FISMA, or the Federal Information Security Modernization Act, was created in 2002 in response to the 9/11 attacks and growing cybersecurity threats. It’s a law that requires government agencies and private companies working with the government to protect their information systems from cyber threats.
FISMA applies to federal agencies, their contractors, and organizations that receive federal grants. If your system handles federal data, you must comply.
Enforcement has become stricter, especially with recent security breaches in systems that fall under FISMA’s “moderate” classification.
Avoid over-classifying your data. Labeling data as too “high-risk” can make audits more expensive and complicated than necessary.
Fedir Kompaniiets, CEO Gart Solutions
FISMA’s Origins (2002)
The 2002 version of FISMA was introduced to help the U.S. government transition from paper-based systems to digital ones. As the government upgraded its IT infrastructure, there was a need for a law to make sure that both government data and systems were well-protected.
FISMA doesn’t just apply to government agencies—it also includes contractors that handle systems for federal agencies, ensuring that any government-related data is shielded from cyber threats.
The law focuses on three key things: keeping data confidential, maintaining its accuracy, and ensuring that systems are available when needed. It shifted the focus from physical security measures (like locked file cabinets) to stronger digital protections.
FISMA is essential for protecting critical government operations and sensitive information, such as Social Security numbers.
2014 Modernization of FISMA
The 2014 FISMA update built on the original law, focusing on better reporting and faster responses to cybersecurity breaches.
A key change was giving the Department of Homeland Security (DHS) a lead role in setting cybersecurity guidelines for federal agencies. DHS, through its Cybersecurity and Infrastructure Security Agency (CISA), continues to push initiatives like Zero Trust Architecture to strengthen federal cybersecurity. They can also issue Binding Operational Directives (BODs), which require agencies to quickly fix serious vulnerabilities that could impact the entire federal infrastructure.
The update also introduced mandatory rules for reporting cyber breaches. Now, federal civilian agencies must notify DHS whenever a security incident happens. This helps the government react faster to threats and fix weaknesses.
Overall, FISMA 2014 highlights the importance of real-time reporting to catch and address cybersecurity threats as quickly as possible across all federal agencies.
Risk Management and Security Controls
One of the central requirements under FISMA is that federal agencies must conduct risk assessments to evaluate the level of security needed for their information systems. They must follow a Risk Management Framework (RMF), which includes:
- Categorizing systems based on the sensitivity of data (low, moderate, or high).
- Selecting security controls according to guidelines from the National Institute of Standards and Technology (NIST), particularly the Federal Information Processing Standards (FIPS) 200 and the NIST SP 800-53 controls catalog.
Agencies are required to implement these security controls and conduct annual compliance checks to ensure continuous security.
The Compliance Process: Challenges and Best Practices
Gap Analyses
Rich explains that many clients come to Lifeline Data Centers after performing a gap analysis, which reveals areas of non-compliance. This often includes insufficient two-factor authentication, inadequate intrusion detection, or poor remote management capabilities.
System Security Package (SSP)
Developing an SSP is one of the most time-consuming steps in the compliance process. This document can run 400-500 pages and details every aspect of the system, including configurations, license keys, and change management processes.
Audits and Assessments
External auditors are required to validate compliance. This involves checking controls, verifying physical security, and ensuring availability. Costs can run high, especially for FedRAMP, where continuous monitoring is required annually.
FISMA vs FedRAMP vs NIST 800-53
What is FedRAMP?
FedRAMP, which stands for the Federal Risk and Authorization Management Program, was launched in 2011 to help the federal government move to cloud services. It creates a standard way to assess, monitor, and approve Cloud Service Providers (CSPs), like companies offering SaaS, PaaS, or IaaS solutions to government agencies.
Unlike FISMA, where each agency gives its own authorization, a FedRAMP authorization allows a cloud service provider to work with multiple federal agencies after going through a one-time, but much more thorough, approval process.
The goal of FedRAMP is to simplify and speed up the approval of cloud services while ensuring that they meet strict security standards, helping government agencies confidently adopt cloud-based systems.
