- What is Infrastructure Monitoring in DevOps?
- Why Monitoring is Crucial?
- The Complexity of Monitoring in DevOps
- Key Challenges Faced
- Types of Monitoring in DevOps
- Three Pillars of Monitoring
- Monitoring Tools – Choosing the Right Monitoring Stack
- Real-World Monitoring Use Cases
- Common Mistakes in Monitoring
- Future of Monitoring in DevOps
- Conclusion
What is Infrastructure Monitoring in DevOps?
Imagine driving a car with no dashboard. You wouldn’t know your speed, fuel level, or engine temperature – until you break down. That’s exactly what monitoring is for DevOps. It’s the dashboard that keeps your digital solutions running smoothly. In simple terms, monitoring in DevOps means continuously collecting, analyzing, and interpreting data about your systems, applications, and infrastructure to ensure everything works as it should.
Monitoring covers the entire ecosystem – cloud resources, servers, containers, applications, databases, and networks. It tells you what’s happening under the hood, provides insights to optimize performance, and alerts you when something goes wrong.
For example, in a modern microservices architecture, dozens of interconnected services communicate simultaneously. If one service fails or becomes slow, the entire application performance is affected. Infrastructure Monitoring acts as your real-time detective, pinpointing the exact root cause quickly so your team can resolve it before users even notice.
But monitoring is not just about “checking if it’s working.”
It empowers:
- Proactive issue resolution before impacting users.
- Data-driven decision making for capacity planning.
- Enhanced security through anomaly detection.
- Better customer experiences by ensuring fast and reliable services.
In DevOps, where continuous integration and deployment (CI/CD) pipelines push updates rapidly, monitoring becomes a safety net to catch failures early, enabling fast recovery without fear of hidden issues.
Why Monitoring is Crucial?
Without monitoring, DevOps is like flying blind. Here’s why it’s crucial:
- Faster Troubleshooting & Reduced Downtime
Imagine an e-commerce app going down during a flash sale. Every minute lost equals revenue lost. Monitoring provides real-time visibility, helping teams resolve incidents instantly. - Performance Optimization
Monitoring uncovers bottlenecks in CPU, memory, databases, or network, enabling teams to fine-tune configurations for peak performance. - Informed Capacity Planning
By understanding usage trends and traffic patterns, businesses can plan future infrastructure needs, avoiding costly over-provisioning or risky under-provisioning. - Compliance & Security
Regulatory standards often require detailed system logs and audit trails. Monitoring ensures all activities are recorded and security threats are detected early. - Better User Experience
Modern users expect instant, smooth interactions. Monitoring ensures your app’s uptime, speed, and reliability remain consistent, building user trust and brand reputation.
Ultimately, monitoring forms the backbone of a reliable, scalable, and resilient DevOps ecosystem.

The Complexity of Monitoring in DevOps
Why is Monitoring Complex?
Monitoring might sound straightforward – just install tools, collect metrics, and view dashboards, right? Not exactly. The complexity arises because:
- There’s no universal approach
Every project, application, and infrastructure has unique requirements. - Data overload is real
With thousands of metrics streaming in, identifying what truly matters is challenging. - Interdependencies complicate monitoring
In microservices, one service’s failure can ripple into many others, making root cause analysis tough. - Rapidly changing environments in CI/CD mean that monitoring configurations need continuous updates.
For example, monitoring a static on-prem server cluster differs entirely from monitoring dynamic Kubernetes pods that scale up and down rapidly based on traffic.
Key Challenges Faced
Here are the major challenges that make monitoring a complex task:
- Identifying Critical Metrics
Not everything needs to be monitored. Picking metrics that impact business goals without drowning in unnecessary data is an art. - Tool Overload
Using multiple tools for logs, metrics, and traces often leads to fragmented insights, increasing mean time to detect (MTTD) and resolve (MTTR) incidents. - Alert Fatigue
Poorly configured alerts trigger for trivial issues, causing teams to ignore even critical alerts over time. - Integration with DevOps Pipelines
Monitoring must integrate seamlessly with CI/CD pipelines to maintain visibility across automated deployments. - Scalability
As systems grow, monitoring solutions must handle massive data volumes without becoming performance bottlenecks themselves. - Cost Management
High-frequency data collection and storage in third-party monitoring platforms can escalate costs significantly if not optimized.
