Healthcare technology solutions must navigate a complex web of regulations designed to protect patient data and maintain confidentiality, integrity, and availability.
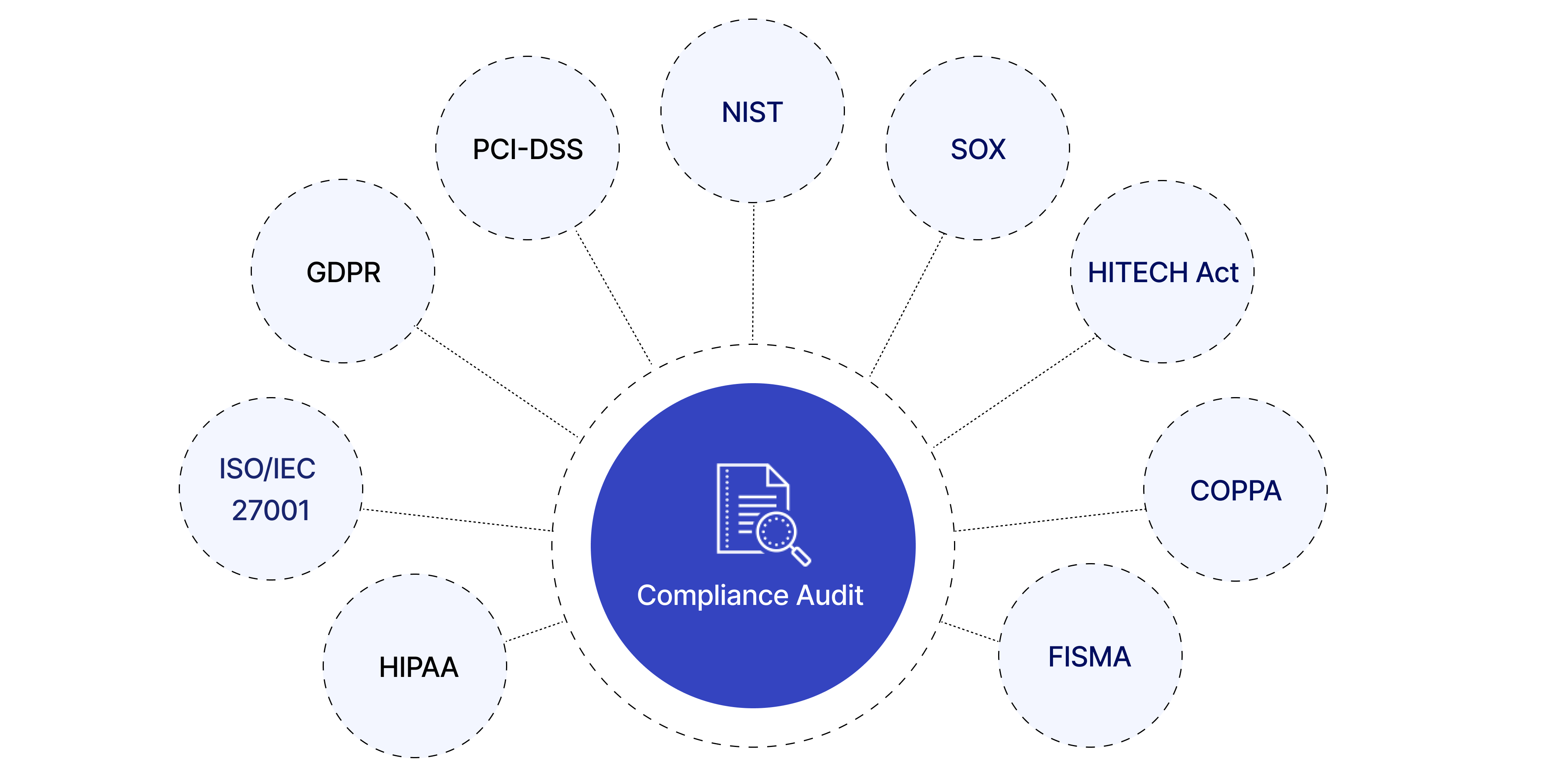
Six significant compliance frameworks that healthcare providers and technology developers must adhere to are HIPAA, CCPA, GDPR, NIST, HiTECH, and PIPEDA.
