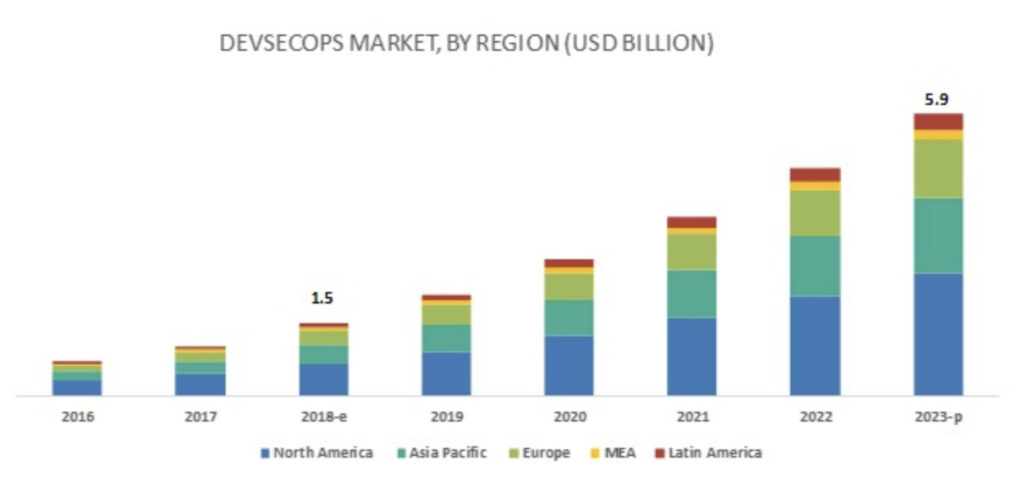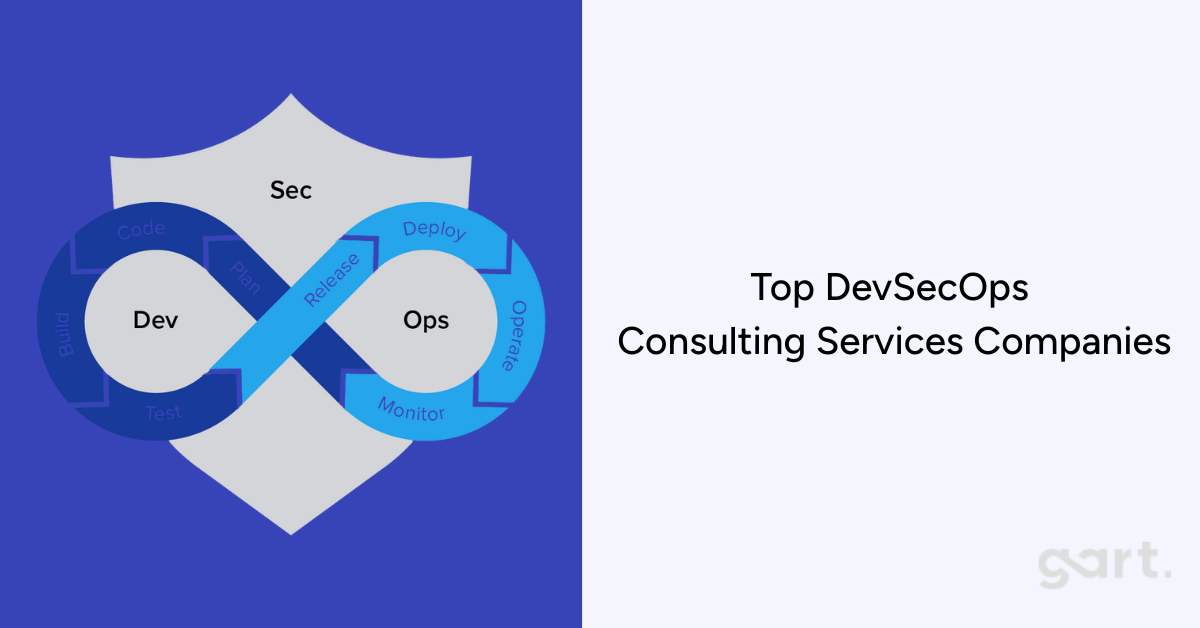
Cyberattacks in 2026 aren't just about ransomware anymore. They're smarter, faster, and deeply embedded in software supply chains. That’s why companies today are going beyond traditional DevOps. They're integrating security into every part of the development lifecycle — and that approach has a name: DevSecOps.
DevSecOps isn't just a methodology — it's a culture shift, a set of tools, and a leadership strategy that treats security as a first-class citizen in software delivery. In a world where regulations are tighter, cloud environments are more complex, and software teams are deploying multiple times per day, DevSecOps has become non-negotiable.
This article brings you a hand-picked, in-depth look at the top DevSecOps consulting service providers in 2026, ranging from global tech giants to highly specialized regional firms. Each one is evaluated based on technical capabilities, real-world use cases, security integrations, Clutch reviews, and industry relevance.
Whether you're a fast-moving SaaS startup, a fintech firm protecting sensitive transactions, or a healthcare company under HIPAA pressure, these providers will help you secure your pipelines — without slowing down innovation.
