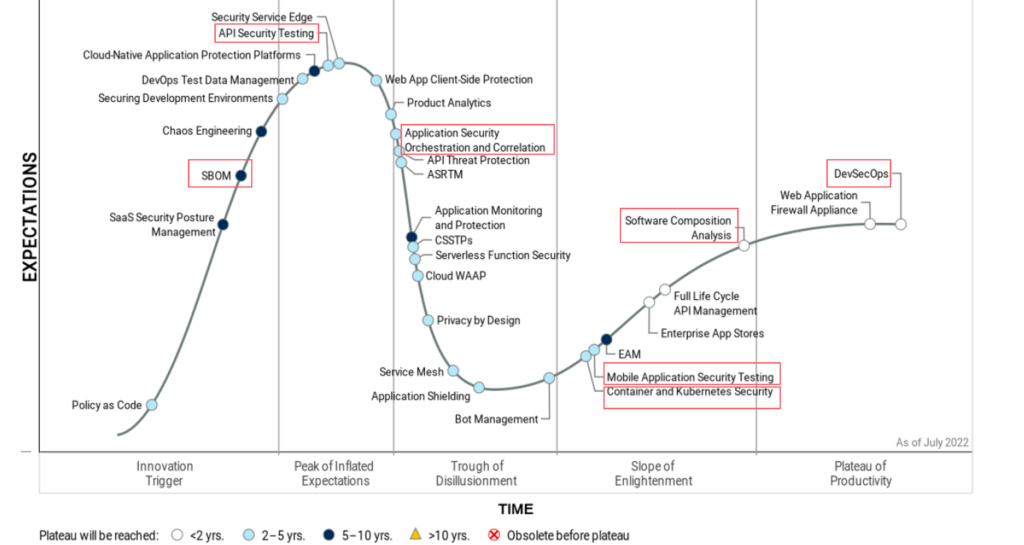
The cycle comprises five distinct phases:
- Innovation Trigger: This phase marks the introduction of technologies in the cybersecurity domain, just starting their journey.
- Peak of Inflated Expectations: Technologies in this phase demonstrate some successful use cases but also experience setbacks. Companies strive to tailor these practices to their specific needs, but widespread adoption is yet to be achieved.
- Trough of Disillusionment: Interest in technologies of this phase begins to decline as their implementation doesn’t always yield desired results.
- Slope of Enlightenment: At this stage, technologies have a solid track record of being beneficial to companies, leading to new generations of tools and an increase in demand.
- Plateau of Productivity: In this final stage, technologies have well-defined tasks and applications, gaining momentum as mainstream cybersecurity solutions.
Now, let’s explore DevSecOps and delve into the most impactful and compelling secure development practices, considering their implications on businesses, technological complexities, and geopolitical implications.
DevSecOps in the Current Landscape
As per Gartner’s assessment, DevSecOps has reached the “Plateau of Productivity” phase. It has now become a mature mainstream approach, adopted by over 50% of the target audience. This methodology allows security teams to stay in sync with development and operations units during the creation of modern applications. The model ensures seamless integration of security tools into DevOps and automates all processes involved in developing secure software. Consequently, DevSecOps aids businesses in elevating product security, aligning applications and processes with industrial and regulatory standards, reducing vulnerability remediation costs, improving Time-to-Market metrics, and enhancing developers’ expertise.
While striving to establish an effective secure development process, companies face several challenges:
- Improper implementation of AppSec practices and poorly structured security processes can create a contradiction with DevOps, leading developers to perceive security tools as hindrances to their work.
- The wide variety of tools used in modern CI/CD pipelines complicates the smooth integration of DevSecOps.
- Many developers lack expertise in security, resulting in a lack of understanding of potential risks in their code. They may be hesitant to leave the CI/CD pipeline for security testing or scan results and may encounter difficulties with false positives from SAST and DAST tools.
- Open-source security solutions may contain malicious code, and there is a risk that such tools may become unavailable for Russian users at any moment.