Effective monitoring strategies address these complexities through smart metric selection, streamlined tools integration, and automation.
Determining what to monitor, what truly matters for the project, requires DevOps engineers to:
- Identify what to monitor,
- Determine what to display,
- Define how to execute these tasks.
The most critical question is not how to monitor, but what to monitor.
Types of Monitoring in DevOps
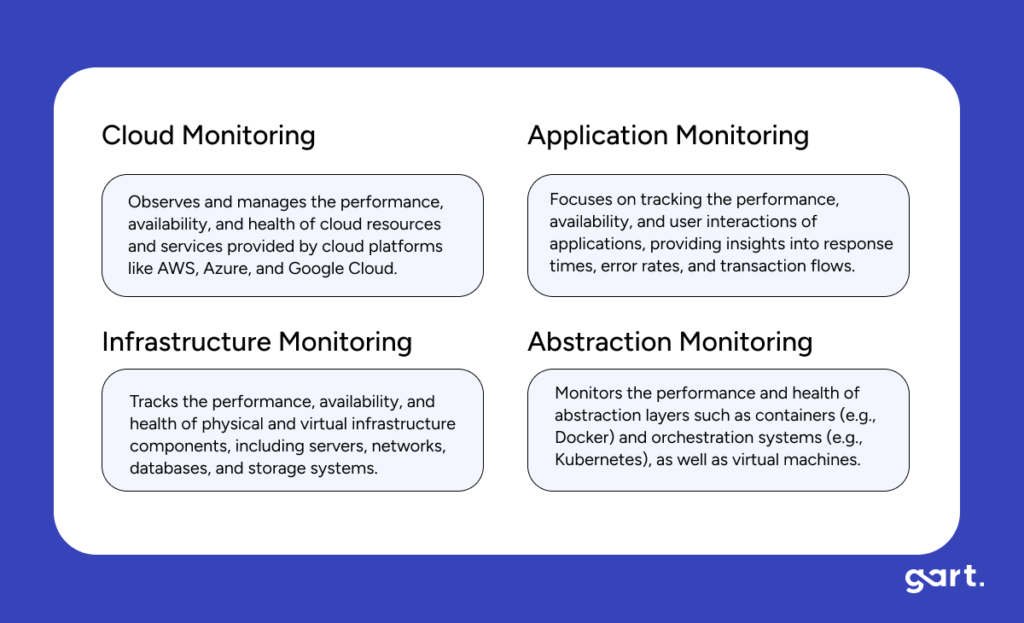
Monitoring spans multiple layers of your tech stack. Understanding these layers helps design a holistic monitoring strategy.
- Cloud Level Monitoring
Monitors services offered by cloud providers like AWS, Azure, and Google Cloud, including resource health, billing, and policy compliance. - Infrastructure Level Monitoring
Covers physical and virtual servers, databases, networks, and storage systems to ensure foundational stability. - Abstraction Level Monitoring
Focuses on containers (Docker), orchestration (Kubernetes), and virtual machines to manage application deployment environments efficiently. - Application Level Monitoring
Tracks application performance, transactions, errors, and user experiences to maintain high service quality.
Each layer has distinct metrics, challenges, and tools. Ignoring any of these layers can leave blind spots in your monitoring setup, risking operational inefficiencies.
In essence, monitoring involves tracking the state of a solution across these levels to ensure optimal performance, efficiency, and reliability.
Cloud Level Monitoring Explained
Cloud environments form the base of most modern digital solutions. Here’s what cloud monitoring involves:
AWS Monitoring
AWS offers CloudWatch, a powerful tool to collect logs, metrics, and events. For example:
- EC2 instances: CPU utilization, disk I/O, network throughput.
- RDS databases: Connection counts, read/write latency.
- Lambda functions: Invocation errors, duration, throttles.
AWS CloudWatch integrates with SNS for alerts and with third-party tools like Grafana for enhanced visualizations.
Azure Monitoring
Azure’s native monitoring solution is Azure Monitor, which provides:
- Metrics collection across resources.
