- What is PHI (Protected Health Information)?
- Who Must Comply with HIPAA?
- The Three Main Rules of HIPAA
- Penalties for Non-Compliance
- What Is a HIPAA Audit?
- What Gets Audited During a HIPAA Audit?
- Implementation and Best Practices
- HIPAA compliance checklist
- Common Mistakes to Avoid During HIPAA Audits
- Conclusion
Imagine this: You’re busy running your clinic, pharmacy, or health tech firm when suddenly an email arrives – you’re getting audited for HIPAA compliance. Panic sets in. What if your policies aren’t updated? What if employee training is outdated? What if a single misstep costs you millions in fines?
This isn’t an imaginary worst-case scenario. HIPAA audits are real, random, and rigorous. With penalties ranging from $50,000 per incident to $1.5 million per year, failing an audit can financially and reputationally cripple your business.
But here’s the good news: You can prepare in advance. This guide will break down everything you need to know in simple, practical steps to ensure you’re not just compliant on paper but audit-ready anytime.
We’ll cover:
- What HIPAA really is (without jargon)
- Who needs to comply (it’s not just hospitals)
- What gets audited
- The three main HIPAA rules
- Step-by-step HIPAA audit preparation checklist
- How to avoid common pitfalls
- How experts like Gart Solutions can help you stay secure and compliant
Ready to protect your business and your patients’ trust? Let’s dive in.
What is PHI (Protected Health Information)?
HIPAA’s main goal is to keep patients’ medical records and personal health details safe from being shared without permission. It sets nationwide rules to make sure that health information stays private, accurate, and accessible only to the right people. These rules apply to health plans, doctors, hospitals, and any businesses that handle patient information.
Protected Health Information (PHI) is any health-related data that can be traced back to a specific person. This includes things like medical records, names, social security numbers, and even fingerprints or other biometric data. HIPAA requires that all health information connected to personal details is considered PHI and must be kept secure.
The U.S. Department of Health and Human Services (HHS) has defined 18 unique identifiers that classify health information as PHI, including but not limited to:
- Names
- Dates (except years)
- Social security numbers
- Medical record numbers
- Email addresses
- Device identifiers
- Biometric data (fingerprints, face scans)
Who Must Comply with HIPAA?
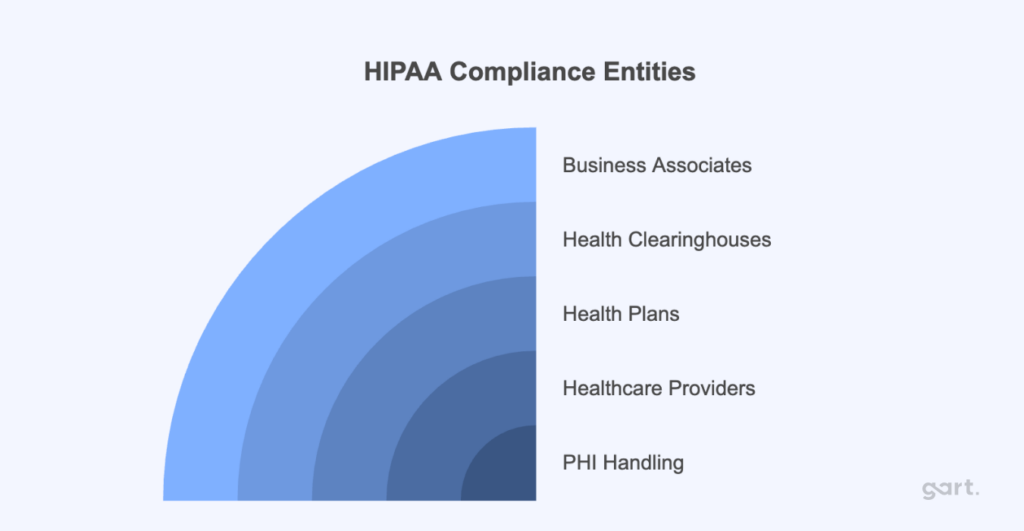
HIPAA compliance is mandatory for entities that handle PHI, including:
- Healthcare providers: Hospitals, clinics, nursing homes, pharmacies.
- Health plans: Health insurance companies, Medicare, Medicaid.