Let’s take a closer look at each of those frameworks:
HIPAA Compliance
The Health Insurance Portability and Accountability Act (HIPAA) is a critical regulation for any technological solutions developed for the US market. Enacted in 1996, HIPAA mandates the protection of Protected Healthcare Information (PHI). It ensures that electronically protected health information maintains its confidentiality, integrity, and availability. Compliance with HIPAA involves implementing robust security measures to prevent unauthorized access, breaches, and misuse of patient data. This includes encryption, access controls, and regular audits to ensure that all processes align with HIPAA standards.
CCPA Compliance
The California Consumer Privacy Act (CCPA) is another cornerstone of data protection in the United States. Although it primarily targets businesses operating in California, its implications are far-reaching, especially for healthcare providers handling large volumes of personal data. The CCPA focuses on transparency, requiring organizations to inform clients about the data collected, its purpose, and how it will be used. Patients have the right to request a detailed report of their data, demand its deletion, or opt out of data sharing with third parties. Ensuring CCPA compliance necessitates rigorous data management practices and responsive mechanisms to address patient requests promptly.
GDPR Compliance
The General Data Protection Regulation (GDPR) represents one of the most stringent data protection laws globally. Introduced in Europe in 2018, GDPR applies to any healthcare apps and services operating within the European Union. Its reach extends to any company processing data related to EU citizens, regardless of the company's location. GDPR emphasizes patient consent, data minimization, and the right to be forgotten. Healthcare providers must ensure that data is collected and processed transparently, securely, and only for specified purposes. Non-compliance can result in severe financial penalties, making adherence to GDPR a top priority for any organization handling personal health data in Europe.
NIST Compliance
The National Institute of Standards and Technology (NIST) framework is another collection of standards, tools, and technologies designed to protect users’ data in the United States. According to research, 70% of surveyed organizations consider the NIST framework as the best cybersecurity practice, but many say it requires significant investment. The NIST framework is renowned for its comprehensive approach to cybersecurity, offering guidelines for identifying, protecting, detecting, responding to, and recovering from cyber incidents. Implementing NIST standards helps healthcare organizations bolster their security posture, ensuring they can safeguard sensitive health information effectively.
HiTech Compliance
The Health Information Technology for Economic and Clinical Health (HiTECH) Act focuses more on the Electronic Health Record (EHR) systems' data security and is also valid in the United States. Enacted in 2009 and integrated into the HIPAA Final Omnibus Rule in 2013, HiTECH aims to promote the adoption and meaningful use of health information technology. Now, HIPAA-compliant applications are considered HiTECH compliant. This alignment simplifies compliance efforts for healthcare providers, ensuring they meet rigorous standards for data protection and patient privacy across multiple regulatory frameworks.
PIPEDA Compliance
The Personal Information Protection and Electronic Documents Act (PIPEDA) governs cloud storage and other medical software working in the Canadian market. Compliance with PIPEDA is crucial for any healthcare technology solutions operating in Canada. An interesting fact is that if your app is compliant with PIPEDA, it’s most likely compliant with the GDPR since these two laws are quite similar. PIPEDA emphasizes obtaining consent for data collection, ensuring data accuracy, and implementing safeguards to protect personal information. Compliance with PIPEDA helps organizations build trust with Canadian patients and ensures robust data protection practices.
Project Example: Gart's Expertise in ISO 27001 Compliance
Challenges:
Our client, Spiral Technology, faced significant challenges related to data security and cloud migration. The primary concerns were ensuring compliance with ISO 27001 standards and seamlessly transitioning their data and operations to the cloud without compromising security or disrupting their services.