- Log Analytics for querying data.
- Application Insights for real-time application performance monitoring.
Azure Monitor’s integration with Sentinel further enhances security monitoring, creating a unified observability and threat detection system.
Google Cloud Monitoring
Google Cloud offers Operations Suite (formerly Stackdriver), which includes:
- Monitoring: Dashboards, alerts, uptime checks.
- Logging: Centralized logs collection across resources.
- Error Reporting & Debugging: Application error tracking with detailed stack traces.
It integrates seamlessly with Google Kubernetes Engine (GKE) for container monitoring.
Cloud level monitoring ensures visibility, compliance, and optimal resource utilization, preventing unexpected bills and downtimes.
Infrastructure Level Monitoring
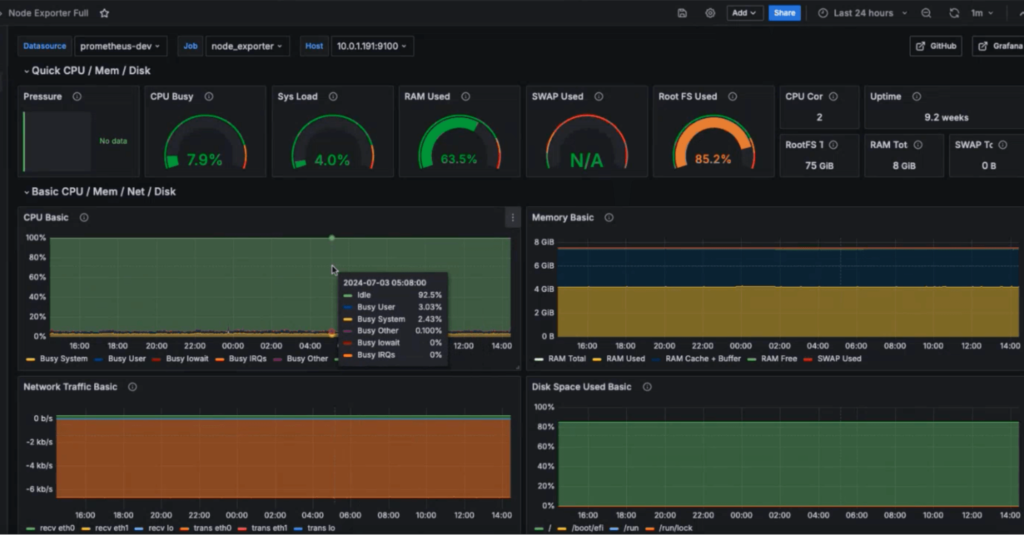
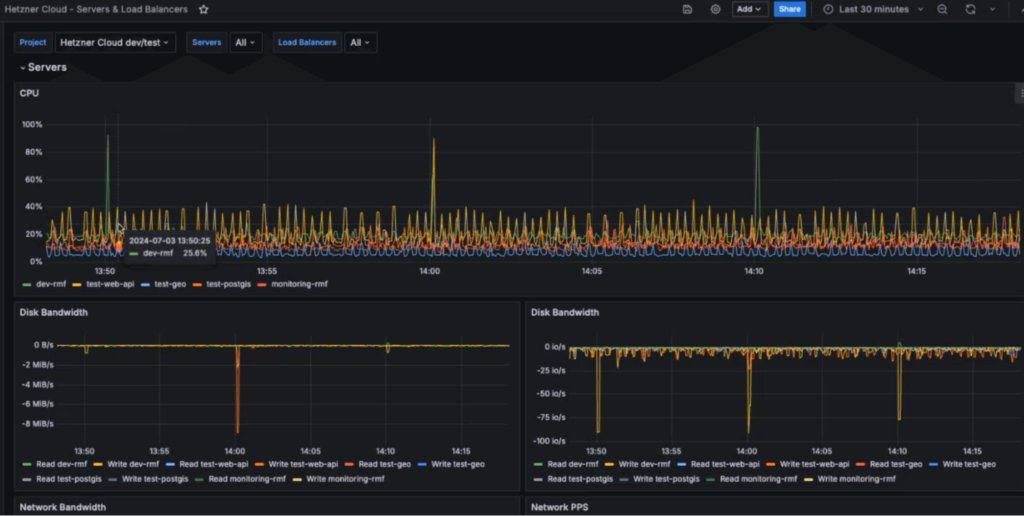
Infrastructure is where your applications run. Infrastructure monitoring tracks the performance, availability, and health of physical and virtual infrastructure components, including servers, networks, databases, and storage systems.
