By treating infrastructure as software code, IaC empowers teams to leverage the benefits of version control, automation, and repeatability in their cloud deployments.
This article explores the key concepts and benefits of IaC, shedding light on popular tools such as Terraform, Ansible, SaltStack, and Google Cloud Deployment Manager. We’ll delve into their features, strengths, and use cases, providing insights into how they enable developers and operations teams to streamline their infrastructure management processes.
IaC Tools Comparison Table
| IaC Tool | Description | Supported Cloud Providers |
| Terraform | Open-source tool for infrastructure provisioning | AWS, Azure, GCP, and more |
| Ansible | Configuration management and automation platform | AWS, Azure, GCP, and more |
| SaltStack | High-speed automation and orchestration framework | AWS, Azure, GCP, and more |
| Puppet | Declarative language-based configuration management | AWS, Azure, GCP, and more |
| Chef | Infrastructure automation framework | AWS, Azure, GCP, and more |
| CloudFormation | AWS-specific IaC tool for provisioning AWS resources | Amazon Web Services (AWS) |
| Google Cloud Deployment Manager | Infrastructure management tool for Google Cloud Platform | Google Cloud Platform (GCP) |
| Azure Resource Manager | Azure-native tool for deploying and managing resources | Microsoft Azure |
| OpenStack Heat | Orchestration engine for managing resources in OpenStack | OpenStack |
Exploring the Landscape of IaC Tools
The IaC paradigm is widely embraced in modern software development, offering a range of tools for deployment, configuration management, virtualization, and orchestration. Prominent containerization and orchestration tools like Docker and Kubernetes employ YAML to express the desired end state. HashiCorp Packer is another tool that leverages JSON templates and variables for creating system snapshots.
The most popular configuration management tools, namely Ansible, Chef, and Puppet, adopt the IaC approach to define the desired state of the servers under their management.
Ansible functions by bootstrapping servers and orchestrating them based on predefined playbooks. These playbooks, written in YAML, outline the operations Ansible will execute and the targeted resources it will operate on. These operations can include starting services, installing packages via the system’s package manager, or executing custom bash commands.
Both Chef and Puppet operate through central servers that issue instructions for orchestrating managed servers. Agent software needs to be installed on the managed servers. While Chef employs Ruby to describe resources, Puppet has its own declarative language.
Terraform seamlessly integrates with other IaC tools and DevOps systems, excelling in provisioning infrastructure resources rather than software installation and initial server configuration.
Unlike configuration management tools like Ansible and Chef, Terraform is not designed for installing software on target resources or scheduling tasks. Instead, Terraform utilizes providers to interact with supported resources.
Terraform can operate on a single machine without the need for a master or managed servers, unlike some other tools. It does not actively monitor the actual state of resources and automatically reapply configurations. Its primary focus is on orchestration. Typically, the workflow involves provisioning resources with Terraform and using a configuration management tool for further customization if necessary.
For Chef, Terraform provides a built-in provider that configures the client on the orchestrated remote resources. This allows for automatic addition of all orchestrated servers to the master server and further customization using Chef cookbooks (Chef’s infrastructure declarations).
Optimize your infrastructure management with our DevOps expertise. Harness the power of IaC tools for streamlined provisioning, configuration, and orchestration. Scale efficiently and achieve seamless deployments. Contact us now.