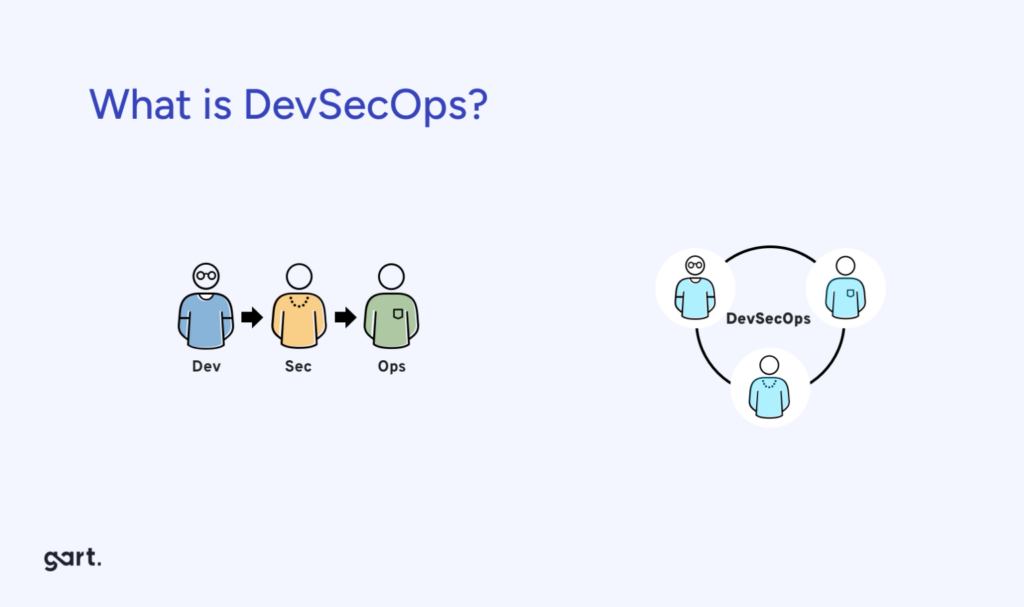
What is DevSecOps?
DevSecOps stands for Development, Security, and Operations. It's an evolution of DevOps that ensures security is embedded into every stage of the software delivery process, not bolted on at the end.
It addresses one of the biggest problems in modern tech: the disconnect between speed and safety. Traditional development pushes for faster releases. Security, on the other hand, often slows things down. DevSecOps bridges this gap by:
Integrating security tools directly into CI/CD pipelines
Automating vulnerability scans
Using policy-as-code to enforce secure practices
Enabling real-time threat modeling
Empowering developers to write secure code from day one
In short, DevSecOps ensures your code, infrastructure, and teams are resilient — even at scale.
Why DevSecOps Matters in 2026
Let’s be real: cybersecurity isn’t optional anymore. With cloud-native systems, containerized deployments, and APIs running across borders, companies face complex, multi-layered threats.
In 2026:
Software supply chain attacks are up by 300%
Dev teams ship code 40x faster than 2018
Regulations like GDPR, HIPAA, ISO 27001, SOC 2, and NIS2 demand security baked into software, not stapled on later
This is where DevSecOps shines. It:
Reduces vulnerabilities early, saving millions in potential breach costs
Builds a culture of shared responsibility between devs, ops, and sec
Automates security compliance through tools and scripts
Prevents reputational damage and regulatory penalties
Companies using DevSecOps experience:
60% fewer production incidents
80% faster security fixes
70% reduction in audit-related delays
How We Chose the Top DevSecOps Companies
To rank the best consulting companies for DevSecOps in 2026, we used a balanced evaluation approach focused on:
Evaluation Criteria:
Clutch ratings and reviews (4.7+ only)
Years of experience in DevOps & AppSec integration
Expertise in cloud-native, Kubernetes, and IaC security
Usage of modern tools like Snyk, Prisma Cloud, Checkmarx, etc.
Real-world case studies and client results
Focus on regulated industries like finance, healthcare, SaaS
Ability to scale from startups to enterprise-level implementations
Let’s dive into the leaders…
1. Gart Solutions
Clutch Rating: 4.9/5Specialties: GitOps, Kubernetes Security, DevOps & DevSecOps Consulting
Gart Solutions has emerged as one of the most reliable DevSecOps consulting partners in 2026. Based in Georgia but serving clients worldwide, Gart combines deep cloud-native expertise with secure-by-design DevOps architectures.
Their consultants are known for integrating security into CI/CD pipelines, Infrastructure-as-Code (IaC), and Kubernetes clusters. What makes Gart unique is their developer-first mindset. They don’t just patch vulnerabilities; they redesign workflows so that developers can avoid creating them in the first place.
From fintech startups to healthcare platforms, Gart has consistently delivered secure pipelines, automated compliance audits, and hands-on threat modeling as part of their CTO-level advisory services.
Why Choose Gart Solutions:
GitOps-first approach with security enforcement
DevSecOps for startups, SaaS, and cloud-native apps
Excellent documentation and real-time collaboration tools
Strong presence in Eastern Europe and U.S. markets
If you want DevOps that’s secure by default, Gart Solutions delivers at every layer.
2. Snyk
Clutch Rating: 4.8/5Specialties: Developer Security, Container & IaC Scanning, Open Source Protection
Snyk isn’t just a tool — it’s a DevSecOps movement. As of 2026, Snyk remains a leader in developer-centric security with consulting arms that help organizations build DevSecOps from the inside out.