Server Monitoring
Servers, whether physical or virtual, need constant health checks:
- CPU load: Spikes can slow down applications.
- Memory usage: Memory leaks can crash services.
- Disk usage: Full disks prevent applications from writing data.
- Process monitoring: Detects failed processes and restarts them automatically.
Tools like Nagios, Zabbix, and Prometheus Node Exporter help collect these metrics effectively.
Abstraction Level Monitoring Detailed
Container Monitoring (Docker)
Containers have revolutionized software deployment. But their dynamic nature demands specialized monitoring.
What is Container Monitoring?
Container monitoring tracks resource utilization and performance of containerized applications. For Docker, it involves:
- CPU and memory usage per container
- Container uptime and health checks
- Network I/O for container communications
- Storage usage within containers
Why is it Important?
Unlike traditional VMs, containers share the host OS kernel, meaning resource contention can arise quickly, affecting multiple services. For example, if one container uses excessive CPU, others on the same host may suffer degraded performance.
Tools for Docker Monitoring:
- cAdvisor (Container Advisor): Developed by Google, it provides container-level resource usage and performance characteristics.
- Prometheus with cAdvisor exporter: Stores and queries container metrics efficiently.
- Grafana dashboards: Visualize container health and performance trends for quick analysis.
Monitoring Docker ensures containers run optimally without affecting other workloads, which is essential in microservices architectures.
Orchestration Monitoring (Kubernetes)
Kubernetes (K8s) automates container orchestration, but its complexity demands deep observability.
What does Kubernetes Monitoring Involve?
- Cluster health status
- Node and pod resource usage
- Deployment statuses and scaling behaviors
- Networking, service discovery, and ingress traffic
- Events and error logs within the cluster
Key Tools:
- Prometheus + kube-state-metrics: Collects metrics about cluster states, pods, nodes, and deployments.
- Grafana dashboards: Visualizes Prometheus metrics into user-friendly dashboards for DevOps teams.
- Kubernetes Dashboard: A web UI to manage and monitor clusters but limited in observability compared to Prometheus-Grafana stacks.
Kubernetes monitoring ensures application scalability, reliability, and quick issue detection across dynamically scaling pods.
Virtual Machine Monitoring
Virtual machines (VMs) are still widely used alongside containers.
What should you monitor in VMs?
- CPU, memory, and disk I/O usage
- Network latency and throughput
- Hypervisor resource allocation
- VM uptime and performance anomalies
Tools for VM Monitoring:
- Nagios & Zabbix: Traditional yet robust monitoring solutions for VM environments.
- Prometheus node exporters: Collect metrics from VMs for visualization in Grafana.
Monitoring VMs ensures stability, efficient resource allocation, and smooth performance for hosted applications.
Application Level Monitoring
Focuses on tracking the performance, availability, and user interactions of applications, providing insights into response times, error rates, and transaction flows. APM focuses on how well your application runs from the end-user perspective.
- Application Performance Monitoring (APM)
- Transaction Tracing
- User Experience Monitoring
What does APM track?
- Response times of APIs and services
- Application error rates
- Backend database query performance
- Third-party service integrations
Popular APM Tools:
- New Relic: Provides deep application insights with transaction traces.
- Datadog APM: Offers distributed tracing and performance analytics.
- Dynatrace: Uses AI-powered automation to monitor and optimize application performance.
APM helps ensure users experience fast, reliable, and error-free applications, directly impacting business revenue and user satisfaction.
Three Pillars of Monitoring
Logs – Logs record events with timestamps, creating a chronology of processes occurring within the system.
Metrics – Metrics demonstrate resource usage levels or behaviors that can be collected in systems.
Traces – Traces illustrate the journey of a user through the entire application stack.