Proposed Solutions:
ISO 27001 Compliance
Gart Solutions provided expert guidance and support to Spiral Technology, helping them achieve ISO 27001 certification. This involved implementing comprehensive security measures, conducting thorough risk assessments, and establishing robust data protection protocols.
Seamless Cloud Migration
To address the challenge of cloud migration, Gart Solutions developed a detailed migration plan that minimized downtime and ensured data integrity, utilizing advanced encryption and secure data transfer methods to protect sensitive information during the transition.
Continuous Monitoring and Audits
For post-migration, Gart Solutions set up continuous monitoring and regular audits to maintain ISO 27001 compliance and address any emerging security threats promptly.
More details about this Case Study – by the link.
Interested in being prepared for a compliance audit & certification - contact Us!
We will help you to understand the specifics and be prepared, as well as from a technology integration and data management perspective.
Conclusion
Compliance in healthcare is an ongoing challenge that requires constant vigilance, investment in technology, and a thorough understanding of regulatory requirements.
By adhering to HIPAA, CCPA, GDPR, NIST, HiTECH, and PIPEDA, healthcare providers can protect patient data, build trust, and avoid costly penalties. As the regulatory landscape continues to evolve, staying informed and proactive in compliance efforts will remain essential for success in the healthcare industry.

The NIS2 (Network and Information Security Directive) is a comprehensive directive that mandates organizations to implement robust security measures and document compliance to protect critical assets and ensure community continuity.
For organizations subject to NIS2 requirements, CISOs, and IT security officers must ensure robust internal compliance preparedness.
Why NIS2 Compliance Matters
NIS2 aims to enhance the overall level of cybersecurity in the EU by:
Improving the resilience of critical infrastructure.
Enhancing the security of network and information systems.
Ensuring rapid response to and recovery from cyber incidents.
For organizations subject to NIS2 requirements, compliance is not just a legal obligation but a vital component of risk management and operational continuity. Failing to comply can result in significant financial penalties, reputational damage, and operational disruptions.
Who is affected by NIS2?
NIS2 affects all big organizations that work in the European Union and are considered important to society. This includes organizations that:
Have 50 or more employees, or
Make over €10 million in revenue each year
NIS2 puts these organizations into two groups:
Essential organizations - These are very important sectors like energy, healthcare, transportation, and water supply.
Important organizations - These are sectors like manufacturing, food production, waste management, and postal services.
So in simple terms, if your fairly large organization operates in the EU and provides crucial services or products to society, then NIS2 applies to you. The directive aims to ensure these vital entities have strong cybersecurity measures in place.
The penalties for not following NIS2 rules are different depending on whether an organization is labeled as "essential" or "important".
For essential organizations:
They can be fined up to €10 million, or
They can be fined at least 2% of their total worldwide revenue from the previous year, whichever amount is higher.
For important organizations:
They can be fined up to €7 million, or
They can be fined at least 1.4% of their total worldwide revenue from the previous year, whichever amount is higher.
Gart’s NIS2 Solution
Gart offers a solution that simplifies the complexity of NIS2 compliance. The solution provides a systematic approach tailored to your ongoing operations and compliance efforts. By adopting Gart’s solution, you gain access to:
A systematic compliance framework for analyzing and documenting the security of critical assets.
Assurance of effective compliance work throughout your organization, aligned with good security practices and NIS2 requirements by applying ISO/EIC 27001/2 security principles.
Use of questionnaires to review the directive's requirements and ensure all documentation requirements are met, preparing you for audits.
Clear guidance on how to register significant security incidents with CSIRT, ensuring a proactive approach.
Read more: Gart’s Expertise in ISO 27001 Compliance Empowers Spiral Technology for Seamless Audits and Cloud Migration
How Does Gart Solution Support NIS2 Compliance?