Key Differences from FISMA:
- Focus: FedRAMP is designed for cloud services, including SaaS, PaaS, and IaaS providers, who store or process federal data.
- Standardization: Unlike FISMA, which requires separate ATOs for each federal agency, FedRAMP allows CSPs to achieve a single ATO that can be used across multiple agencies.
- Assessment: CSPs must undergo rigorous assessments from Third-Party Assessment Organizations (3PAOs), which are federally authorized to conduct audits.
What is NIST 800-53?
NIST 800-53 is a detailed set of security guidelines created by the National Institute of Standards and Technology (NIST) to protect federal information systems. It’s used as a framework by both FISMA and FedRAMP to ensure that security controls are in place.
While NIST 800-53 doesn’t provide a certification on its own, companies working toward FISMA or FedRAMP compliance need to follow its recommendations. Auditors use NIST 800-53 as a guide when checking if an organization is meeting the required security standards.
NIST 800-53 goes beyond FISMA and FedRAMP, offering frameworks for other regulations like the NIST Cybersecurity Framework (CSF) and NIST 800-171, which covers how to handle controlled unclassified information (CUI).
Both FISMA and FedRAMP heavily depend on NIST 800-53’s security controls. However, while the guidelines are clear, they can be open to interpretation, making audits more complex depending on how the standards are applied.
Key Differences and Similarities
Here’s a table that outlines the differences between FISMA, FedRAMP, and NIST 800-53:
| Aspect | FISMA | FedRAMP | NIST 800-53 |
|---|---|---|---|
| Target Audience | Federal agencies, state agencies handling federal programs, private companies working with federal data. | Third-party cloud service providers (CSPs) working with federal agencies. | Any federal agency or organization operating critical infrastructure and handling sensitive information. |
| Certification Process | Requires separate Authority to Operate (ATOs) for each federal agency a company works with. | One-time ATO allows companies to work with multiple agencies after authorization is granted. | No direct certification, but acts as a guide for audits and assessments across various frameworks. |
| Nature | A law mandating security protocols for agencies and contractors. | A program designed to streamline cloud service security for federal agencies. | A standards organization that creates the frameworks used by both FISMA and FedRAMP. |
Similarities:
- Focus on Security: All three frameworks are centered on securing federal information systems, with a specific focus on protecting U.S. government data.
- Enabling Business with the Government: By achieving compliance with these frameworks, companies can do business with the federal government, making them critical for companies seeking government contracts.
- Private Sector Adoption: Although these frameworks are primarily for federal agencies and contractors, they have become widely adopted in the private sector due to their comprehensive security requirements. Many companies voluntarily adopt FISMA, FedRAMP, or NIST controls to strengthen their cybersecurity posture.
How Gart Solutions Can Help with Your FISMA Audit
At Gart Solutions, we specialize in DevOps, cloud, and infrastructure services, and we’re here to help you navigate the often complex world of FISMA compliance.