- Health clearinghouses: Organizations that process health data like billing services and data management firms.
- Business associates: Third-party vendors, including billing companies, consultants, and cloud service providers, who handle PHI on behalf of covered entities.
HIPAA compliance extends beyond healthcare providers to include business associates—third-party entities that perform services involving the use or disclosure of Protected Health Information (PHI) on behalf of covered entities like hospitals or clinics. Examples of business associates include:
- Billing companies
- Cloud service providers
- Consultants
- Transcription services
- Data storage firms
Business associates are required to ensure the same level of protection for PHI as the primary covered entities, such as hospitals and insurance companies. This means they must adhere to HIPAA’s Privacy, Security, and Breach Notification rules. If a breach occurs or there’s non-compliance, business associates face the same penalties, ranging from $50,000 fines per incident to $1.5 million annually.
Key takeaway:
If you store, process, access, or transmit PHI in any capacity, HIPAA applies to you. No exceptions.
The Three Main Rules of HIPAA
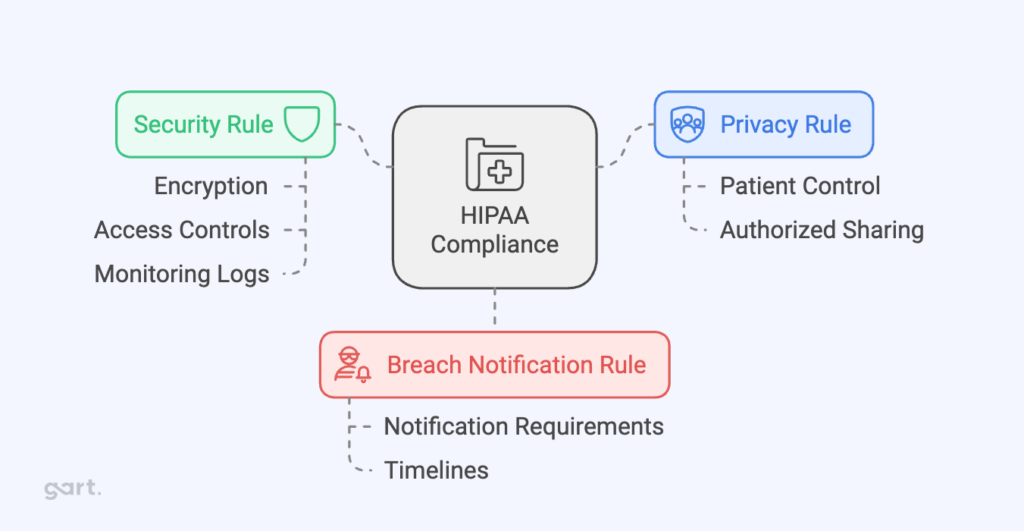
HIPAA compliance is governed by three primary rules:
Privacy Rule
This rule controls how personal health information (PHI) can be used and shared. It focuses on keeping patient information safe from unauthorized access while still allowing healthcare providers to share it when needed for treatment or running their services. It limits who can see a patient’s health information and under what conditions it can be shared, giving patients control over their personal health details.
Security Rule
This rule is about protecting electronic health information (ePHI). It requires security measures like encryption, access controls, and monitoring logs to keep data safe from breaches. Whether the data is being stored or sent, this rule ensures it is protected. It also requires healthcare organizations to have administrative, physical, and technical safeguards in place to keep electronic health data secure.
Breach Notification Rule
If there’s a breach involving unsecured health information, this rule requires healthcare providers to notify the affected individuals and, in some cases, the government and media. The individuals must be informed within 60 days if their health information was accessed without permission. If the breach is large, the Department of Health and Human Services (HHS) and the media may also need to be notified.
Penalties for Non-Compliance
Failing to comply with HIPAA can lead to severe consequences. Financial penalties range from $50,000 per incident to $1.5 million per violation category per year. Persistent violations or multiple breaches can result in multi-million-dollar fines, and in some cases, criminal charges.
Even if an organization is found to be compliant today, they may face fines for any previous deficiencies. These penalties can be financially debilitating, highlighting the importance of maintaining a thorough and consistent compliance plan.
What Is a HIPAA Audit?
A HIPAA audit is a formal assessment conducted by the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) to verify that healthcare providers, health plans, and their business associates comply with HIPAA’s privacy and security requirements.
