Why the DevOps vs DevSecOps debate still matters?
Software engineering has entered an era where speed without security is no longer merely inefficient—it is existentially risky. As organizations accelerate release cycles using automation, cloud platforms, and AI-assisted development, the traditional boundaries between building, running, and securing software have collapsed.
DevOps solved one historical problem: the friction between development and operations.
DevSecOps emerged to solve the next one: security debt created by speed itself.
In 2026, the distinction between DevOps and DevSecOps is not academic. It determines whether organizations can safely scale AI-generated code, survive automated attacks, meet regulatory obligations, and maintain trust in systems that now evolve faster than humans can manually inspect.
This article explores DevOps and DevSecOps not as competing models, but as successive architectural responses to systemic failures in software delivery—culminating in a security-embedded operating model designed for autonomous, AI-augmented systems.
The Historical Failure of Sequential Development
Waterfall and the Cost of Late Discovery
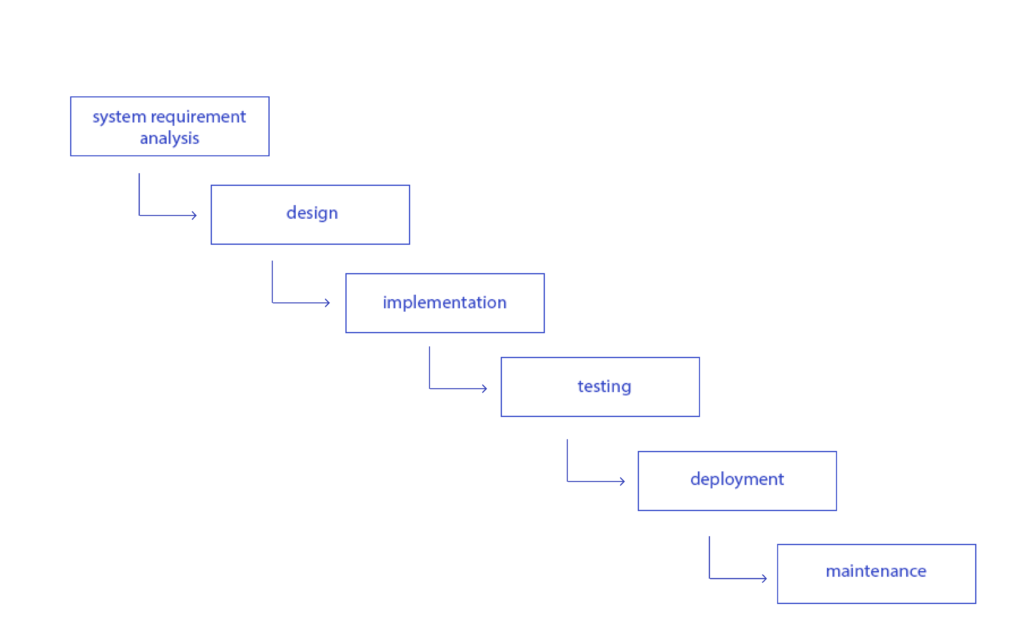
For decades, software was built using the Waterfall model, a linear sequence of requirements, design, implementation, testing, and deployment. While administratively neat, it assumed that:
- requirements would remain stable,
- risks could be fully anticipated upfront,
- and defects discovered late were acceptable.
In reality, Waterfall created compounding risk. Defects found during testing or production were exponentially more expensive to fix, and security flaws often surfaced only after systems were already exposed.
More critically, Waterfall institutionalized organizational silos:
- Developers optimized for feature delivery.
- Operations optimized for uptime and stability.
- Security was external, reactive, and often adversarial.
This misalignment made rapid adaptation nearly impossible.
DevOps: Optimizing for Flow and Stability
The Birth of DevOps
DevOps emerged in the late 2000s as a response to these failures. Sparked by Patrick Debois and popularized through early success stories like Flickr’s “10+ deploys per day,” DevOps reframed software delivery as a continuous, collaborative system rather than a sequence of handoffs.
The goal was not just faster releases, but predictable, repeatable, low-risk change.
The CAMS Model: DevOps as a System, Not a Toolchain
DevOps is best understood through the CAMS framework:
- Culture: Shared ownership across development, operations, and management
- Automation: CI/CD pipelines, infrastructure provisioning, and repeatable processes
- Measurement: Metrics-driven feedback loops (later formalized as DORA metrics)
- Sharing: Transparent communication of failures, learnings, and outcomes
By 2025, DevOps had become the industry default, with adoption nearing 85%.