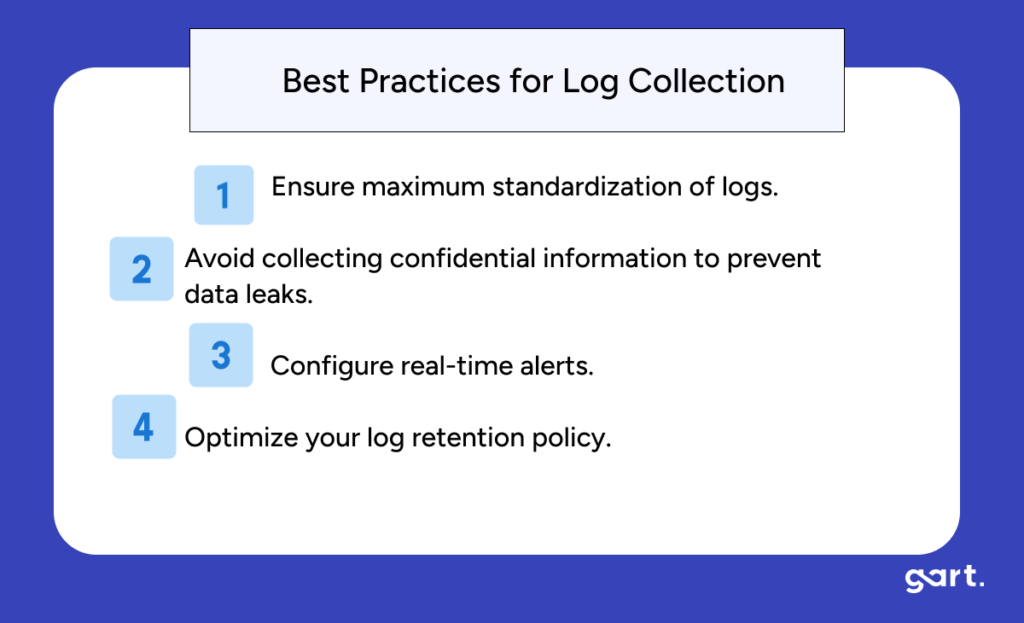
Why are logs important?
They capture detailed insights for troubleshooting. For instance, if an API fails, logs show the error type, timestamp, and potentially the root cause.
Best Practices:
- Use structured logging for easier querying.
- Avoid logging sensitive data to remain compliant.
- Centralize logs using tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Grafana Loki for faster access.
Metrics
Metrics are numerical data points representing system behaviors or statuses over time.
Examples:
- CPU utilization %
- Number of active users
- API request latency
- Database query counts
Metrics are ideal for trend analysis and alert configurations to trigger immediate actions when thresholds are breached.
Traces
Traces track the flow of requests across different services and components.
For example, an e-commerce checkout trace might involve:
- Frontend click event.
- Backend order service.
- Payment gateway integration.
- Inventory database update.
- Confirmation email service.
Tracing tools like Jaeger and Zipkin visualize this journey, making debugging distributed systems efficient.
Monitoring Tools – Choosing the Right Monitoring Stack
Grafana and Prometheus are among the most widely used, free, and open-source solutions. These tools together create a solid foundation for a robust and reliable monitoring stack, ensuring high-quality analysis.
- Grafana: This powerful visualization tool displays data from various sources in customizable dashboards, making it easier to understand and act on complex metrics.
- Prometheus: A leading open-source monitoring and alerting toolkit, known for its reliability and scalability in gathering and querying metrics.
- Grafana Loki: A log aggregation system that integrates smoothly with Grafana, allowing for comprehensive log management and analysis.

Other notable tools in the monitoring ecosystem include:
Datadog: A comprehensive monitoring and analytics platform that provides visibility into your entire tech stack, from infrastructure to applications.
New Relic: An observability platform that offers detailed insights into application performance, helping to quickly identify and resolve issues.