Popular Infrastructure as Code Tools
Terraform
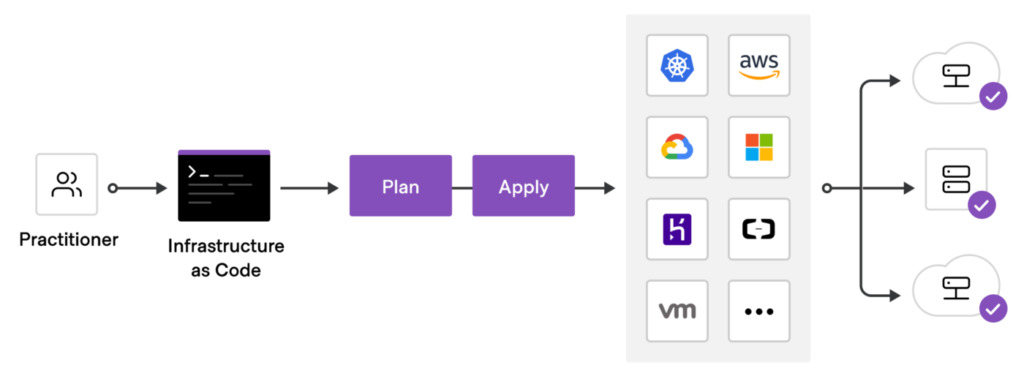
Terraform, introduced by HashiCorp in 2014, is an open-source Infrastructure as Code (IaC) solution. It operates based on a declarative approach to managing infrastructure, allowing you to define the desired end state of your infrastructure in a configuration file. Terraform then works to bring the infrastructure to that desired state. This configuration is applied using the PUSH method. Written in the Go programming language, Terraform incorporates its own language known as HashiCorp Configuration Language (HCL), which is used for writing configuration files that automate infrastructure management tasks.
Download: https://github.com/hashicorp/terraform
Terraform operates by analyzing the infrastructure code provided and constructing a graph that represents the resources and their relationships. This graph is then compared with the cached state of resources in the cloud. Based on this comparison, Terraform generates an execution plan that outlines the necessary changes to be applied to the cloud in order to achieve the desired state, including the order in which these changes should be made.
Within Terraform, there are two primary components: providers and provisioners. Providers are responsible for interacting with cloud service providers, handling the creation, management, and deletion of resources. On the other hand, provisioners are used to execute specific actions on the remote resources created or on the local machine where the code is being processed.
Terraform offers support for managing fundamental components of various cloud providers, such as compute instances, load balancers, storage, and DNS records. Additionally, Terraform’s extensibility allows for the incorporation of new providers and provisioners.
In the realm of Infrastructure as Code (IaC), Terraform’s primary role is to ensure that the state of resources in the cloud aligns with the state expressed in the provided code. However, it’s important to note that Terraform does not actively track deployed resources or monitor the ongoing bootstrapping of prepared compute instances. The subsequent section will delve into the distinctions between Terraform and other tools, as well as how they complement each other within the workflow.
Real-World Examples of Terraform Usage
Terraform has gained immense popularity across various industries due to its versatility and user-friendly nature. Here are a few real-world examples showcasing how Terraform is being utilized:
CI/CD Pipelines and Infrastructure for E-Health Platform
For our client, a development company specializing in Electronic Medical Records Software (EMRS) for government-based E-Health platforms and CRM systems in medical facilities, we leveraged Terraform to create the infrastructure using VMWare ESXi. This allowed us to harness the full capabilities of the local cloud provider, ensuring efficient and scalable deployments.
Implementation of Nomad Cluster for Massively Parallel Computing
Our client, S-Cube, is a software development company specializing in creating a product based on a waveform inversion algorithm for building Earth models. They sought to enhance their infrastructure by separating the software from the underlying infrastructure, allowing them to focus solely on application development without the burden of infrastructure management.
To assist S-Cube in achieving their goals, Gart Solutions stepped in and leveraged the latest cloud development techniques and technologies, including Terraform. By utilizing Terraform, Gart Solutions helped restructure the architecture of S-Cube’s SaaS platform, making it more economically efficient and scalable.
The Gart Solutions team worked closely with S-Cube to develop a new approach that takes infrastructure management to the next level. By adopting Terraform, they were able to define their infrastructure as code, enabling easy provisioning and management of resources across cloud and on-premises environments. This approach offered S-Cube the flexibility to run their workloads in both containerized and non-containerized environments, adapting to their specific requirements.