They specialize in SCA (software composition analysis), SAST (static analysis), and IaC security, all built for developer adoption. Snyk’s consulting services include CI/CD integrations, secure coding training, and pipeline hardening.
They work well with modern stacks like Node.js, Python, Kubernetes, and Terraform — and integrate seamlessly with GitHub, GitLab, Bitbucket, and Azure DevOps.
Why Choose Snyk Consulting:
Developer-first DevSecOps tooling
Seamless integrations with modern CI/CD
Active risk posture dashboards and compliance support
AI-driven vulnerability remediation assistance
Ideal for cloud-native dev teams that need to scale security without slowing down engineering velocity.
3. Prisma Cloud by Palo Alto Networks
Clutch Rating: 4.7/5Specialties: Full-stack Cloud Security, Code-to-Cloud Visibility, Compliance Automation
Prisma Cloud by Palo Alto Networks has become a cornerstone of DevSecOps architecture for enterprise environments. As cloud security grows more complex, Prisma Cloud helps organizations secure every layer — from the codebase to cloud runtime — all within a single unified platform.
Their consulting services are designed for organizations seeking end-to-end DevSecOps enablement. This includes:
Infrastructure-as-Code (IaC) security (Terraform, CloudFormation)
Container and Kubernetes workload protection
Cloud Identity & Access Management (IAM) analysis
Compliance-as-code implementation
Prisma Cloud’s consultants help companies align with regulations like PCI-DSS, HIPAA, GDPR, and SOC 2 by automating real-time policy enforcement.
Why Choose Prisma Cloud Consulting:
Ideal for multi-cloud and hybrid cloud DevSecOps
Strong policy engine for continuous compliance
Visibility from development to production
Tight integration with CI/CD pipelines and SCMs
For enterprises needing broad cloud visibility with granular security, Prisma Cloud is the gold standard in 2026.
4. Checkmarx
Clutch Rating: 4.8/5Specialties: SAST, SCA, Developer Security Training, CI/CD Scanning
Checkmarx has long been one of the most respected names in secure application development, and their DevSecOps consulting services reinforce that reputation in 2026.
Their strength lies in empowering developers to detect and fix vulnerabilities at the source, using automated tools like:
Static Application Security Testing (SAST)
Software Composition Analysis (SCA)
API Security Testing
Developer-focused secure coding education
Checkmarx consultants work hand-in-hand with DevOps teams to implement shift-left security practices. They also help configure CI/CD environments to fail builds on critical vulnerabilities and integrate code scanning at every touchpoint.
If you're trying to build a culture of secure coding, Checkmarx is the right partner to harden your pipelines without hindering development speed.
5. Cycode
Clutch Rating: 4.8/5Specialties: SCM Security, CI/CD Governance, Secrets Management, Pipeline Integrity
Cycode is one of the fastest-growing names in the DevSecOps ecosystem — and for good reason. Their consulting services are tailor-made for companies looking to secure the software supply chain, which remains one of the most targeted and vulnerable areas in modern DevOps.
They help organizations implement:
Pipeline-as-Code governance
Secrets detection and remediation
Source control protection (GitHub, GitLab, Bitbucket)
Risk scoring across your entire DevSecOps toolchain
Cycode is designed with modern development in mind, offering zero-friction integrations and a single-pane-of-glass dashboard for all AppSec activities.
If your goal is to secure your code from the moment it’s committed to the moment it’s deployed, Cycode gives you the visibility and tools to make it happen.
6. ArmorCode
Clutch Rating: 4.7/5Specialties: AppSec Posture Management, Security Orchestration, Toolchain Unification
ArmorCode has emerged as a game-changer in the DevSecOps orchestration space. In 2026, the biggest AppSec problem isn’t lack of tools — it’s lack of coordination. That’s where ArmorCode comes in, helping companies centralize and automate security workflows across teams, tools, and environments.
Their consultants help unify all your AppSec tooling (Snyk, Checkmarx, Prisma, SonarQube, etc.) into a single visibility and orchestration layer. They also implement:
Security posture dashboards
Policy-based automation triggers
Third-party risk management
It’s especially useful for large teams managing multiple products or dev teams spread across geographies.
ArmorCode is ideal for companies drowning in disconnected security alerts who need clarity, structure, and speed.
7. JFrog
Clutch Rating: 4.8/5Specialties: Artifact Scanning, DevSecOps for Binary Management, Continuous Delivery Security
JFrog is best known for revolutionizing artifact management through JFrog Artifactory, but their DevSecOps product — JFrog Xray — takes things a step further by embedding security into the heart of your binary lifecycle.
Their consulting services focus on:
End-to-end supply chain security
Package vulnerability scanning in build artifacts
Real-time security enforcement in CD pipelines
Integration with Jenkins, GitLab, DockerHub, and Kubernetes
JFrog’s team also helps optimize software bill of materials (SBOM) compliance, making them a top pick for companies preparing for government or industry regulation.
If your DevSecOps goals revolve around release integrity and package security, JFrog delivers an essential layer of protection.
8. ThreatModeler
Clutch Rating: 4.7/5Specialties: Threat Modeling Automation, Shift-Left Risk Analysis, Secure Architecture Design
ThreatModeler has carved out a unique space in the DevSecOps world by addressing a crucial — but often neglected — practice: proactive threat modeling. Their platform and consulting services help teams identify potential vulnerabilities early in the SDLC, long before they become costly problems.