NIS2 Requirement 1: Have policies for analyzing risks and information security
Gart can find and evaluate all assets, systems, weaknesses, and cyber/operational risks in critical infrastructure environments. It uses this detailed visibility to automatically create and enforce network security policies that reduce exposure to those identified risks.
In simple terms, Gart's solution allows organizations to:
Discover all their critical assets, systems, and potential vulnerabilities
Assess the cyber and operational risks in their environments
Automatically define security policies to protect against those risks
Enforce those security policies across their networks
NIS2 Requirement 2: Dealing with Security Incidents
Gart Solutions constantly keeps watch over all critical infrastructure systems for any signs of potential threats, both known and new. It analyzes all security alerts in detail to prioritize the most important issues. Gart also integrates with existing security tools like SIEM and SOAR to extend an organization's security processes across all of its critical systems.
In simpler terms, Gart's solution allows organizations to:
Continuously monitor all their vital systems and networks
Quickly detect any potential cyber threats, even new unidentified ones
Understand the context and importance of every security alert
Work seamlessly with their existing security tools and workflows
Expand their incident response capabilities to cover all critical infrastructure
NIS2 Requirement 3: Managing Crises
Gart provides:
A complete, up-to-date list of all critical systems
Logging of all changes and unusual activity in assets and networks
Ability to create and enforce security policies to separate networks and control access
Ready integration with backup and recovery tools
All of these capabilities from Gart help organizations improve their overall crisis management and ensure the continuity of essential operations.
In simpler terms, Gart's solution allows organizations to:
Know exactly what critical assets they have at all times
Track all activity so they can investigate incidents
Lock down systems by enforcing strict security controls
Quickly backup and restore systems if needed
NIS2 Requirement 4: Security of Networks and Information Systems
By utilizing Gart's capabilities, customers can effectively:
Identify vulnerabilities and insecure configurations in their critical networks and systems
Assess and manage the cyber risks to their operational environments
Allow remote access for personnel to do their work securely
In simple terms, Gart helps organizations implement robust security measures for their networks and information systems as required by NIS2. This includes finding and fixing vulnerabilities, evaluating risks, and controlling access - all crucial for securing vital operational technology.
NIS2 Requirement 5: Basic Cybersecurity Practices and Training
Gart's solution helps organizations:
Identify areas where they need to improve their basic cybersecurity habits and procedures based on risk assessments.
Ensure all personnel, whether employees or vendors, follow proper access controls, password management, and other essential cybersecurity practices.
Use the recommendations to develop training programs to raise cybersecurity awareness and skills.
NIS2 Requirement 6: Policies and Procedures for Data Encryption
Gart provides:
1) Encryption of all user data, critical system data, and other sensitive information in compliance with NIS2, GDPR, and other regulations.
2) Alerts when sensitive data like personal health records is being processed in a way that violates security policies or could lead to a data breach.
Here's a rewording in simple language:
NIS2 Requirement 7: Using Multi-Factor Authentication and Secure Communications
Gart helps organizations:
- Enforce strong access controls like multi-factor authentication across their workforce and supply chain vendors/partners
- Allow only authorized and verified personnel to access critical systems remotely or on-site
- Ensure all communications to operational technology are fully secured
- Meet audit requirements by recording all access sessions
Get a sample of IT Audit
Sign up now
Get on email
Loading...
Thank you!
You have successfully joined our subscriber list.
Key Features:
Mapping of Critical Assets
We will create an overview of the various types of critical assets within your value chain and document their security levels.
Risk Assessment of Critical Assets, Systems, and Processes
We will conduct a risk assessment based on the current threat landscape, the assets' placement within the value chain, and their potential societal consequences.
GAP Analysis
We will obtain a clear overview of your current compliance level and implementation, identifying the essential control objectives required for NIS2.
Automated Processes
We will automate control follow-ups and communication with internal stakeholders to ensure all relevant tasks are carried out correctly and on time.