Why do HIPAA audits happen?
- Random selection for proactive audits
- Complaints filed by patients or staff
- Data breach incidents reported to OCR
These audits are not just paperwork reviews. They evaluate your actual practices, training programs, and technical safeguards. In recent years, OCR contracted firms like FCI Federal to conduct these audits, expanding audit frequency and depth.
Types of HIPAA audits:
- Desk audits – You submit requested documentation electronically within a strict timeframe (usually 10-14 days).
- On-site audits – Auditors visit your physical office to observe operations, interview staff, and inspect security practices.
If deficiencies are found, you may be required to submit a Corrective Action Plan (CAP) and could face monetary penalties depending on severity.
Key takeaway:
A HIPAA audit tests your real-world compliance, not just your written policies.
What Gets Audited During a HIPAA Audit?
Auditors review both current and historical compliance efforts, meaning that even if you updated policies last week, outdated practices from last year can still lead to penalties.
Areas commonly audited:
- Privacy policies and procedures: Are they up to date and aligned with HIPAA standards?
- Security risk assessment reports: Have you identified and addressed vulnerabilities in your systems?
- Employee training records: Has your staff been trained regularly on HIPAA requirements?
- Business Associate Agreements (BAAs): Are they signed, current, and compliant with HIPAA rules?
- Breach notification procedures: Do you have a documented and tested plan in place?
- Technical safeguards: Encryption, access controls, audit logs, and authentication systems.
- Physical safeguards: Locked storage, secure facility access, workstation security policies.
- Incident response plans: Are you prepared to handle and report breaches effectively?
What is the auditor looking for?
They want proof that:
- You understand HIPAA requirements
- You have implemented policies, procedures, and safeguards
- Your team is trained and compliant
- You maintain documentation to demonstrate compliance
Failure to provide these quickly can trigger deeper investigations or fines.
Implementation and Best Practices
HIPAA compliance requires organizations to adopt several best practices, including:
- Employee Training: All employees handling PHI must be thoroughly trained on HIPAA policies and procedures.
- Risk Management: Organizations should regularly assess risks to PHI and take necessary steps to mitigate them.
- Access Control: Only authorized personnel should have access to PHI, ensuring that medical information is protected from unauthorized access.
HIPAA compliance checklist
Common Mistakes to Avoid During HIPAA Audits
Even organizations with good intentions fail audits due to avoidable errors. Here are critical mistakes to avoid:
- Incomplete risk assessments – Simply checking boxes without thorough evaluation.
- Outdated policies – Using templates created years ago without updates.
- No employee training records – Failing to document who attended HIPAA training and when.
- Unencrypted data – Storing PHI in cloud or local systems without proper encryption.
- Weak password policies – Allowing default passwords or sharing logins.
- Missing BAAs – Working with vendors handling PHI without signed Business Associate Agreements.
- Ignoring small breaches – Failing to document or notify minor unauthorized disclosures.
- No audit logs – Lack of monitoring for who accesses PHI and when.
Avoid these pitfalls by conducting internal audits regularly, keeping policies current, and working with compliance experts who can identify gaps before OCR finds them.
How Gart Solutions Can Help with HIPAA Audits
Preparing for a HIPAA audit isn’t just about checking off compliance boxes – it’s about implementing security and privacy best practices that protect your patients and your business long-term. This is where Gart Solutions comes in.
