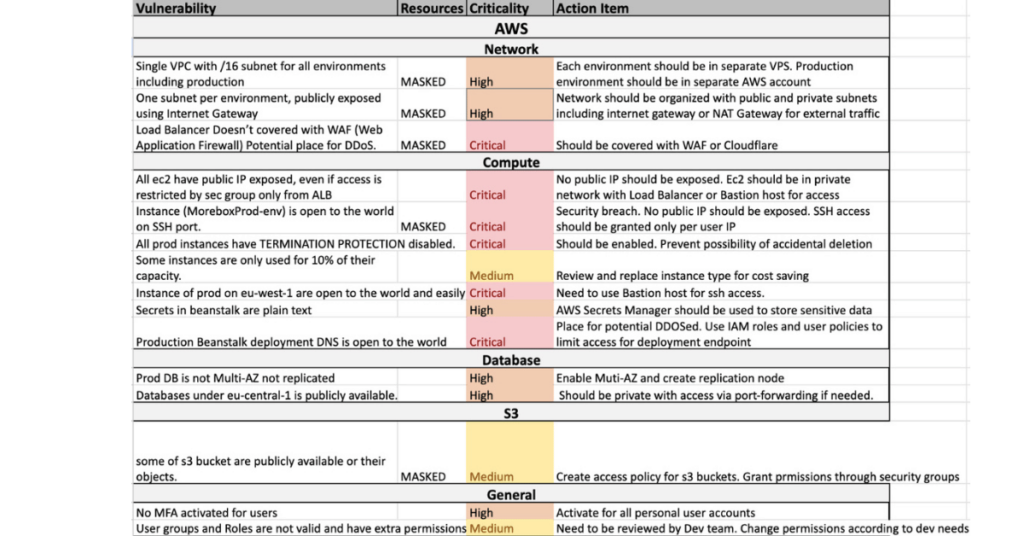
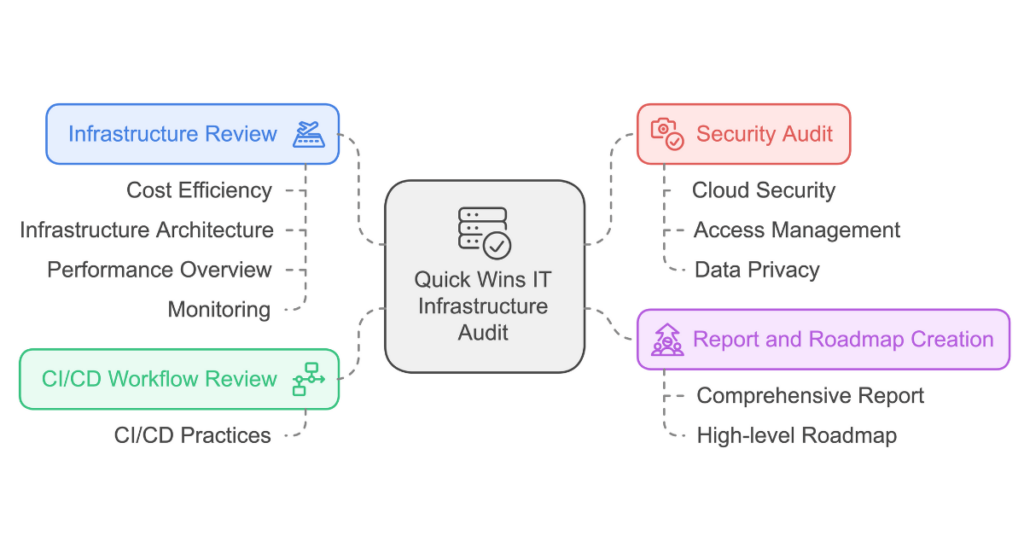
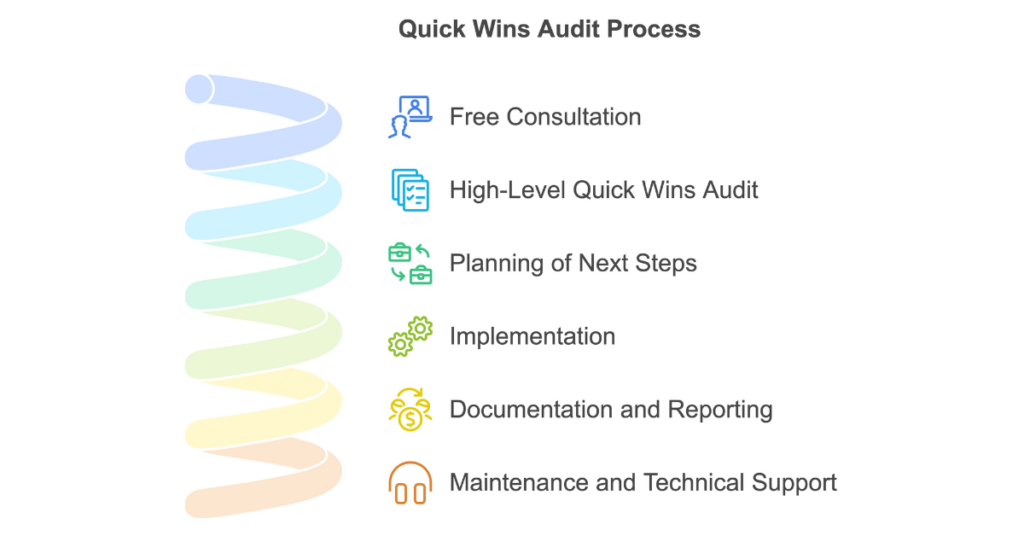
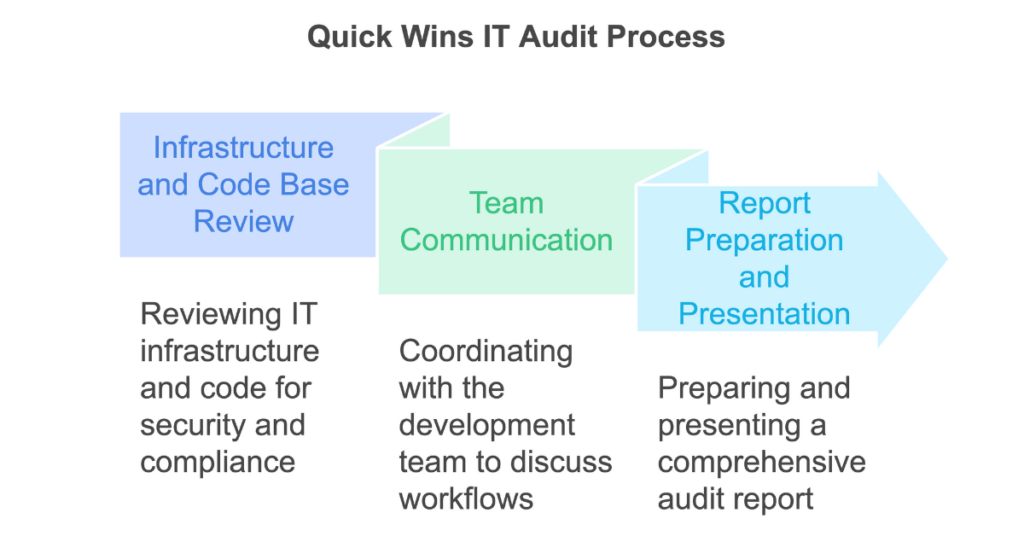
SOC (Service Organization Control) audits are a way to show that your internal processes are up to standard—whether it's managing financial data or protecting sensitive information like customer privacy.
SOC 2 compliance is a set of guidelines that helps companies manage and protect customer data. It's especially important for businesses that offer services to other companies, like those in IT and cloud services.