Despite these challenges, implementing DevSecOps can greatly benefit organizations by enhancing their security practices and ensuring the safety and compliance of their applications and processes.
Practices of DevSecOps in the Context of Modern Challenges
- SCA (Software Composition Analysis): SCA involves analyzing the components and dependencies in software applications to identify and address vulnerabilities in third-party libraries or open-source code. With the increasing use of external libraries, SCA helps ensure that potential security risks from these components are mitigated.
- MAST (Mobile Application Security Testing): MAST focuses on evaluating the security of mobile applications across various platforms. It involves conducting comprehensive security assessments to identify weaknesses and vulnerabilities specific to mobile app development.
- Container Security: Containerization has become prevalent in modern application deployment. Container Security practices involve scanning container images for potential security flaws and continuously monitoring container runtime environments to prevent unauthorized access and data breaches.
- ASOC (Application Security Orchestration & Correlation): ASOC is about streamlining and automating security practices throughout the software development lifecycle. It includes integrating various security tools, orchestrating their actions, and correlating their findings to improve the efficiency and effectiveness of security assessments.
- API Security Testing: With the increasing use of APIs in modern applications, API security testing is crucial. It involves evaluating the security of APIs, ensuring they are protected against potential attacks, and safeguarding sensitive data exchanged through these interfaces.
- Securing Development Environments: Securing development environments involves implementing robust security measures to protect the tools, platforms, and repositories used by developers during the software development process. This ensures that the codebase remains secure from the very beginning.
- Chaos Engineering: Chaos Engineering is a proactive approach to testing system resilience. It involves simulating real-world scenarios and failures to identify potential weaknesses in applications and infrastructure and enhance their overall resilience.
- SBOM (Software Bill of Materials): SBOM is a detailed inventory of all software components used in an application. It helps organizations track and manage their software supply chain, facilitating vulnerability management and risk assessment.
- Policy-as-a-Code: Policy-as-a-Code involves codifying security policies and compliance requirements into the software development process. By integrating policy checks into the CI/CD pipeline, organizations can ensure that applications adhere to security standards and regulatory guidelines.
- RBAC stands for Role-Based Access Control, a method of restricting system access based on user roles. In CI/CD pipelines, RBAC ensures that only authorized individuals have access to specific stages of the pipeline, enhancing security and control.
Implementing these DevSecOps practices can significantly enhance application security, address modern challenges, and foster a proactive approach to safeguarding software throughout its lifecycle.
Triggers for Implementation and Recommendations
Knowing when to prioritize the security of your products and embark on serious DevSecOps implementation can be a crucial decision. It depends on your industry, market position, and the demands of your audience. Compliance with regulators and the assessment of potential risks act as significant drivers for security. DevSecOps has become a mature mainstream technology embraced by over 50% of the target audience. It enables security teams to align with development and operations units, fostering the creation of modern applications. Deep integration of security tools into DevOps and automation of secure software development processes help businesses elevate product security levels, comply with industry standards, reduce vulnerability fixing costs, improve Time-to-Market metrics, and enhance developer expertise.
Several triggers can prompt the adoption of DevSecOps practices:
- A development team comprising more than 50 members.
- The implementation of process automation in development, such as CI/CD and DevOps.
- An emphasis on microservices architecture.
- The need for post-implementation improvements in application security practices.
For companies with large development teams and multiple products, introducing DevSecOps should be a gradual process, involving the team in decision-making. Though initial challenges may arise, once the process functions efficiently, developers, other team members, investors, and stakeholders will recognize the benefits of these changes.
Before proceeding, it’s wise to seek guidance from successful implementations, consult with experts, and evaluate the advantages gained by companies that have already adopted DevSecOps, making informed decisions backed by data.
Empower your team with DevOps excellence! Streamline workflows, boost productivity, and fortify security. Let’s shape the future of your software development together – inquire about our DevOps Consulting Services.