But success created a new problem.
The Security Debt of High-Velocity Delivery
When Speed Outpaces Control
DevOps dramatically reduced deployment friction—but security practices largely remained unchanged:
- Threat modeling happened late or not at all.
- Vulnerability scanning was a gate, not a guide.
- Security teams reviewed releases after code was written.
This created what many organizations experienced as security debt:
- vulnerabilities accumulated silently,
- open-source dependencies expanded attack surfaces,
- cloud misconfigurations became the leading cause of breaches.
In regulated industries—finance, healthcare, government—this model simply did not scale.
DevSecOps: Security as a First-Class System Property
The Core Difference: Timing and Ownership
The fundamental difference between DevOps and DevSecOps is not tooling—it is when and by whom security is handled.
| Dimension | DevOps | DevSecOps |
|---|---|---|
| Primary Goal | Speed and reliability | Speed with verifiable security |
| Security Role | External or late-stage | Built-in, shared responsibility |
| Risk Focus | Downtime and failures | Vulnerabilities, compliance, exposure |
| Automation | Build & deploy | Security, compliance, governance as code |
DevSecOps does not slow DevOps down.
It restructures it so security moves at the same velocity as code.
“Shift Left”: The Operating Mechanism of DevSecOps
Why Early Security Changes Everything
The strategic engine of DevSecOps is Shift Left—moving security controls as close as possible to the point where code is written.
In practice, this means:
- security feedback inside the IDE,
- pre-commit scans for secrets and vulnerable dependencies,
- automated threat modeling during design,
- policy enforcement before infrastructure is provisioned.
Fixing a vulnerability during coding can be up to 90% cheaper than fixing it in production. Mature DevSecOps teams consistently demonstrate:
- faster remediation,
- lower incident rates,
- higher deployment frequency.
Security becomes an accelerator, not a brake.
The DevSecOps Toolchain: Defense in Depth, Automated
In a mature DevSecOps environment, security is not delivered through a single tool or control point. It emerges from a layered, automated system designed to surface risk as early as possible and respond to it continuously as software moves from idea to production. This approach—often described as defense in depth—ensures that no single failure, missed scan, or human oversight can expose the entire system.
Application security testing forms the foundation of this layered model. Static analysis tools examine source code and build artifacts before they ever run, identifying insecure patterns, missing input validation, and unsafe logic at the moment developers are still actively working on the code. Dynamic testing complements this by evaluating applications while they are running, revealing vulnerabilities that only appear in real execution contexts, such as authentication flaws, injection paths, or broken access controls. Together, these techniques close the gap between theoretical weakness and real-world exploitability.
Application Security Testing (AST)
- SAST: Finds insecure code patterns before execution
- DAST: Tests running applications for real-world exploitability
- SCA: Secures open-source and third-party dependencies
- IAST: Correlates runtime behavior with source code
- RASP: Protects applications in production
As modern software increasingly depends on open-source and third-party components, software composition analysis has become just as critical as scanning proprietary code. Dependency trees now represent a significant portion of the attack surface, and vulnerabilities introduced indirectly can be just as damaging as those written in-house. By automatically evaluating dependencies against known vulnerability databases during builds and tests, DevSecOps pipelines protect the software supply chain without requiring developers to manually audit every library they use.
More advanced teams introduce interactive and runtime protection mechanisms to reduce noise and increase precision. By observing how code behaves during functional testing, interactive testing technologies can directly map untrusted inputs to vulnerable execution paths, dramatically reducing false positives. Runtime protection extends this visibility into production environments, where applications can actively block exploit attempts in real time, providing a last line of defense against zero-day attacks or previously unknown attack vectors.
Beyond application code, the DevSecOps toolchain expands into infrastructure and operational security. Secrets management systems prevent credentials, API keys, and tokens from being hardcoded or leaked into version control. Infrastructure-as-code scanners evaluate cloud templates and configuration files before deployment, catching misconfigurations such as overly permissive access policies or unencrypted storage—issues that remain one of the leading causes of cloud breaches.
Beyond Applications
- Secrets management prevents credential leaks
- IaC scanning detects cloud misconfigurations early
- Diff-aware scanning preserves pipeline speed
The goal is not maximal scanning—it is precise, contextual, automated control.