If your business handles sensitive information, SOC 2 compliance audit is crucial. Preparing for a SOC 2 audit means following clear steps to make sure your data protection measures are working effectively.
In today’s digital age, being SOC 2 compliant shows your customers that you prioritize data security, building trust and confidence in your business.
What is SOC 2?
SOC 2 (System and Organization Controls 2) is a set of compliance standards developed by the American Institute of Certified Public Accountants (AICPA). It is aimed at service organizations that store customer data in the cloud.The audit assesses a company’s systems and processes based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
Unlike other frameworks that are rigid, SOC 2 is flexible and allows companies to select which trust service criteria they need to focus on, depending on their operational needs.
Trust Services Criteria
SOC 2 focuses on five key trust services criteria:
Security: Ensuring that systems are protected against unauthorized access (both physical and digital).
Availability: Making sure systems are available for operation and use as expected.
Confidentiality: Protecting sensitive information from unauthorized access.
Processing Integrity: Ensuring that data processing systems operate correctly, delivering accurate results.
Privacy: Protecting personal information collected and ensuring it is used appropriately.
Out of these five criteria, security is the only mandatory one. However, most organizations also focus on availability and confidentiality, as they are critical for maintaining customer trust.
Pre-Audit Preparations
Defining the Audit Scope
The first step in preparing for a SOC 2 audit is clearly defining the scope. This scope outlines the specific systems and processes that will be evaluated. It is essential to ensure that the defined information system – infrastructure, software, people, data, and processes – still meets the current business needs. If there have been changes, adjustments to the scope may be necessary.
Control Customization
SOC 2 allows organizations to customize controls based on their operational environment. For example, if your organization has shifted from a waterfall to an agile development process, the controls should reflect this change. Ensuring that controls align with how the business operates helps auditors understand your environment better, leading to a smoother audit process.
Team Readiness
Preparing the internal team for the audit is crucial. Assigning clear roles, setting agendas, and conducting control spot-checks beforehand can save time and ensure that everyone knows what is expected during the audit. Key personnel must understand their roles in explaining controls, providing evidence, and participating in system walkthroughs.
Ask how Gart Solutions can help you with SOC 2 compliance.
Contact us today.
SOC 2 Audit Process
The SOC 2 audit is not a one-size-fits-all. Organizations can choose which of the trust service criteria they want to be audited on. This flexibility allows businesses to tailor their audit based on specific operational needs. For example, an e-commerce platform might focus on security and availability, while a healthcare provider might prioritize security and confidentiality.
The audit process itself involves several steps:
Documentation: It is essential to document all processes and policies. Auditors will review this documentation to verify that security measures are in place and that they are being followed. For example, if a company states that it conducts annual access reviews for AWS, it must provide evidence that these reviews actually took place.
Audit Execution: Auditors will examine the company’s controls to ensure compliance. This can involve reviewing data logs, verifying access permissions, and conducting interviews with key personnel.
Audit Types:
Type 1 Audit: A snapshot of the organization’s compliance at a specific point in time.
Type 2 Audit: Reviews the operational effectiveness of controls over a period, typically 12 months.
*The key difference between Type I and Type II audits is time. A Type I audit checks if the controls you have in place are working at a single point in time. A Type II audit goes further by testing whether those controls actually worked over a longer period, usually at least six months. Both SOC 1 and SOC 2 audits can come in either Type I or Type II formats, which is why it can get confusing.
Critical Controls for SOC 2 Compliance
SOC 2 compliance requires several key controls across the organization. Some of the most important include:
Access Controls: Implementing principles like "least privilege," where only necessary personnel have access to sensitive data. Multi-factor authentication is also required for accessing sensitive systems like cloud services.
Encryption: Both encryption at rest (data stored) and encryption in transit (data moving between systems) are crucial. Encryption protects sensitive information from unauthorized access.