In 2026, security-aware architecture is no longer a “nice-to-have.” ThreatModeler provides automated threat modeling tools integrated directly into the DevOps toolchain — GitHub, Jira, Jenkins, Azure DevOps, and more — to make security planning a repeatable, automated process.
Why Choose ThreatModeler:
Reduces DevSecOps friction with visual threat diagrams
Supports compliance initiatives by identifying policy gaps
Helps establish security as code alongside infrastructure as code
Improves security ownership across product teams
If you're a CTO or VP of Engineering looking to embed security thinking at the architecture level, ThreatModeler makes DevSecOps both visual and scalable.
9. Wipro Cybersecurity & DevSecOps
Clutch Rating: 4.7/5Specialties: Enterprise DevSecOps, Compliance, IAM, Cloud-Native Security
Wipro brings serious enterprise muscle to the DevSecOps space. With decades of experience in IT services and security consulting, their Cybersecurity & DevSecOps division has grown into a full-stack solution provider for complex, global organizations.
Wipro’s consultants specialize in helping companies modernize and secure their entire delivery pipeline — from development to production. They bring robust frameworks that align with ISO 27001, NIST, GDPR, PCI-DSS, and HIPAA, especially for clients in regulated industries like finance, telecom, and healthcare.
Their offerings include:
DevSecOps maturity assessments
Pipeline orchestration with security enforcement
Secure secrets management and identity access policies
Cloud-native workload protection
If your organization spans multiple regions and compliance regimes, Wipro brings both strategy and execution for scalable DevSecOps adoption.
10. Capgemini
Clutch Rating: 4.6/5Specialties: Infrastructure-as-Code Security, CI/CD Governance, Automated Compliance
Capgemini is a globally recognized leader in digital transformation — and their DevSecOps consulting services reflect their strengths in complex enterprise modernization.
They specialize in embedding security policies into Infrastructure-as-Code (IaC) and CI/CD pipelines, particularly in highly regulated verticals like banking, insurance, government, and energy. Their consultants guide clients through:
Policy-as-code adoption using Open Policy Agent (OPA)
Security integration in Terraform, Azure ARM, and AWS CDK
Implementation of Zero Trust frameworks
Full-stack DevSecOps automation using open-source and enterprise tools
Capgemini is a great fit for organizations that need to move away from legacy security models and implement repeatable DevSecOps governance.
If you’re looking to standardize DevSecOps practices across large teams, projects, and clouds, Capgemini brings the structure and stability your enterprise needs.
Top 30 DevSecOps Consulting Services Companies in 2026
#CompanyRegion / HQKey SpecializationClutch Rating1Gart SolutionsUkraine / EuropeGitOps, DevSecOps for startups, Kubernetes security⭐ 4.92SnykUK / GlobalDeveloper-first security, SCA, container & IaC scanning⭐ 4.83Prisma CloudUSA / GlobalCode-to-cloud security, compliance automation⭐ 4.74CheckmarxIsrael / GlobalStatic code analysis, open-source scanning, CI/CD integration⭐ 4.85CycodeUSA / GlobalSoftware supply chain security, pipeline governance⭐ 4.86ArmorCodeUSAAppSec posture management, security workflow orchestration⭐ 4.77JFrog (Xray)Israel / USAArtifact-level DevSecOps, SBOM & binary analysis⭐ 4.88ThreatModelerUSAAutomated threat modeling, secure architecture planning⭐ 4.79WiproIndia Enterprise-grade DevSecOps, compliance-driven pipelines⭐ 4.710CapgeminiFrance / GlobalInfra-as-code security, large-scale DevSecOps governance⭐ 4.611SoftServeUkraineCloud-native DevSecOps, Zero Trust, enterprise threat detection⭐ 4.812EleksUkraineAI-enhanced DevSecOps, real-time monitoring⭐ 4.813DevinitiPolandISO 27001-certified, Atlassian + DevSecOps consulting⭐ 4.714BairesDevLATAM / USAAgile DevSecOps for SaaS, compliance automation⭐ 4.915Tata Consultancy Services (TCS)IndiaMulti-industry DevSecOps, IAM integration, hybrid clouds⭐ 4.716KPMG Cyber AdvisoryGlobalDevSecOps risk consulting, governance integration⭐ 4.717EY DevSecOps ServicesGlobalSecurity architecture, audit-aligned DevSecOps for enterprises⭐ 4.718Aqua SecurityIsrael / GlobalContainer runtime protection, cloud-native application security⭐ 4.819Sonatype (Nexus)USASoftware supply chain management, automated OSS governance⭐ 4.720Redscan (Kroll)UK / GlobalDevSecOps penetration testing, threat modeling⭐ 4.821DXC TechnologyUSA / GlobalHybrid cloud security, IaC automation⭐ 4.622CiklumUkraine / GlobalCI/CD security, startup and enterprise DevSecOps integration⭐ 4.723Accenture SecurityGlobalLarge-scale digital security transformation & DevSecOps⭐ 4.624DevSecOps.ioUSA / RemoteFully managed DevSecOps consulting and delivery⭐ 4.825KonektiaPoland / EUSecure cloud migration, DevSecOps for SMBs⭐ 4.726Contino (by Cognizant)UK / USADevSecOps transformation for regulated enterprises⭐ 4.727CyberArkIsrael / GlobalSecrets management, secure access pipelines⭐ 4.828HashiCorp Consulting PartnersGlobalSecure IaC, Vault integration, OPA/Policy-as-code⭐ 4.729VeracodeUSA / GlobalApplication security, integrated AppSec tooling⭐ 4.830StackHawkUSADevSecOps DAST (Dynamic App Security Testing) for dev teams⭐ 4.7Top 30 DevSecOps Consulting Services Companies in 2026
Benefits of Hiring a DevSecOps Consultant
In a world where speed and security are no longer mutually exclusive, hiring a DevSecOps consultant is no longer a luxury — it’s a strategic advantage. Here’s why smart companies in 2026 are investing in external DevSecOps expertise:
1. Security by Design
Consultants help you embed security into every layer — from code to cloud. They implement secure defaults, enforce compliance, and design secure infrastructure that scales.