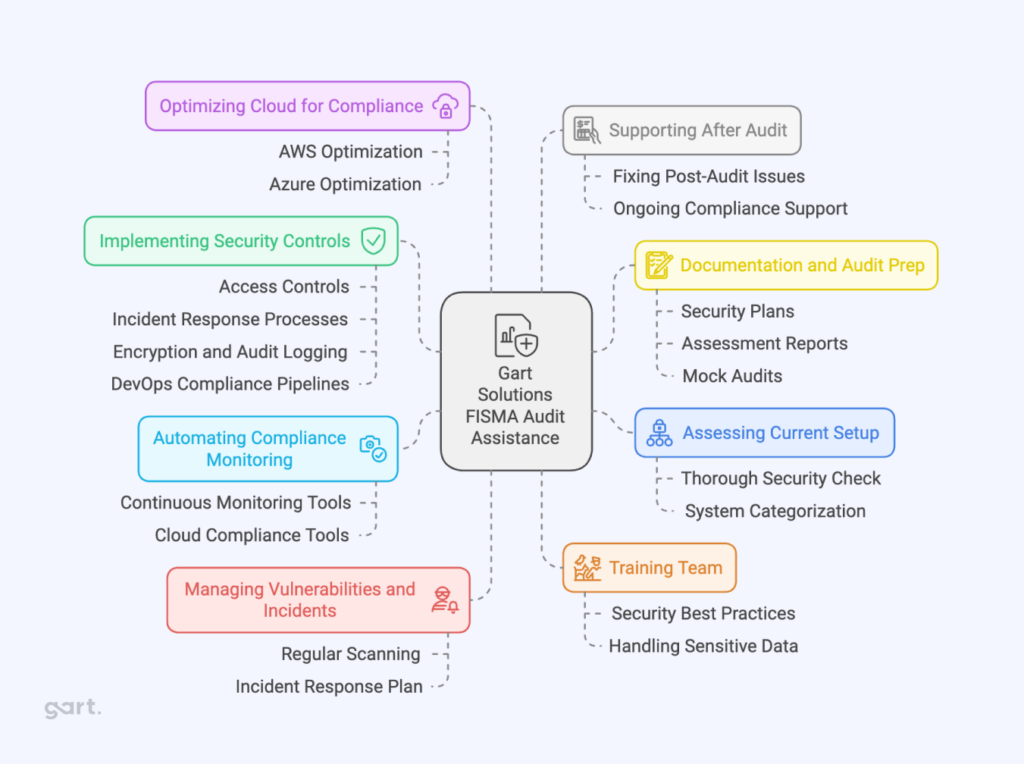
Here’s how we can make your FISMA audit process easier:
1. Assessing Your Current Setup
We start by doing a thorough check of your current security practices to see how they stack up against FISMA requirements. We’ll help you figure out what’s missing or needs improvement.
We’ll also help you categorize your systems based on their risk level (low, moderate, or high), which is a key step in getting the right controls in place.
2. Automating Compliance Monitoring
We set up tools that continuously monitor your systems for security risks, vulnerabilities, and updates. This makes sure you’re always audit-ready, and reduces the manual work involved in staying compliant.
If you’re in the cloud, we ensure your setup follows both FISMA and FedRAMP standards, with automated tools to keep everything secure and up to date.
3. Implementing Security Controls
We help you put the necessary security controls in place, like controlling who can access your systems, setting up incident response processes, and using encryption and audit logging.
For companies using DevOps, we build pipelines that have compliance baked in, so that all software and infrastructure changes meet FISMA requirements from the start.
4. Helping with Documentation and Audit Prep
We’ll make sure you have all the necessary documents ready for the FISMA audit, such as Security Plans and Assessment Reports.
To get you fully prepared, we can even run mock audits to help your team get comfortable with the process before the real thing.
5. Managing Vulnerabilities and Incidents
We regularly scan your systems for security risks and quickly address any vulnerabilities we find, helping you avoid security issues before they become problems.
We’ll also help you set up an incident response plan so you can react fast to any security breaches, meeting FISMA’s requirements for reporting and handling incidents.
6. Optimizing Your Cloud for Compliance
If your systems are in the cloud (like AWS or Azure), we’ll make sure your infrastructure is optimized for FISMA compliance, using the right cloud security tools to keep everything secure and audit-ready.
8. Supporting You After the Audit
After your audit, if any issues are flagged, we’ll help you fix them quickly to get you fully compliant.
We also offer ongoing support to help you maintain compliance, regularly reviewing your security controls and keeping you updated on any changes to FISMA regulations.
FISMA Audie Checklist
Why Choose Gart Solutions?
- We Know the Rules: We have deep experience with federal security standards like NIST 800-53 and FISMA, so we can help you meet those requirements without the headache.
- We Handle Everything: From assessing your current setup to post-audit support, we’ve got you covered.
- We Automate the Hard Parts: Our automation tools make compliance less manual and more reliable, saving you time and reducing errors.
- Cloud Experts: Whether you’re in the cloud or on-prem, we’ll make sure your systems are secure and meet all FISMA and FedRAMP standards.
With Gart Solutions by your side, you can feel confident that your organization will be ready for the FISMA audit and stay compliant long-term, keeping your systems safe and secure.
See how we can help to overcome your challenges