Change Management: In software companies, it’s important to maintain strict version control and require independent approval of changes. This ensures that code changes are securely managed and that no unauthorized changes affect the system.
Post-Audit Steps
Reviewing the System DescriptionAfter the audit fieldwork is completed, the next step is reviewing the system description. This section of the SOC 2 report details the organization’s systems and processes. It must be reviewed annually to ensure that it reflects any changes in the company’s operations. The system description can be lengthy, often around 30 pages, so early preparation is necessary.
Maintaining Compliance for Future AuditsOnce the initial audit is done, it is important to establish an ongoing compliance program. This includes regular control checks, ensuring that controls continue to operate as expected. For example, if a control requires quarterly user access reviews, these must be conducted regularly. Assigning responsibility for each control ensures accountability and reduces the risk of future non-compliance.
Audit Closure and Next StepsOnce the audit is complete, it is essential to schedule a closeout meeting with the auditor to discuss improvements and plan for future audits. This meeting should also cover how to use the SOC 2 report for business purposes, such as sharing it with stakeholders or using it as a marketing tool to demonstrate compliance. Additionally, preparing for the next year’s audit by scheduling key dates and responsibilities is recommended.
SOC 2 Audit Checklist
SOC-2-Audit-ChecklistDownload
Human Factors in SOC 2 Compliance
While SOC 2 compliance focuses heavily on technical controls, human factors also play a critical role. Processes like employee onboarding and offboarding must be managed consistently to ensure that no unauthorized individuals gain access to systems. For instance, an overlooked background check due to an HR error could compromise compliance.
Automation tools, such as Secureframe, are invaluable in mitigating risks associated with human error. By automating reminders for critical processes (like access reviews or background checks), companies can reduce the chance of non-compliance due to manual oversights.
SOC 1 vs. SOC 2
SOC 1 audits, also known as SSAE16 audits, look at how well your company controls financial reporting. SOC 2 audits focus on other important aspects like security, system availability, data processing accuracy, confidentiality, and privacy. Think of it like comparing apples to oranges—they’re both fruit but serve different needs.
Key differences between SOC 2 and ISO 27001
Table
AspectSOC 2ISO 27001DefinitionSet of audit reports based on Trust Service Criteria (TSC)Standard for an Information Security Management System (ISMS)Geographical ApplicabilityPrimarily used in the United StatesInternationally recognizedIndustry ApplicabilityService organizations across various industriesOrganizations of any size or industryComplianceAttested by a Certified Public Accountant (CPA)Certified by an accredited ISO certification bodyFocusProves security level of systems against static principles and criteriaDefines, implements, operates, controls, and improves overall securityReport TypesType 1 and Type 2 reportsCertification audit and surveillance auditsPurposeValidates internal controls related to information systemsEstablishes and maintains an ISMS
Conclusion
SOC 2 compliance is essential for organizations that handle sensitive data, particularly in the B2B sector. Achieving SOC 2 certification not only demonstrates that a company takes security seriously but also enables it to expand its business by selling to larger, security-conscious clients. SOC 2 is more than just a compliance program; it is a powerful tool for fostering customer trust and enhancing business opportunities.
How can Gart Solutions help with SOC 2 compliance?
Gart Solutions offers:
Gap assessments and remediation
Secure cloud infrastructure setup
Automated evidence collection
Policy documentation support
Post-audit compliance maintenanceOur team helps you streamline the entire SOC 2 journey and stay ready for future audits.

Imagine this: You’re busy running your clinic, pharmacy, or health tech firm when suddenly an email arrives – you’re getting audited for HIPAA compliance. Panic sets in. What if your policies aren’t updated? What if employee training is outdated? What if a single misstep costs you millions in fines?
This isn’t an imaginary worst-case scenario. HIPAA audits are real, random, and rigorous. With penalties ranging from $50,000 per incident to $1.5 million per year, failing an audit can financially and reputationally cripple your business.