2. Accelerated Time to Market
DevSecOps isn’t about slowing you down. In fact, it’s the opposite. By catching issues early in the pipeline, you reduce production bugs, breaches, and rework, leading to faster, safer releases.
3. Risk & Compliance Management
Whether you’re subject to GDPR, HIPAA, SOC 2, ISO 27001, or NIS2, a DevSecOps consultant ensures your CI/CD pipelines meet security and audit requirements — automatically.
4. Toolchain Integration
From Snyk to Checkmarx, from GitHub Advanced Security to Prisma Cloud, the right consultant helps select, integrate, and automate tools that work with your stack.
5. Training & Culture Change
Consultants don’t just install tools — they train your developers, security teams, and DevOps engineers to think “security-first” without friction.
In short: a great DevSecOps consultant turns your team into a self-sufficient, security-aware delivery machine.
DevSecOps Use Cases by Industry
DevSecOps isn’t one-size-fits-all. Here’s how it brings value across industries:
IndustryDevSecOps ValueFintechSecure APIs, compliance automation (PCI-DSS, SOX), transaction encryptionHealthcareHIPAA compliance, PHI protection, secure patient platformsSaaS & StartupsCI/CD hardening, rapid MVP releases with baked-in securityRetail & eCommerceSecure payment gateways, fraud detection systems, API protectionGovernment & DefenseZero Trust frameworks, secure infrastructure-as-codeTelecomSecure edge networks, compliance-driven infrastructure reviewsDevSecOps Use Cases by Industry
No matter your vertical, DevSecOps delivers measurable ROI by reducing risk while supporting agility.
DevSecOps Trends for 2026–2028
Looking ahead, DevSecOps is not slowing down — it’s evolving fast. Here are key trends shaping the future:
1. AI-Powered DevSecOps
Expect AI to write secure code suggestions, detect anomalies in pipelines, and recommend real-time fixes. AI assistants will become standard in CI/CD security checks.
2. Policy-as-Code Everything
Security policies (e.g., access controls, deployment permissions, compliance rules) are being codified using tools like OPA (Open Policy Agent) and Rego. Expect this to be default in enterprise pipelines by 2028.
3. Cloud-Native DevSecOps Toolchains
From Kubernetes security policies (OPA Gatekeeper) to container scanning in build pipelines, cloud-native DevSecOps will dominate as serverless and microservices adoption grows.
4. Unified DevSecOps Platforms
Vendors like ArmorCode, Prisma Cloud, and Aqua Security are offering “single-pane” platforms that cover the entire AppSec lifecycle — with automation, visibility, and integration.
5. DevSecOps-as-a-Service (DaaS)
More companies are outsourcing their entire AppSec program to specialized partners that offer 24/7 monitoring, updates, tooling, and advisory — in a flexible monthly model.
Conclusion: Why DevSecOps Consulting is a Must in 2026
The modern software delivery lifecycle is fast, distributed, and constantly exposed. Developers push to production in minutes. New vulnerabilities are discovered daily. Compliance demands are rising globally.
And yet — users expect flawless, secure digital experiences.
That’s why DevSecOps is no longer optional. And it’s also why consulting firms that specialize in DevSecOps are the bridge between agility and safety.
Whether you're a startup building your MVP or an enterprise migrating to cloud-native platforms, the 30 providers listed in this guide offer trusted, high-impact DevSecOps consulting services — ready to plug into your stack, your team, and your goals.
Start with strategy. Choose a consulting partner like Gart Solutions. Secure your pipelines.Because in 2026, DevSecOps isn’t just a tech trend — it’s business-critical.

In recent times, there has been a growing urgency regarding the security concerns of the developed software. Integrating secure development practices into the current processes has become imperative.
This is where DevSecOps comes into play—a powerful methodology that seamlessly integrates security practices into the software development process. In this article, we will explore the world of DevSecOps tools and how they play a pivotal role in enhancing software security, enabling organizations to stay one step ahead of potential threats.
[lwptoc]
Understanding DevSecOps Tools
DevSecOps tools are software applications and utilities designed to integrate security practices into the DevOps (Development and Operations) workflow. These tools aim to automate security checks, improve code quality, and ensure that security measures are an integral part of the software development process.
