SOC (Service Organization Control) audits are a way to show that your internal processes are up to standard—whether it’s managing financial data or protecting sensitive information like customer privacy.
SOC 2 compliance is a set of guidelines that helps companies manage and protect customer data. It’s especially important for businesses that offer services to other companies, like those in IT and cloud services.
If your business handles sensitive information, SOC 2 compliance audit is crucial. Preparing for a SOC 2 audit means following clear steps to make sure your data protection measures are working effectively.
In today’s digital age, being SOC 2 compliant shows your customers that you prioritize data security, building trust and confidence in your business.
What is SOC 2?
SOC 2 (System and Organization Controls 2) is a set of compliance standards developed by the American Institute of Certified Public Accountants (AICPA). It is aimed at service organizations that store customer data in the cloud.The audit assesses a company’s systems and processes based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
Unlike other frameworks that are rigid, SOC 2 is flexible and allows companies to select which trust service criteria they need to focus on, depending on their operational needs.
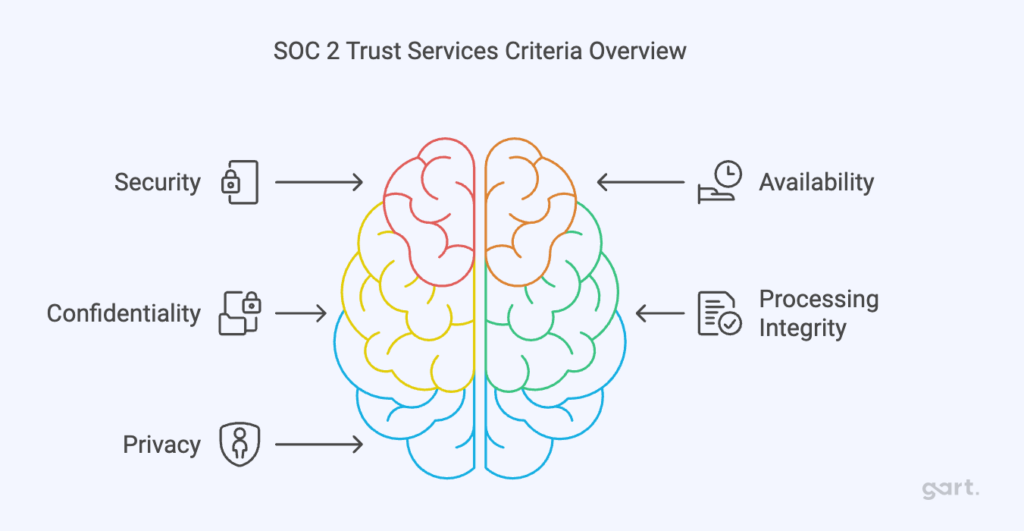
Trust Services Criteria
SOC 2 focuses on five key trust services criteria:
- Security: Ensuring that systems are protected against unauthorized access (both physical and digital).
- Availability: Making sure systems are available for operation and use as expected.
- Confidentiality: Protecting sensitive information from unauthorized access.
- Processing Integrity: Ensuring that data processing systems operate correctly, delivering accurate results.
- Privacy: Protecting personal information collected and ensuring it is used appropriately.
Out of these five criteria, security is the only mandatory one. However, most organizations also focus on availability and confidentiality, as they are critical for maintaining customer trust.
Pre-Audit Preparations
Defining the Audit Scope
The first step in preparing for a SOC 2 audit is clearly defining the scope. This scope outlines the specific systems and processes that will be evaluated. It is essential to ensure that the defined information system – infrastructure, software, people, data, and processes – still meets the current business needs. If there have been changes, adjustments to the scope may be necessary.
Control Customization
SOC 2 allows organizations to customize controls based on their operational environment. For example, if your organization has shifted from a waterfall to an agile development process, the controls should reflect this change. Ensuring that controls align with how the business operates helps auditors understand your environment better, leading to a smoother audit process.
Team Readiness
Preparing the internal team for the audit is crucial. Assigning clear roles, setting agendas, and conducting control spot-checks beforehand can save time and ensure that everyone knows what is expected during the audit. Key personnel must understand their roles in explaining controls, providing evidence, and participating in system walkthroughs.
Ask how Gart Solutions can help you with SOC 2 compliance. Contact us today.
SOC 2 Audit Process
The SOC 2 audit is not a one-size-fits-all. Organizations can choose which of the trust service criteria they want to be audited on. This flexibility allows businesses to tailor their audit based on specific operational needs. For example, an e-commerce platform might focus on security and availability, while a healthcare provider might prioritize security and confidentiality.
The audit process itself involves several steps:
- Documentation: It is essential to document all processes and policies. Auditors will review this documentation to verify that security measures are in place and that they are being followed. For example, if a company states that it conducts annual access reviews for AWS, it must provide evidence that these reviews actually took place.