Streamlining Presale Processes with ChatOps Automation
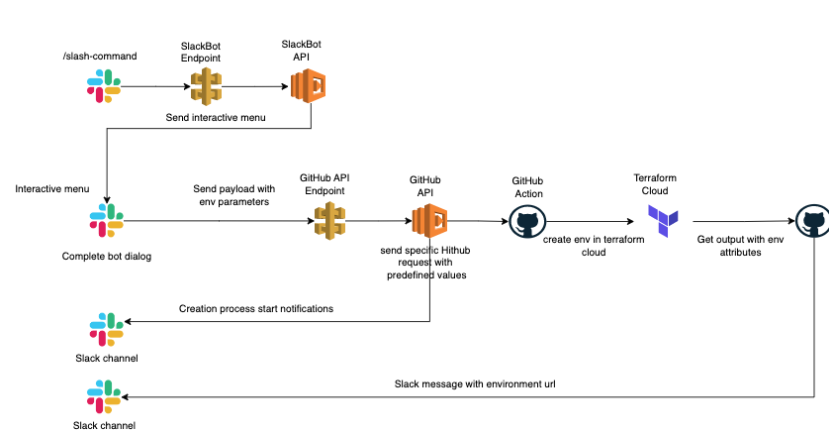
Our client, Beyond Risk, is a dynamic technology company specializing in enterprise risk management solutions. They faced several challenges related to environmental management, particularly in managing the existing environment architecture and infrastructure code conditions, which required significant effort.
To address these challenges, Gart implemented ChatOps Automation to streamline the presale processes. The implementation involved utilizing the Slack API to create an interactive flow, AWS Lambda for implementing the business logic, and GitHub Action + Terraform Cloud for infrastructure automation.
One significant improvement was the addition of a Notification step, which helped us track the success or failure of Terraform operations. This allowed us to stay informed about the status of infrastructure changes and take appropriate actions accordingly.
Unlock the full potential of your infrastructure with our DevOps expertise. Maximize scalability and achieve flawless deployments. Drop us a line right now!
AWS CloudFormation
AWS CloudFormation is a powerful Infrastructure as Code (IaC) tool provided by Amazon Web Services (AWS). It simplifies the provisioning and management of AWS resources through the use of declarative CloudFormation templates. Here are the key features and benefits of AWS CloudFormation, its declarative infrastructure management approach, its integration with other AWS services, and some real-world case studies showcasing its adoption.
Key Features and Advantages:
Infrastructure as Code: CloudFormation enables you to define and manage your infrastructure resources using templates written in JSON or YAML. This approach ensures consistent, repeatable, and version-controlled deployments of your infrastructure.
Automation and Orchestration: CloudFormation automates the provisioning and configuration of resources, ensuring that they are created, updated, or deleted in a controlled and predictable manner. It handles resource dependencies, allowing for the orchestration of complex infrastructure setups.
Infrastructure Consistency: With CloudFormation, you can define the desired state of your infrastructure and deploy it consistently across different environments. This reduces configuration drift and ensures uniformity in your infrastructure deployments.
Change Management: CloudFormation utilizes stacks to manage infrastructure changes. Stacks enable you to track and control updates to your infrastructure, ensuring that changes are applied consistently and minimizing the risk of errors.
Scalability and Flexibility: CloudFormation supports a wide range of AWS resource types and features. This allows you to provision and manage compute instances, databases, storage volumes, networking components, and more. It also offers flexibility through custom resources and supports parameterization for dynamic configurations.
Case studies showcasing CloudFormation adoption
Netflix leverages CloudFormation for managing their infrastructure deployments at scale. They use CloudFormation templates to provision resources, define configurations, and enable repeatable deployments across different regions and accounts.
Yelp utilizes CloudFormation to manage their AWS infrastructure. They use CloudFormation templates to provision and configure resources, enabling them to automate and simplify their infrastructure deployments.
Dow Jones, a global news and business information provider, utilizes CloudFormation for managing their AWS resources. They leverage CloudFormation to define and provision their infrastructure, enabling faster and more consistent deployments.