Compliance Control and Scope of SoA
We will begin with an initial compliance review, prioritize, and scope the Statement of Applicability (SoA) based on NIS2 requirements.
Create Awareness and Communicate Directly with Stakeholders
We will create awareness and directly communicate with stakeholders to keep everyone informed about policy and procedural changes, ensuring everyone understands their role.
Overview of Reporting to CSIRT
We will establish a process for reporting significant incidents and threats to the organization or its supply chain to CSIRT, protecting critical assets quickly and efficiently.
Ongoing Auditing
We will document internal compliance with NIS2 via dedicated management controls and functionality for auditing critical suppliers.
About the NIS2 Directive or NIS2 framework
The NIS 2 Directive, also referred to as the NIS2 framework, is a European Union regulation aimed at enhancing cybersecurity across the bloc. Here's a breakdown of the key points:
Goals:
Improve overall cybersecurity posture in the EU.
Strengthen existing cybersecurity measures in critical sectors.
Ensure a consistent approach to cybersecurity risk management across member states.
Key Features:
Broader Scope: NIS2 applies to a wider range of sectors compared to the previous NIS Directive. This includes essential services (energy, transport, water, etc.) and important entities in sectors like waste management, postal services, manufacturing, and more.
Enhanced Risk Management: Organizations must implement robust cybersecurity measures to manage risks to their network and information systems. This includes measures to prevent incidents, minimize their impact, and report them effectively.
Incident Reporting: Entities are required to report significant incidents to relevant authorities. This allows for faster response and improved coordination across member states.
Supply Chain Security: The directive emphasizes the importance of supply chain security. Organizations need to consider the cybersecurity risks associated with their suppliers and vendors.
Cooperation and Information Sharing: Increased cooperation and information sharing among member states and relevant authorities are crucial aspects of NIS2.
Current Status:
Adopted in December 2022 and came into effect in January 2023.
EU member states have until October 17, 2024 to transpose the NIS2 Directive into national law.
By April 17, 2025, member states need to establish a list of essential entities falling under the directive.
NIS2-Compliance-Checklist-A-Comprehensive-Guide-to-Audit_Free-PDFDownload
Conclusion
The European Union's Network and Information Security Directive, known as NIS2, sets stringent requirements for organizations to safeguard their critical assets and ensure the continuity of essential services.
Gart is here to guide you through every step of the process, providing the expertise, tools, and support you need to achieve and maintain compliance. With our systematic approach, you can focus on your core business operations, confident that your information security is in capable hands.
Are you ready to simplify your NIS2 compliance journey? Contact Gart today to learn more about how we can help you strengthen your information security and achieve regulatory compliance with ease.

Compliance monitoring is the ongoing process of checking that an organization is following all the rules, regulations, and standards that apply to its operations. In simple terms, it's about making sure a company is "playing by the rules" set by governments, industry bodies, or its own policies
This practice is critical in several industries, including:
Healthcare
Finance and banking
Pharmaceuticals
Energy and utilities
Food and beverage manufacturing
Environmental services
Compliance monitoring helps ensure that an organization follows laws and rules. It helps avoid legal problems and fines, and it builds the organization's reputation and trust with clients and partners.
Key Components of Compliance Monitoring
Effective compliance monitoring involves several important parts working together. At its core, there's a clear set of rules or standards that a company needs to follow. These could be laws, industry regulations, or even the company's own policies. Visit our compliance audits page to explore different compliance frameworks and regulations in detail.
Next comes the crucial step of actually checking compliance. This involves regularly examining the company's activities and comparing them against established rules and regulations. It's essentially a health check-up for the business, ensuring everything is running according to plan. For companies looking to streamline this process, Gart Solutions offers specialized services to help assess regulatory compliance. Our expertise can be particularly valuable in navigating complex regulatory landscapes, providing businesses with peace of mind that they're meeting all necessary standards and requirements.