Some popular DevSecOps tools include:
Continuous Integration (CI) tools for security testing
Continuous Integration (CI) tools play a vital role in automating security testing throughout the development pipeline. They enable developers to regularly test code changes for vulnerabilities and weaknesses, ensuring that security is integrated into every stage of development.
Continuous Deployment (CD) tools for secure deployment
Continuous Deployment (CD) tools facilitate the secure and automated release of software into production environments. By leveraging CD tools, organizations can ensure that security measures are applied consistently during the deployment process.
? Read more: Exploring the Best CI/CD Tools for Streamlined Software Delivery
Security Information and Event Management (SIEM) tools for monitoring and incident response
SIEM tools help organizations monitor and analyze security events across their infrastructure. By providing real-time insights and automated incident response capabilities, SIEM tools empower teams to swiftly detect and respond to potential security breaches.
Here is a list of SIEM (Security Information and Event Management) tools: Splunk, IBM QRadar, ArcSight (now part of Micro Focus), LogRhythm, Sumo Logic, AlienVault (now part of AT&T Cybersecurity), SolarWinds Security Event Manager, Graylog, McAfee Enterprise Security Manager (ESM), Rapid7 InsightIDR.
Static Application Security Testing (SAST) tools for code analysis
SAST tools analyze the source code of applications to identify security flaws, vulnerabilities, and compliance issues. Integrating SAST into the development workflow allows developers to proactively address security concerns during the coding phase.
Some examples of Static Application Security Testing (SAST) tools: Fortify Static Code Analyzer, Checkmarx, Veracode Static Analysis, SonarQube, WhiteSource Bolt, Synopsys Coverity, Kiuwan, WebInspect, AppScan Source, Codacy
Key Features of SAST Solutions:
Code Analysis: SAST solutions perform in-depth code analysis to identify security issues, such as SQL injection, cross-site scripting (XSS), and buffer overflows.
Early Detection: By integrating SAST into the development workflow, security issues can be identified and addressed during the coding phase, reducing the cost and effort required to fix vulnerabilities later in the development cycle.
Continuous Scanning: SAST solutions can be configured for continuous scanning, allowing developers to receive real-time feedback on security issues as code changes are made.
Integration with CI/CD Pipelines: SAST tools seamlessly integrate with Continuous Integration/Continuous Deployment (CI/CD) pipelines, ensuring security testing is an integral part of the software development process.
Compliance Checks: SAST solutions can help organizations adhere to industry-specific and regulatory security standards by identifying code that may violate compliance requirements.
False Positive Reduction: Modern SAST solutions employ advanced algorithms and heuristics to reduce false positives, providing developers with more accurate and actionable results.
Language Support: SAST solutions support a wide range of programming languages, enabling organizations to secure diverse application portfolios.
Remediation Guidance: SAST tools often provide guidance on how to remediate identified vulnerabilities, helping developers address security issues effectively.
Dynamic Application Security Testing (DAST) tools for web application scanning
DAST tools perform dynamic scans of web applications in real-time, simulating attacks to identify potential vulnerabilities. By testing applications from the outside, DAST tools offer a comprehensive view of security risks.
Here is a list of Dynamic Application Security Testing (DAST) tools: OWASP ZAP (Zed Attack Proxy), Burp Suite, Acunetix, Netsparker, WebInspect, Qualys Web Application Scanning (WAS), AppScan Standard, Trustwave App Scanner (formerly Cenzic Hailstorm), Rapid7 AppSpider, Tenable.io Web Application Scanning.
Key Features of DAST Solutions:
Web Application Scanning: DAST tools focus on web applications and assess their security from an external perspective by sending crafted requests and analyzing responses.
Real-World Simulation: DAST solutions mimic actual attack scenarios, including SQL injection, cross-site scripting (XSS), and other common security threats, to identify vulnerabilities.
Comprehensive Coverage: DAST solutions analyze the entire application, including dynamic content generated by the server, to detect security issues across different pages and functionalities.
Automation and Scalability: DAST tools can be automated to perform regular and extensive scans, making them suitable for large-scale web applications and continuous testing.
Out-of-Band Testing: DAST solutions can identify vulnerabilities not discoverable through traditional scanning, such as those found in non-standard HTTP methods or custom headers.
Reduced False Positives: Modern DAST tools employ advanced techniques to minimize false positives, providing developers with accurate and reliable security findings.
Integration with CI/CD Pipelines: DAST solutions can be seamlessly integrated into CI/CD pipelines, allowing security testing to be an integral part of the software development process.
Compliance Support: DAST tools help organizations meet industry standards and regulatory requirements by detecting security weaknesses that may lead to compliance violations.
Continuous Monitoring: Some DAST solutions offer continuous monitoring capabilities, enabling developers to receive real-time feedback on security issues as the application changes.
Interactive Application Security Testing (IAST) tools for real-time code analysis
IAST tools provide real-time security analysis by observing application execution. By combining dynamic and static analysis, IAST tools offer deeper insights into application security while minimizing false positives.
Here is a list of IAST (Interactive Application Security Testing) tools: Contrast Security, Hdiv Security, RIPS Technologies, Seeker by Synopsys, Waratek AppSecurity for Java, Quotium Seeker, ShiftLeft, WhiteHat Security Sentinel IAST, AppSecTest by Pradeo, IriusRisk IAST.