Ansible
Perhaps Ansible is the most well-known configuration management system used by DevOps engineers. This system is written in the Python programming language and uses a declarative markup language to describe configurations. It utilizes the PUSH method for automating software configuration and deployment.
What are the main differences between Ansible and Terraform? Ansible is a versatile automation tool that can be used to solve various tasks, while Terraform is a tool specifically designed for “infrastructure as code” tasks, which means transforming configuration files into functioning infrastructure.
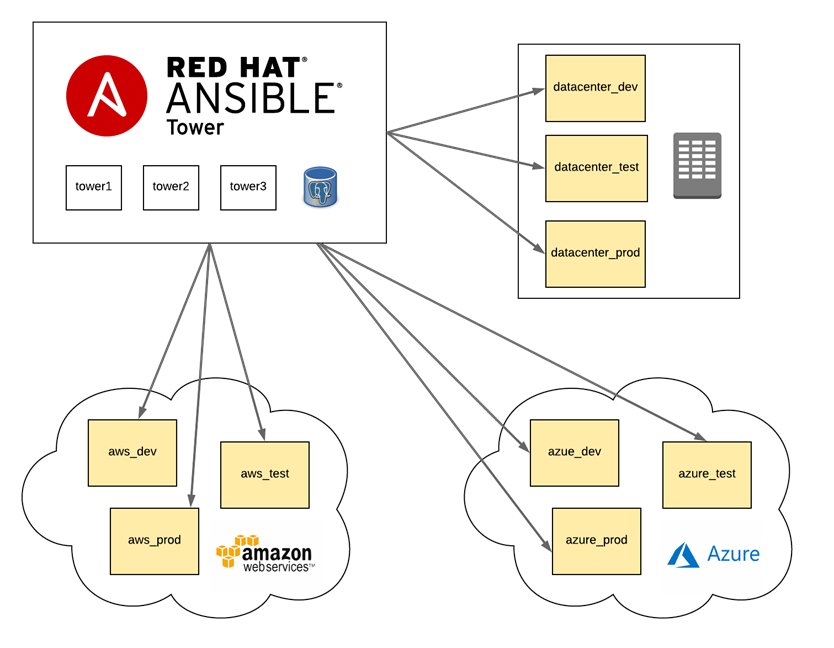
Use cases highlighting Ansible’s versatility
Configuration Management: Ansible is commonly used for configuration management, allowing you to define and enforce the desired configurations across multiple servers or network devices. It ensures consistency and simplifies the management of configuration drift.
Application Deployment: Ansible can automate the deployment of applications by orchestrating the installation, configuration, and updates of application components and their dependencies. This enables faster and more reliable application deployments.
Cloud Provisioning: Ansible integrates seamlessly with various cloud providers, enabling the provisioning and management of cloud resources. It allows you to define infrastructure in a cloud-agnostic way, making it easy to deploy and manage infrastructure across different cloud platforms.
Continuous Delivery: Ansible can be integrated into a continuous delivery pipeline to automate the deployment and testing of applications. It allows for efficient and repeatable deployments, reducing manual errors and accelerating the delivery of software updates.
Google Cloud Deployment Manager
Google Cloud Deployment Manager is a robust Infrastructure as Code (IaC) solution offered by Google Cloud Platform (GCP). It empowers users to define and manage their infrastructure resources using Deployment Manager templates, which facilitate automated and consistent provisioning and configuration.
By utilizing YAML or Jinja2-based templates, Deployment Manager enables the definition and configuration of infrastructure resources. These templates specify the desired state of resources, encompassing various GCP services, networks, virtual machines, storage, and more. Users can leverage templates to define properties, establish dependencies, and establish relationships between resources, facilitating the creation of intricate infrastructures.
Deployment Manager seamlessly integrates with a diverse range of GCP services and ecosystems, providing comprehensive resource management capabilities. It supports GCP’s native services, including Compute Engine, Cloud Storage, Cloud SQL, Cloud Pub/Sub, among others, enabling users to effectively manage their entire infrastructure.