What differentiates high-performing DevSecOps pipelines from slower, tool-heavy implementations is selectivity. Rather than scanning everything all the time, modern systems are diff-aware, focusing security analysis only on what has changed. This preserves fast feedback loops and prevents security tooling from becoming a bottleneck. Developers receive relevant, contextual feedback tied directly to their changes, which makes security actionable instead of disruptive.
Taken together, this automated, layered toolchain transforms security from a single gate at the end of delivery into a continuous capability embedded throughout the lifecycle. Each layer compensates for the limitations of the others, creating a resilient system where speed and protection reinforce each other rather than compete. In practice, this is where DevSecOps delivers its greatest value—not by adding more tools, but by orchestrating them into a coherent, automated defense that moves at the same pace as modern software development.
Infrastructure and Policy as Code: Governance Without Friction
As infrastructure moved to the cloud, manual configuration became a liability.
DevSecOps extends automation to governance itself:
- Infrastructure as Code (IaC) ensures consistency and auditability
- Policy as Code (PaC) enforces rules automatically using engines like Open Policy Agent (OPA)
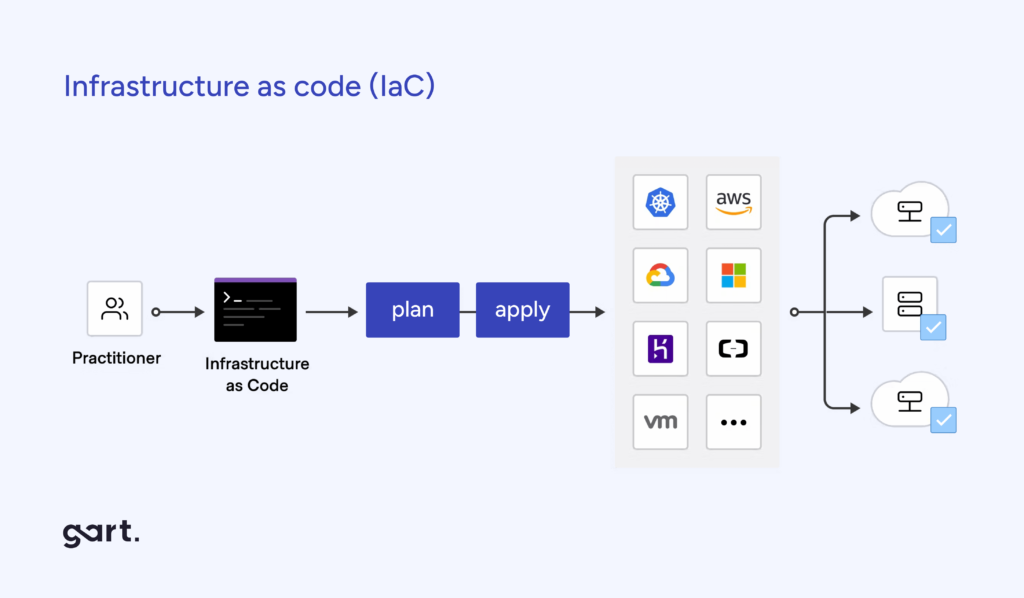
Examples:
- Preventing unencrypted storage before deployment
- Blocking insecure Kubernetes manifests at admission time
- Generating audit evidence automatically for SOC 2, HIPAA, or GDPR
This creates guardrails, not gates—allowing teams to move fast safely.
Culture: From Security Gatekeepers to Shared Ownership
Tools alone do not create DevSecOps. DevSecOps succeeds or fails less on tooling than on culture. In traditional organizations, security teams often operated as external reviewers, stepping in late to approve or reject releases. This positioning made security a perceived obstacle to delivery and reinforced adversarial dynamics between teams focused on speed and those focused on risk reduction.
DevSecOps replaces this model with shared ownership. Security is no longer something “handed off” to specialists but a responsibility distributed across development, operations, and security professionals. Developers are empowered to make secure decisions as they write code, operations teams enforce resilient environments, and security teams act as enablers who design guardrails rather than gates.
The cultural shift is from security as enforcement to security as collaboration:
- Developers own security outcomes
- Security teams enable, not block
- Operations enforce reliability and containment
In practice, this shift requires meeting engineers where they work. Security feedback must appear in the same tools developers already use—IDEs, pull requests, and issue trackers—rather than in separate reports or audits. As trust grows, security specialists increasingly collaborate directly with product teams, helping shape design decisions early instead of policing them later.