But here’s the good news: You can prepare in advance. This guide will break down everything you need to know in simple, practical steps to ensure you’re not just compliant on paper but audit-ready anytime.
We’ll cover:
What HIPAA really is (without jargon)
Who needs to comply (it’s not just hospitals)
What gets audited
The three main HIPAA rules
Step-by-step HIPAA audit preparation checklist
How to avoid common pitfalls
How experts like Gart Solutions can help you stay secure and compliant
Ready to protect your business and your patients’ trust? Let’s dive in.
What is PHI (Protected Health Information)?
HIPAA's main goal is to keep patients' medical records and personal health details safe from being shared without permission. It sets nationwide rules to make sure that health information stays private, accurate, and accessible only to the right people. These rules apply to health plans, doctors, hospitals, and any businesses that handle patient information.
Protected Health Information (PHI) is any health-related data that can be traced back to a specific person. This includes things like medical records, names, social security numbers, and even fingerprints or other biometric data. HIPAA requires that all health information connected to personal details is considered PHI and must be kept secure.
The U.S. Department of Health and Human Services (HHS) has defined 18 unique identifiers that classify health information as PHI, including but not limited to:
Names
Dates (except years)
Social security numbers
Medical record numbers
Email addresses
Device identifiers
Biometric data (fingerprints, face scans)
Who Must Comply with HIPAA?
HIPAA compliance is mandatory for entities that handle PHI, including:
Healthcare providers: Hospitals, clinics, nursing homes, pharmacies.
Health plans: Health insurance companies, Medicare, Medicaid.
Health clearinghouses: Organizations that process health data like billing services and data management firms.
Business associates: Third-party vendors, including billing companies, consultants, and cloud service providers, who handle PHI on behalf of covered entities.
HIPAA compliance extends beyond healthcare providers to include business associates—third-party entities that perform services involving the use or disclosure of Protected Health Information (PHI) on behalf of covered entities like hospitals or clinics. Examples of business associates include:
Billing companies
Cloud service providers
Consultants
Transcription services
Data storage firms
Business associates are required to ensure the same level of protection for PHI as the primary covered entities, such as hospitals and insurance companies. This means they must adhere to HIPAA’s Privacy, Security, and Breach Notification rules. If a breach occurs or there’s non-compliance, business associates face the same penalties, ranging from $50,000 fines per incident to $1.5 million annually.
Key takeaway:If you store, process, access, or transmit PHI in any capacity, HIPAA applies to you. No exceptions.
The Three Main Rules of HIPAA
HIPAA compliance is governed by three primary rules:
Privacy Rule
This rule controls how personal health information (PHI) can be used and shared. It focuses on keeping patient information safe from unauthorized access while still allowing healthcare providers to share it when needed for treatment or running their services. It limits who can see a patient’s health information and under what conditions it can be shared, giving patients control over their personal health details.
Security Rule
This rule is about protecting electronic health information (ePHI). It requires security measures like encryption, access controls, and monitoring logs to keep data safe from breaches. Whether the data is being stored or sent, this rule ensures it is protected. It also requires healthcare organizations to have administrative, physical, and technical safeguards in place to keep electronic health data secure.
Breach Notification Rule
If there’s a breach involving unsecured health information, this rule requires healthcare providers to notify the affected individuals and, in some cases, the government and media. The individuals must be informed within 60 days if their health information was accessed without permission. If the breach is large, the Department of Health and Human Services (HHS) and the media may also need to be notified.
Penalties for Non-Compliance
Failing to comply with HIPAA can lead to severe consequences. Financial penalties range from $50,000 per incident to $1.5 million per violation category per year. Persistent violations or multiple breaches can result in multi-million-dollar fines, and in some cases, criminal charges.
Even if an organization is found to be compliant today, they may face fines for any previous deficiencies. These penalties can be financially debilitating, highlighting the importance of maintaining a thorough and consistent compliance plan.