Puppet
Puppet is a widely adopted configuration management tool that helps automate the management and deployment of infrastructure resources. It provides a declarative language and a flexible framework for defining and enforcing desired system configurations across multiple servers and environments.
Puppet enables efficient and centralized management of infrastructure configurations, making it easier to maintain consistency and enforce desired states across a large number of servers. It automates repetitive tasks, such as software installations, package updates, file management, and service configurations, saving time and reducing manual errors.
Puppet operates using a client-server model, where Puppet agents (client nodes) communicate with a central Puppet server to retrieve configurations and apply them locally. The Puppet server acts as a repository for configurations and distributes them to the agents based on predefined rules.
Pulumi
Pulumi is a modern Infrastructure as Code (IaC) tool that enables users to define, deploy, and manage infrastructure resources using familiar programming languages. It combines the concepts of IaC with the power and flexibility of general-purpose programming languages to provide a seamless and intuitive infrastructure management experience.
Pulumi has a growing ecosystem of libraries and plugins, offering additional functionality and integrations with external tools and services. Users can leverage existing libraries and modules from their programming language ecosystems, enhancing the capabilities of their infrastructure code.
There are often situations where it is necessary to deploy an application simultaneously across multiple clouds, combine cloud infrastructure with a managed Kubernetes cluster, or anticipate future service migration. One possible solution for creating a universal configuration is to use the Pulumi project, which allows for deploying applications to various clouds (GCP, Amazon, Azure, AliCloud), Kubernetes, providers (such as Linode, Digital Ocean), virtual infrastructure management systems (OpenStack), and local Docker environments.
Pulumi integrates with popular CI/CD systems and Git repositories, allowing for the creation of infrastructure as code pipelines.
Users can automate the deployment and management of infrastructure resources as part of their overall software delivery process.
SaltStack
SaltStack is a powerful Infrastructure as Code (IaC) tool that automates the management and configuration of infrastructure resources at scale. It provides a comprehensive solution for orchestrating and managing infrastructure through a combination of remote execution, configuration management, and event-driven automation.
SaltStack enables remote execution across a large number of servers, allowing administrators to execute commands, run scripts, and perform tasks on multiple machines simultaneously. It provides a robust configuration management framework, allowing users to define desired states for infrastructure resources and ensure their continuous enforcement.
SaltStack is designed to handle massive infrastructures efficiently, making it suitable for organizations with complex and distributed environments.
The SaltStack solution stands out compared to others mentioned in this article. When creating SaltStack, the primary goal was to achieve high speed. To ensure high performance, the architecture of the solution is based on the interaction between the Salt-master server components and Salt-minion clients, which operate in push mode using Salt-SSH.
The project is developed in Python and is hosted in the repository at https://github.com/saltstack/salt.
The high speed is achieved through asynchronous task execution. The idea is that the Salt Master communicates with Salt Minions using a publish/subscribe model, where the master publishes a task and the minions receive and asynchronously execute it. They interact through a shared bus, where the master sends a single message specifying the criteria that minions must meet, and they start executing the task. The master simply waits for information from all sources, knowing how many minions to expect a response from. To some extent, this operates on a “fire and forget” principle.
In the event of the master going offline, the minion will still complete the assigned work, and upon the master’s return, it will receive the results.
The interaction architecture can be quite complex, as illustrated in the vRealize Automation SaltStack Config diagram below.