Successful organizations scale this through:
- Security champions inside engineering teams
- Pairing and embedding security engineers
- Threat modeling workshops and gamification
- Integrating security into existing workflows
Maturity is measured not by zero vulnerabilities, but by how fast teams learn and respond.
Measuring DevSecOps: Speed and Risk Signals
Traditional DevOps metrics, like deployment frequency, lead time, and change failure rate, remain important indicators of agility. But they don’t capture the full picture in a security-first environment.
DevSecOps expands the lens to include risk signals that reflect how effectively teams prevent, detect, and remediate vulnerabilities. Key measures include how quickly newly discovered flaws are addressed, how long critical issues linger in the system, and how many high-severity vulnerabilities reach production. By combining velocity with these security indicators, organizations can evaluate whether their fast-moving pipelines also maintain a strong risk posture.
DevSecOps extends classic DORA metrics with security indicators:
- Vulnerability discovery rate
- Mean time to remediate (MTTR)
- Mean vulnerability age
- Critical issues reaching production
Data from 2025 shows that mature DevSecOps organizations resolve vulnerabilities over ten times faster than less mature peers, while simultaneously increasing deployment frequency by up to 150 percent. This demonstrates a crucial point: when automated correctly, speed and security reinforce each other rather than compete, turning DevSecOps into a true accelerator for both innovation and resilience.
AI Changes Everything — and Exposes Everything
By 2025, 90% of developers used AI daily.
The DORA report confirms a hard truth:
AI does not fix broken systems — it amplifies them.
High-maturity teams get faster and safer.
Low-maturity teams accumulate debt at machine speed.
The key lesson is clear: AI is a force multiplier. In capable environments, it drives innovation safely. In fragile environments, it magnifies vulnerabilities and exposes weaknesses faster than human teams can respond. The challenge for 2026 and beyond is not whether AI will be used—it’s whether organizations have the culture, tooling, and guardrails in place to ensure that speed doesn’t come at the cost of security. In other words, AI changes everything, but without DevSecOps, it also exposes everything.
Vibe Coding, Agentic AI, and the New Security Gap
As we move into 2026, a new paradigm is reshaping software development: vibe coding. Developers now act as “conductors,” giving natural language prompts to AI systems that generate entire modules or applications. This accelerates prototyping at unprecedented speeds but introduces a hidden cost: security debt baked into AI-generated code.
By 2026:
- Up to 42% of code is AI-generated
- Nearly 25% of that code contains security flaws
- Developers increasingly do not fully trust what they ship
New risks emerge:
- hallucinated authentication bypasses,
- phantom dependencies,
- silent removal of security controls,
- AI-driven polymorphic attacks.
Compounding the challenge, adversaries are also leveraging agentic AI to launch adaptive attacks, creating a dynamic, real-time contest between offensive and defensive systems. In this environment, DevSecOps is no longer optional—it is the framework that allows organizations to integrate security into AI-assisted development, detect flawed code before it reaches production, and maintain trust even as machines take a more active role in creating software.
Security is no longer human-versus-human.
It is machine-versus-machine.
DevSecOps in the Agentic Era
In the era of agentic AI, DevSecOps evolves from a pipeline strategy into a continuous, autonomous capability. Security can no longer be a manual checkpoint or a final review—AI-driven development moves too fast, and attackers are already leveraging machine intelligence to probe vulnerabilities in real time.
The future DevSecOps model includes:
- autonomous vulnerability detection,
- AI-generated remediation PRs,
- automated validation pipelines,
- strict human-in-the-loop controls for high-impact logic.
Frameworks like NIST SSDF, OWASP SAMM, SLSA provide structure, but success depends on platform engineering that embeds security invisibly into developer experience.
Conclusion: DevSecOps Is Not Optional Anymore
DevOps made software fast.
DevSecOps makes it trustworthy at speed.
In an era of:
- AI-generated code,
- autonomous attackers,
- continuous compliance,
- and expanding attack surfaces,
security can no longer be a phase, a team, or a checklist.
DevSecOps is the operating system for modern software delivery.
Organizations that adopt it as a cultural, architectural, and automated system will not just ship faster—they will survive the next decade of software evolution.
See how we can help to overcome your challenges