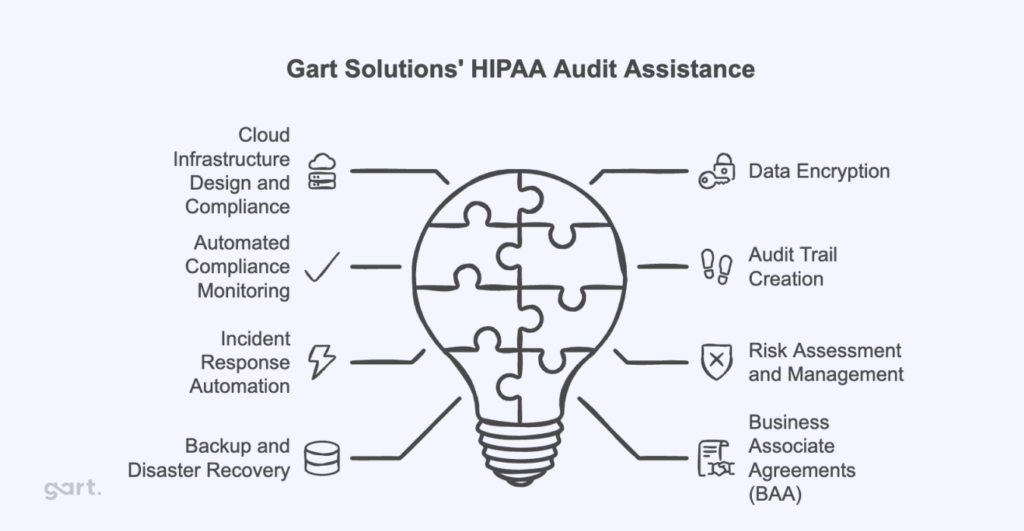
Here’s how Gart Solutions can support your HIPAA compliance:
- Cloud Infrastructure Design
Design and deploy cloud environments compliant with HIPAA standards, ensuring scalable and secure PHI storage.
Cloud Infrastructure Design
Design and deploy cloud environments compliant with HIPAA standards, ensuring scalable and secure PHI storage. - Data Encryption Implementation
Encrypt sensitive data in transit and at rest to prevent unauthorized access. - Automated Compliance Monitoring
Use DevOps practices to continuously scan for misconfigurations and vulnerabilities, resolving them in real time. - Audit Trail Creation
Deploy logging and monitoring tools to track system activity and demonstrate compliance during audits. - Incident Response Automation
Develop automated procedures to minimize breach impact and ensure fast compliance with HIPAA breach notification rules. - Risk Assessment and Management
Conduct thorough risk assessments, implement remediation plans, and monitor for ongoing compliance. - Backup and Disaster Recovery
Set up secure backup systems and disaster recovery plans to ensure data is always recoverable. - Business Associate Agreements (BAA) Management
Help draft and maintain compliant BAAs with cloud vendors and business associates.
By partnering with Gart Solutions, you not only prepare for HIPAA audits but also build a resilient and secure IT environment that earns your patients’ trust and protects your business.
Gart Solutions can design and implement cloud infrastructure that adheres to HIPAA security and privacy standards. This includes ensuring that the architecture is secure, scalable, and meets the technical safeguards required for protected health information (PHI) handling.
One of the core requirements for HIPAA compliance is ensuring that sensitive data, such as PHI, is encrypted both in transit and at rest. Gart Solutions can implement encryption protocols on cloud services, ensuring that all data is protected from unauthorized access.
Using DevOps practices, Gart Solutions can automate the monitoring of cloud environments for HIPAA compliance. By setting up automated scans and alert systems, they can ensure that any misconfigurations or potential breaches are identified and resolved in real-time.
HIPAA requires that organizations maintain a record of access and activity for all systems handling PHI. Gart Solutions can deploy logging and monitoring tools to ensure a robust audit trail. This makes it easier to demonstrate compliance during an audit.
In case of a security incident, a fast and effective response is critical. Gart Solutions can automate incident response procedures, minimizing response time and ensuring that any HIPAA violations are addressed immediately.
Gart Solutions can conduct regular risk assessments, helping organizations identify vulnerabilities in their cloud infrastructure. They can then implement remediation plans and continuously monitor the environment to reduce the risk of non-compliance.
HIPAA requires that organizations have plans for backup and disaster recovery in place. Gart Solutions can set up automated, secure backups and disaster recovery solutions, ensuring that data is always recoverable and protected from loss.
For any cloud services provided to healthcare organizations, a BAA is required to establish responsibilities for HIPAA compliance. Gart Solutions can help navigate the process of drafting and maintaining BAAs with cloud vendors, ensuring proper legal protection and compliance.
These services ensure that organizations meet HIPAA requirements while maintaining efficient, secure cloud operations.
Conclusion
HIPAA serves as a cornerstone of healthcare privacy and security regulations, ensuring that individuals’ health data is protected. Healthcare providers, insurance companies, and associated businesses must understand and adhere to HIPAA’s rules to avoid heavy penalties and safeguard patient trust.
See how we can help to overcome your challenges