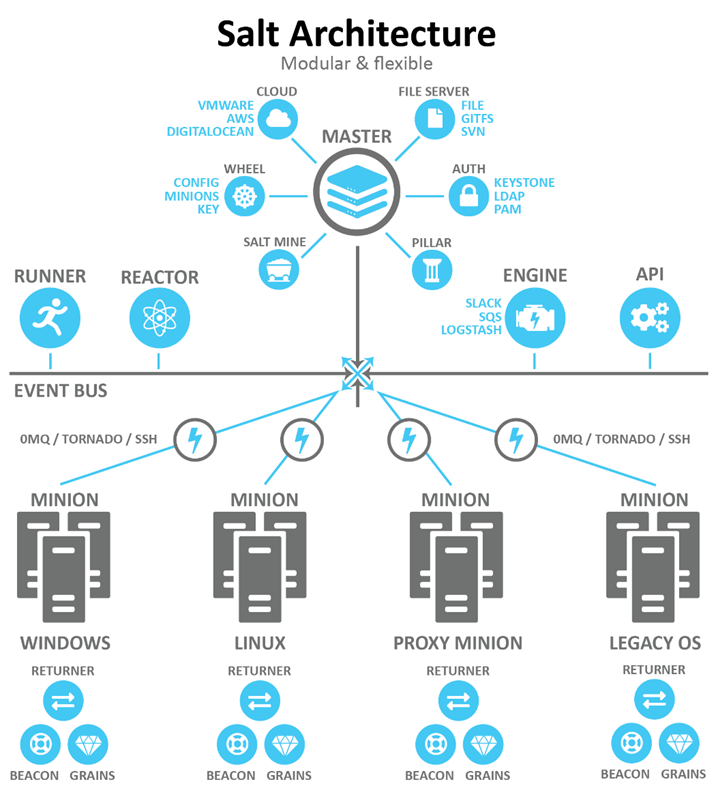
When comparing SaltStack and Ansible, due to architectural differences, Ansible spends more time processing messages. However, unlike SaltStack’s minions, which essentially act as agents, Ansible does not require agents to function. SaltStack is significantly easier to deploy compared to Ansible, which requires a series of configurations to be performed. SaltStack does not require extensive script writing for its operation, whereas Ansible is quite reliant on scripting for interacting with infrastructure.
Additionally, SaltStack can have multiple masters, so if one fails, control is not lost. Ansible, on the other hand, can have a secondary node in case of failure. Finally, SaltStack is supported by GitHub, while Ansible is supported by Red Hat.
SaltStack integrates seamlessly with cloud platforms, virtualization technologies, and infrastructure services.
It provides built-in modules and functions for interacting with popular cloud providers, making it easier to manage and provision resources in cloud environments.
SaltStack offers a highly extensible framework that allows users to create custom modules, states, and plugins to extend its functionality.
It has a vibrant community contributing to a rich ecosystem of Salt modules and extensions.
Chef
Chef is a widely recognized and powerful Infrastructure as Code (IaC) tool that automates the management and configuration of infrastructure resources. It provides a comprehensive framework for defining, deploying, and managing infrastructure across various platforms and environments.
Chef allows users to define infrastructure configurations as code, making it easier to manage and maintain consistent configurations across multiple servers and environments.
It uses a declarative language called Chef DSL (Domain-Specific Language) to define the desired state of resources and systems.
Chef Solo
Chef also offers a standalone mode called Chef Solo, which does not require a central Chef server.
Chef Solo allows for the local execution of cookbooks and recipes on individual systems without the need for a server-client setup.
Benefits of Infrastructure as Code Tools
Infrastructure as Code (IaC) tools offer numerous benefits that contribute to efficient, scalable, and reliable infrastructure management.
IaC tools automate the provisioning, configuration, and management of infrastructure resources. This automation eliminates manual processes, reducing the potential for human error and increasing efficiency.
With IaC, infrastructure configurations are defined and deployed consistently across all environments. This ensures that infrastructure resources adhere to desired states and defined standards, leading to more reliable and predictable deployments.
IaC tools enable easy scalability by providing the ability to define infrastructure resources as code. Scaling up or down becomes a matter of modifying the code or configuration, allowing for rapid and flexible infrastructure adjustments to meet changing demands.
Infrastructure code can be stored and version-controlled using tools like Git. This enables collaboration among team members, tracking of changes, and easy rollbacks to previous configurations if needed.