Cost vs Features Analysis of Monitoring Tools
Let’s simplify a comparison in a table for clarity:
| Tool | Best For | Cost Model | Key Features |
|---|---|---|---|
| Prometheus | Metrics monitoring | Free, self-hosted | Time-series metrics collection, alert manager |
| Grafana | Visualization | Free, self-hosted or SaaS | Customizable dashboards, plugins, alerting |
| Grafana Loki | Log aggregation | Free, self-hosted or SaaS | Integrates with Grafana, efficient log storage |
| Datadog | Full-stack observability | Per host / per GB ingested | APM, infrastructure, logs, security monitoring |
| New Relic | Application performance | Per user / usage-based | Distributed tracing, synthetics, browser monitoring |
Selecting your stack wisely ensures cost optimization without compromising observability.
By leveraging these tools and practices, you can create a monitoring setup that provides actionable insights, helping you to quickly respond to issues, optimize performance, and ensure the overall health of your digital solutions.
Real-World Monitoring Use Cases
1. Music SaaS Platform Case Study
Challenge:
A B2C SaaS music platform needed real-time visibility across its globally distributed infrastructure to support millions of concurrent users.
Solution:
By integrating AWS CloudWatch and Grafana, the team built dashboards displaying:
- Regional server performance metrics
- Database query performance
- API error rates
- User streaming latency per region
Impact:
- Enabled seamless scalability during peak loads (e.g., global music release days)
- Reduced operational interruptions with proactive alerts
- Improved user experience through optimized backend performance
This approach empowered the platform to grow globally while maintaining cost efficiency and high availability.
2. Digital Landfill Platform Case Study
Challenge:
The elandfill.io platform needed scalable monitoring to track landfill methane emissions across multiple countries, with regulatory compliance considerations.
Solution:
Engineered a cloud-agnostic monitoring architecture using:
- Prometheus for metrics collection
- Grafana for visualization dashboards per country operations
- Custom exporters to gather IoT sensor data for emissions tracking
Impact:
- Enhanced methane emission forecasting accuracy
- Simplified compliance with environmental standards
- Allowed flexibility in choosing cloud providers per country requirements
Robust monitoring here wasn’t just a DevOps need but a business-critical enabler for regulatory compliance and operational success.
Common Mistakes in Monitoring
Monitoring can backfire if implemented poorly. Here are frequent mistakes:
- Over-monitoring Everything
Collecting excessive data without clear purpose leads to analysis paralysis, high costs, and cluttered dashboards. Focus on metrics aligned with business KPIs and user experience. - Ignoring User Experience Metrics
Backend health doesn’t guarantee happy users. Always include frontend and user-centric metrics in your monitoring stack. - Improper Alert Configurations
Alerting on non-critical events leads to alert fatigue. Only trigger actionable alerts with well-defined escalation policies. - Neglecting Log Standardization
Inconsistent log formats across services make centralized log management chaotic and analysis time-consuming. - Failure to Test Monitoring Setup
Periodically test alerts, log pipelines, and metric exporters to ensure your monitoring setup actually works when needed.
Avoiding these mistakes ensures your monitoring efforts deliver ROI through actionable insights rather than noise.
Future of Monitoring in DevOps
AI-Powered Monitoring
The future of monitoring lies in AI and machine learning-powered solutions that:
- Analyze millions of data points rapidly
- Detect anomalies before thresholds breach
- Predict outages or performance degradation based on patterns
Tools like Dynatrace and Datadog already implement AI for automated root cause analysis and proactive remediation suggestions.
Predictive Analytics for Proactive Operations
Imagine a monitoring tool telling you,
“Your payment gateway latency is trending upwards and may breach SLA in 2 hours.”
That’s predictive analytics in action. Instead of reacting to failures, teams become proactive, fixing issues before they impact users.
As DevOps ecosystems become more complex, predictive monitoring and AI-driven observability will become non-negotiable for high-performing teams.
Conclusion
Monitoring is no longer optional in the fast-paced DevOps world. It is the eyes, ears, and nervous system of your digital solutions, ensuring seamless operations, happy users, and business growth.
To recap:
- Choose tools that align with your needs and team strengths.
- Focus on actionable metrics rather than collecting everything.
- Integrate logs, metrics, and traces for holistic observability.
- Continuously evolve your monitoring setup to match system complexity.
In DevOps, “you can’t improve what you don’t measure.” Monitoring isn’t just about preventing failures; it’s about empowering continuous improvement to build reliable, scalable, and delightful digital products.
See how we can help to overcome your challenges