Key Features of IAST Solutions:
Real-Time Analysis: IAST tools continuously monitor applications in real-time as they execute, capturing data on code behavior and interactions with the system to detect security flaws.
Code-Level Visibility: IAST solutions provide detailed information about vulnerabilities, including the exact line of code responsible for the issue, helping developers pinpoint and fix problems with greater accuracy.
Low False Positives: IAST reduces false positives by directly observing application behavior, resulting in more precise identification of true security vulnerabilities.
Minimal Performance Impact: IAST operates with low overhead, ensuring that security testing does not significantly impact the application's performance during runtime.
Comprehensive Security Coverage: By analyzing code execution paths, IAST solutions identify a wide range of vulnerabilities, including those arising from data flow, configuration, and authentication.
Seamless Integration: IAST tools easily integrate into existing development and testing environments, supporting various programming languages and frameworks.
Continuous Security Monitoring: IAST solutions enable continuous monitoring of applications, offering ongoing security assessment throughout the development lifecycle.
DevSecOps Collaboration: IAST fosters collaboration between development, security, and operations teams by providing real-time insights accessible to all stakeholders.
Remediation Guidance: IAST solutions not only identify vulnerabilities but also offer actionable remediation guidance, streamlining the process of fixing security issues.
Compliance Support: IAST assists organizations in meeting regulatory requirements by providing accurate and detailed security assessments.
Runtime Application Self-Protection (RASP) tools for runtime security
RASP tools operate within the application runtime environment, actively monitoring for malicious behavior and automatically blocking potential threats. These tools provide an additional layer of protection to complement other security measures.
Here is a list of RASP (Runtime Application Self-Protection) tools: Sqreen, Contrast Security, Waratek AppSecurity for Java, StackRox, Veeam PN (Powered Network), Guardicore, Aqua Security, Datadog Security Monitoring, Wallarm, Arxan Application Protection.
Key Features of RASP Solutions:
Real-Time Protection: RASP tools actively monitor application behavior during runtime, detecting and blocking security threats as they occur in real-time.
Immediate Response: By residing within the application, RASP can take immediate action against threats without relying on external systems, ensuring faster response times.
Application-Centric Approach: RASP solutions focus on protecting the application itself, making them independent of external security configurations.
Automatic Policy Enforcement: RASP automatically enforces security policies based on the application's behavior, mitigating vulnerabilities and enforcing compliance.
Precise Attack Detection: RASP can identify and differentiate between legitimate application behavior and malicious activities, reducing false positives.
Low Performance Overhead: RASP operates with minimal impact on application performance, ensuring efficient security without compromising user experience.
Runtime Visibility: RASP solutions provide real-time insights into application security events, helping developers and security teams understand attack patterns and trends.
Adaptive Defense: RASP can dynamically adjust its protection strategies based on the evolving threat landscape, adapting to new attack vectors and tactics.
Application-Aware Security: RASP understands the unique context of the application, allowing it to tailor security responses to specific application vulnerabilities.
Continuous Protection: RASP continuously monitors the application, offering ongoing security coverage that extends throughout the application's lifecycle.
DevSecOps Integration: RASP seamlessly integrates into DevSecOps workflows, empowering developers with real-time security feedback and enabling collaboration between teams.
Compliance Support: RASP helps organizations meet regulatory requirements by providing active protection against security threats and potential data breaches.
DevSecOps Tools Table
CategoryDevSecOps ToolCI/CDJenkins, GitLab CI, Travis CI, CircleCISASTSonarQube, Veracode, Checkmarx, FortifyDASTOWASP Zap, Burp Suite, Acunetix, NetsparkerIASTContrast Security, RASPberryRASPSqreen, AppTrana, GuardicoreSIEMSplunk, IBM QRadar, ArcSight, LogRhythmContainer SecurityAqua Security, Sysdig, TwistlockSecurity OrchestrationDemisto, Phantom, ResilientAPI SecurityPostman, Swagger InspectorChaos EngineeringGremlin, Chaos Monkey, PumbaPolicy-as-a-CodeOpen Policy Agent (OPA), Rego, KyvernoThis table provides a selection of DevSecOps tools across different categories.
Empower your team with DevOps excellence! Streamline workflows, boost productivity, and fortify security. Let's shape the future of your software development together – inquire about our DevOps Consulting Services.
In recent years, DevOps has become more popular as many companies adopt its practices. The growth is also influenced by advancements in cloud computing, Artificial Intelligence, and Machine Learning. These, along with a heightened focus on security and automation, have significantly impacted the evolving mindset.
[lwptoc]
Initially, DevOps aimed to unify operations with agile and automation methods used by development teams. This led to more efficient and continuous software releases.
How has DevOps changed? It's gaining acceptance across various industries, with professionals recognizing its value at organizational and cultural levels.
This acceptance is due to the adoption of different DevOps trends and tools:
Cloud Computing simplifies DevOps strategy, improving software development through scalability and automation.
Kubernetes enhances app portability and flexibility.
Artificial Intelligence and Machine Learning prioritize automation and optimization in DevOps practices.
DevSecOps integrates security into every development step, promoting a shift-left approach.
With technology's help, DevOps has become a robust methodology, beneficial when correctly applied to any organization.
Embracing AI in DevOps
Artificial Intelligence (AI) is set to revolutionize the DevOps landscape. From infusing AI into configuration management to leveraging it for in-depth analysis and cost optimization, the role of AI in streamlining DevOps processes is undeniable.