Infrastructure code can be structured into reusable components, modules, or templates. These components can be shared across projects and environments, promoting code reusability, reducing duplication, and speeding up infrastructure deployment.
Infrastructure as Code tools automate the provisioning and deployment processes, significantly reducing the time required to set up and configure infrastructure resources. This leads to faster application deployment and delivery cycles.
Infrastructure as Code tools provide an audit trail of infrastructure changes, making it easier to track and document modifications. They also assist in achieving compliance by enforcing predefined policies and standards in infrastructure configurations.
Infrastructure code can be used to recreate and recover infrastructure quickly in the event of a disaster. By treating infrastructure as code, organizations can easily reproduce entire environments, reducing downtime and improving disaster recovery capabilities.
IaC tools abstract infrastructure configurations from specific cloud providers, allowing for portability across multiple cloud platforms. This flexibility enables organizations to leverage different cloud services based on specific requirements or to migrate between cloud providers easily.
Infrastructure as Code tools provide visibility into infrastructure resources and their associated costs. This visibility enables organizations to optimize resource allocation, identify unused or underutilized resources, and make informed decisions for cost optimization.
Considerations for Choosing an IaC Tool
When selecting an Infrastructure as Code (IaC) tool, it’s essential to consider various factors to ensure it aligns with your specific requirements and goals.
Compatibility with Infrastructure and Environments
Determine if the IaC tool supports the infrastructure platforms and technologies you use, such as public clouds (AWS, Azure, GCP), private clouds, containers, or on-premises environments.
Check if the tool integrates well with existing infrastructure components and services you rely on, such as databases, load balancers, or networking configurations.
Supported Programming Languages
Consider the programming languages supported by the IaC tool. Choose a tool that offers support for languages that your team is familiar with and comfortable using.
Ensure that the tool’s supported languages align with your organization’s coding standards and preferences.
Learning Curve and Ease of Use
Evaluate the learning curve associated with the IaC tool. Consider the complexity of its syntax, the availability of documentation, tutorials, and community support.
Determine if the tool provides an intuitive and user-friendly interface or a command-line interface (CLI) that suits your team’s preferences and skill sets.
Declarative or Imperative Approach
Decide whether you prefer a declarative or imperative approach to infrastructure management.
Declarative tools focus on defining the desired state of infrastructure resources, while imperative Infrastructure as Code tools allow more procedural control over infrastructure changes.
Consider which approach aligns better with your team’s mindset and infrastructure management style.
Extensibility and Customization
Evaluate the extensibility and customization options provided by the IaC tool. Check if it allows the creation of custom modules, plugins, or extensions to meet specific requirements.
Consider the availability of a vibrant community and ecosystem around the tool, providing additional resources, libraries, and community-contributed content.
Collaboration and Version Control
Assess the tool’s collaboration features and support for version control systems like Git.
Determine if it allows multiple team members to work simultaneously on infrastructure code, provides conflict resolution mechanisms, and supports code review processes.
Security and Compliance
Examine the tool’s security features and its ability to meet security and compliance requirements.
Consider features like access controls, encryption, secrets management, and compliance auditing capabilities to ensure the tool aligns with your organization’s security standards.
Community and Support
Evaluate the size and activity of the tool’s community, as it can greatly impact the availability of resources, forums, and support.
Consider factors like the frequency of updates, bug fixes, and the responsiveness of the tool’s maintainers to address issues or feature requests.
Cost and Licensing
Assess the licensing model of the IaC tool. Some Infrastructure as Code Tools may have open-source versions with community support, while others offer enterprise editions with additional features and support.
Consider the total cost of ownership, including licensing fees, training costs, infrastructure requirements, and ongoing maintenance.
Roadmap and Future Development
Research the tool’s roadmap and future development plans to ensure its continued relevance and compatibility with evolving technologies and industry trends.
By considering these factors, you can select Infrastructure as Code Tools that best fits your organization’s needs, infrastructure requirements, team capabilities, and long-term goals.
See how we can help to overcome your challenges