- Audit Execution: Auditors will examine the company’s controls to ensure compliance. This can involve reviewing data logs, verifying access permissions, and conducting interviews with key personnel.
- Audit Types:
- Type 1 Audit: A snapshot of the organization’s compliance at a specific point in time.
- Type 2 Audit: Reviews the operational effectiveness of controls over a period, typically 12 months.
*The key difference between Type I and Type II audits is time. A Type I audit checks if the controls you have in place are working at a single point in time. A Type II audit goes further by testing whether those controls actually worked over a longer period, usually at least six months. Both SOC 1 and SOC 2 audits can come in either Type I or Type II formats, which is why it can get confusing.
Critical Controls for SOC 2 Compliance
SOC 2 compliance requires several key controls across the organization. Some of the most important include:
- Access Controls: Implementing principles like “least privilege,” where only necessary personnel have access to sensitive data. Multi-factor authentication is also required for accessing sensitive systems like cloud services.
- Encryption: Both encryption at rest (data stored) and encryption in transit (data moving between systems) are crucial. Encryption protects sensitive information from unauthorized access.
- Change Management: In software companies, it’s important to maintain strict version control and require independent approval of changes. This ensures that code changes are securely managed and that no unauthorized changes affect the system.
Post-Audit Steps
Reviewing the System Description
After the audit fieldwork is completed, the next step is reviewing the system description. This section of the SOC 2 report details the organization’s systems and processes. It must be reviewed annually to ensure that it reflects any changes in the company’s operations. The system description can be lengthy, often around 30 pages, so early preparation is necessary.
Maintaining Compliance for Future Audits
Once the initial audit is done, it is important to establish an ongoing compliance program. This includes regular control checks, ensuring that controls continue to operate as expected. For example, if a control requires quarterly user access reviews, these must be conducted regularly. Assigning responsibility for each control ensures accountability and reduces the risk of future non-compliance.
Audit Closure and Next Steps
Once the audit is complete, it is essential to schedule a closeout meeting with the auditor to discuss improvements and plan for future audits. This meeting should also cover how to use the SOC 2 report for business purposes, such as sharing it with stakeholders or using it as a marketing tool to demonstrate compliance. Additionally, preparing for the next year’s audit by scheduling key dates and responsibilities is recommended.
SOC 2 Audit Checklist
Human Factors in SOC 2 Compliance
While SOC 2 compliance focuses heavily on technical controls, human factors also play a critical role. Processes like employee onboarding and offboarding must be managed consistently to ensure that no unauthorized individuals gain access to systems. For instance, an overlooked background check due to an HR error could compromise compliance.
Automation tools, such as Secureframe, are invaluable in mitigating risks associated with human error. By automating reminders for critical processes (like access reviews or background checks), companies can reduce the chance of non-compliance due to manual oversights.
SOC 1 vs. SOC 2
SOC 1 audits, also known as SSAE16 audits, look at how well your company controls financial reporting. SOC 2 audits focus on other important aspects like security, system availability, data processing accuracy, confidentiality, and privacy. Think of it like comparing apples to oranges—they’re both fruit but serve different needs.
Key differences between SOC 2 and ISO 27001
Table
| Aspect | SOC 2 | ISO 27001 |
|---|---|---|
| Definition | Set of audit reports based on Trust Service Criteria (TSC) | Standard for an Information Security Management System (ISMS) |
| Geographical Applicability | Primarily used in the United States | Internationally recognized |
| Industry Applicability | Service organizations across various industries | Organizations of any size or industry |
| Compliance | Attested by a Certified Public Accountant (CPA) | Certified by an accredited ISO certification body |
| Focus | Proves security level of systems against static principles and criteria | Defines, implements, operates, controls, and improves overall security |
| Report Types | Type 1 and Type 2 reports | Certification audit and surveillance audits |
| Purpose | Validates internal controls related to information systems | Establishes and maintains an ISMS |
Conclusion
SOC 2 compliance is essential for organizations that handle sensitive data, particularly in the B2B sector. Achieving SOC 2 certification not only demonstrates that a company takes security seriously but also enables it to expand its business by selling to larger, security-conscious clients. SOC 2 is more than just a compliance program; it is a powerful tool for fostering customer trust and enhancing business opportunities.
How can Gart Solutions help with SOC 2 compliance?
Gart Solutions offers:
- Gap assessments and remediation
- Secure cloud infrastructure setup
- Automated evidence collection
- Policy documentation support
- Post-audit compliance maintenance
Our team helps you streamline the entire SOC 2 journey and stay ready for future audits.
See how we can help to overcome your challenges