Read more: Gart’s Expertise in ISO 27001 Compliance Empowers Spiral Technology for Seamless Audits and Cloud Migration
Good record-keeping is another crucial piece. Companies need to keep detailed notes about what they're doing and how they're following the rules. This helps prove they're on track if anyone asks.
There's also the tech side of things. Many companies use special software to help track and manage their compliance efforts. This can make the whole process smoother and more accurate.
Read more about RMF (Resource Management Framework) a unified system for monitoring digital solutions for landfills that we developed for our client.
Lastly, there's the response plan. This is what the company does if they find they're not following a rule. It might involve fixing the problem, reporting it to the right people, or changing how things are done to prevent it from happening again.
Risk Assessment: Finding out where things might go wrong
Policies and Procedures: Writing down clear rules for everyone to follow
Training: Teaching employees about the rules and why they matter
Regular Checks: Looking at work often to make sure rules are being followed
Reporting: Keeping track of how well the company is following rules
Technology: Using computers and software to help monitor things
Updating: Changing the monitoring system when new rules come out
Response Plan: Knowing what to do if a rule is broken
Documentation: Keeping good records of all compliance activities
Leadership Support: Making sure bosses take compliance seriously
All these parts work together to create a strong compliance monitoring system, helping companies stay on the right side of the rules and avoid potential problems.
Types of Compliance Monitoring
Compliance monitoring comes in various forms, each serving a specific purpose in ensuring an organization adheres to relevant rules and regulations.
One common type is regulatory compliance monitoring. This focuses on making sure a company follows laws and regulations set by government agencies. For example, a bank might monitor its practices to ensure it complies with anti-money laundering laws.
Internal compliance monitoring is another important type. Here, companies check if their employees are following internal policies and procedures. This could involve reviewing expense reports to ensure they match company guidelines, or checking that proper safety protocols are being followed in a manufacturing plant.
Industry-specific compliance monitoring is crucial for businesses operating in highly regulated sectors. For instance, healthcare providers must monitor their practices to ensure patient data privacy, while food manufacturers need to check that their production processes meet food safety standards.
Environmental compliance monitoring has become increasingly important. Companies, especially those in manufacturing or energy sectors, must track their environmental impact to ensure they're meeting pollution control regulations.
Financial compliance monitoring is critical for publicly traded companies. This involves ensuring accurate financial reporting and adhering to accounting standards to maintain investor trust and meet stock exchange requirements.
Lastly, there's technology compliance monitoring. With the rise of data protection laws, companies must monitor how they collect, use, and store digital information to protect consumer privacy and prevent data breaches.
Each type of compliance monitoring plays a vital role in helping organizations navigate the complex landscape of rules and regulations they face in today's business world.
Challenges in Compliance Monitoring
One of the biggest challenges is dealing with complex and ever-changing regulations. Laws and industry standards are often intricate, with many details to track. What's more, these rules frequently change, sometimes without much warning. This means companies must constantly update their knowledge and practices to stay compliant.
Another major concern is balancing compliance with data privacy and security. In today's digital age, many compliance efforts involve handling sensitive information. Companies need to find ways to monitor and report on their activities without putting private data at risk. This can be especially tricky when dealing with customer information or confidential business data.
Resource limitations also pose a significant challenge. Effective compliance monitoring often requires dedicated staff, sophisticated software, and ongoing training. For many businesses, especially smaller ones, finding the budget and personnel for these efforts can be difficult. They must find ways to meet regulatory requirements without breaking the bank or stretching their teams too thin.
Need a Compliance Audit?
Is your business fully aligned with the latest regulations and standards? At Gart Solutions, we specialize in comprehensive compliance monitoring to keep you on the right side of the rules. Our expert team offers tailored audits and monitoring services across various industries, including healthcare, finance, pharmaceuticals, and more.
Ensure your business stays compliant and protected — contact Gart Solutions for a customized compliance audit today!