Challenge: Adapting to AI-driven methodologies requires upskilling and a mindset shift. Teams need to embrace automation without losing the human touch.
AIOps doesn't just cut costs; it boosts revenue, improves customer satisfaction, safeguards brand reputation, and directly and indirectly influences business performance and the bottom line.
AIOps Potential in IT Operations
AIOps frameworks offer predefined metrics, procedures, policies, and process templates.
AIOps collects data from all network systems, monitoring business process execution.
AIOps maintains a live overview of a company's entire infrastructure, including physical servers, workstations, multi-cloud environments, data repositories, applications, and services.
AIOps frameworks ensure strict adherence to Service Level Agreements (SLAs) for both internal and external users.
AIOps frameworks enhance IT operations, ensuring high service availability.
As AIOps adoption isn't universal, organizations implementing these systems gain a competitive advantage. Users appreciate the rapid response of applications and services, a natural outcome of AIOps implementation.
MLOps Evolution
MLOps, the intersection of machine learning and operations, is evolving rapidly. The emergence of the MLOps Engineer role signals a new era in managing machine learning models seamlessly. Integrating development, testing, and deployment in the realm of machine learning becomes a focal point.
Challenge: Harmonizing traditional DevOps practices with MLOps requires synchronization and alignment of processes.
Serverless Computing on the Rise
Say hello to the serverless revolution! The popularity of serverless architecture is soaring as it becomes a catalyst for faster development and simplified infrastructure. Expect a paradigm shift in application building and deployment strategies.
Challenge: Navigating the nuances of serverless architecture demands a shift in mindset and a reevaluation of application design.
Roles and Responsibilities Redefined
The DevOps team structure is getting a makeover. Roles are becoming more distinct, with a clear definition of responsibilities. Specialized approaches like Site Reliability Engineering (SRE) are gaining traction, ensuring a more efficient and specialized workforce.
Challenge: Adapting to specialized roles requires a balance between expertise and cross-functional collaboration.
FinOps Takes Center Stage
Financial Operations (FinOps) is emerging as a key player in DevOps. Automated tools for optimizing costs on cloud resources are becoming indispensable. FinOps teams play an increasingly vital role in ensuring efficient cost management.
Challenge: Integrating FinOps seamlessly into DevOps workflows requires a strategic and collaborative approach.
2026 promises to be a year of innovation and transformation in the DevOps sphere. Embracing these trends while tackling associated challenges will be the key to staying ahead in the ever-evolving tech landscape. Are you ready for the DevOps revolution?
Reducing Footprint
A new trend takes the spotlight - the quest to reduce the environmental footprint. DevOps is increasingly focusing on eco-friendly practices, emphasizing efficiency in resource usage and minimizing waste.
Challenge: Balancing rapid development with sustainable practices requires a holistic approach and a commitment to eco-conscious decision-making.
Evolving Towards NoOps
A noteworthy trend emerging in DevOps is the transition towards NoOps. NoOps, short for "No Operations," envisions a state where operations are automated to an extent that manual intervention becomes minimal. The goal is to streamline processes to the extent that routine operational tasks are handled seamlessly, without requiring dedicated personnel involvement.
noOps vs. devops.
Challenge: Embracing the NoOps philosophy presents the challenge of striking a balance between automation and human oversight. Organizations must navigate this transition carefully, ensuring that while operations become more efficient, they don't lose sight of essential human insights and decision-making capabilities. Achieving a harmonious blend of automation and human expertise is crucial for the successful implementation of the NoOps trend in DevOps practices.
DevSecOps
It's important to note that DevSecOps is not a specific role or person, but rather a set of practices that focus on securing services within the cloud. Considering the complexity of integrating multiple services, it's crucial to have security measures in place to protect sensitive data as it flows between them. These measures can include data encryption, role-based access control, and change management, just to name a few.
Balancing Simplicity and Efficiency
A prominent movement within the DevOps community is focused on discovering the perfect equilibrium between simplicity and efficacy. In the past, launching an application was an extensive process involving intricate infrastructure preparation, elaborate tool configuration, meticulous design documentation, and the setup of tool environments across multiple teams.
However, thanks to recent advancements, this process has become much more streamlined. With developers now able to simply create a repository and add their application code, while DevOps engineers add infrastructure as code to the same repository, the deployment process has significantly sped up. In fact, with the help of cloud platforms, the very next day, a fully functional application can be up and running.
This approach allows for rapid start-ups by only requiring minimal actions to create an MVP or POC. While certain components, such as security, versioning, and thorough testing, may not be fully implemented initially, technological strategies enable the deployment of a functional application and basic infrastructure within a half day.
This can greatly lower the barrier to entry for development. The integration between development and infrastructure has greatly improved. Developers can easily incorporate pre-made libraries into their code, automating the creation of necessary infrastructure on platforms like AWS or Azure during the building process. This has greatly reduced the gap between development and infrastructure administration, resulting in a faster initial step, given a solid understanding of the process involved.
Conclusion
2026 promises to be a year of innovation and transformation in the DevOps sphere. Embracing these trends while tackling associated challenges will be the key to staying ahead in the ever-evolving tech landscape. Are you ready for the DevOps revolution?