What Is a HIPAA Audit?
A HIPAA audit is a formal assessment conducted by the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) to verify that healthcare providers, health plans, and their business associates comply with HIPAA’s privacy and security requirements.
Why do HIPAA audits happen?
Random selection for proactive audits
Complaints filed by patients or staff
Data breach incidents reported to OCR
These audits are not just paperwork reviews. They evaluate your actual practices, training programs, and technical safeguards. In recent years, OCR contracted firms like FCI Federal to conduct these audits, expanding audit frequency and depth.
Types of HIPAA audits:
Desk audits – You submit requested documentation electronically within a strict timeframe (usually 10-14 days).
On-site audits – Auditors visit your physical office to observe operations, interview staff, and inspect security practices.
If deficiencies are found, you may be required to submit a Corrective Action Plan (CAP) and could face monetary penalties depending on severity.
Key takeaway:A HIPAA audit tests your real-world compliance, not just your written policies.
What Gets Audited During a HIPAA Audit?
Auditors review both current and historical compliance efforts, meaning that even if you updated policies last week, outdated practices from last year can still lead to penalties.
Areas commonly audited:
Privacy policies and procedures: Are they up to date and aligned with HIPAA standards?
Security risk assessment reports: Have you identified and addressed vulnerabilities in your systems?
Employee training records: Has your staff been trained regularly on HIPAA requirements?
Business Associate Agreements (BAAs): Are they signed, current, and compliant with HIPAA rules?
Breach notification procedures: Do you have a documented and tested plan in place?
Technical safeguards: Encryption, access controls, audit logs, and authentication systems.
Physical safeguards: Locked storage, secure facility access, workstation security policies.
Incident response plans: Are you prepared to handle and report breaches effectively?
What is the auditor looking for?
They want proof that:
You understand HIPAA requirements
You have implemented policies, procedures, and safeguards
Your team is trained and compliant
You maintain documentation to demonstrate compliance
Failure to provide these quickly can trigger deeper investigations or fines.
Implementation and Best Practices
HIPAA compliance requires organizations to adopt several best practices, including:
Employee Training: All employees handling PHI must be thoroughly trained on HIPAA policies and procedures.
Risk Management: Organizations should regularly assess risks to PHI and take necessary steps to mitigate them.
Access Control: Only authorized personnel should have access to PHI, ensuring that medical information is protected from unauthorized access.
HIPAA compliance checklist
HIPAA-Compliance-ChecklistDownload
Common Mistakes to Avoid During HIPAA Audits
Even organizations with good intentions fail audits due to avoidable errors. Here are critical mistakes to avoid:
Incomplete risk assessments – Simply checking boxes without thorough evaluation.
Outdated policies – Using templates created years ago without updates.
No employee training records – Failing to document who attended HIPAA training and when.
Unencrypted data – Storing PHI in cloud or local systems without proper encryption.
Weak password policies – Allowing default passwords or sharing logins.
Missing BAAs – Working with vendors handling PHI without signed Business Associate Agreements.
Ignoring small breaches – Failing to document or notify minor unauthorized disclosures.
No audit logs – Lack of monitoring for who accesses PHI and when.
Avoid these pitfalls by conducting internal audits regularly, keeping policies current, and working with compliance experts who can identify gaps before OCR finds them.
How Gart Solutions Can Help with HIPAA Audits
Preparing for a HIPAA audit isn’t just about checking off compliance boxes – it’s about implementing security and privacy best practices that protect your patients and your business long-term. This is where Gart Solutions comes in.
Here’s how Gart Solutions can support your HIPAA compliance:
Cloud Infrastructure DesignDesign and deploy cloud environments compliant with HIPAA standards, ensuring scalable and secure PHI storage.Cloud Infrastructure DesignDesign and deploy cloud environments compliant with HIPAA standards, ensuring scalable and secure PHI storage.
Data Encryption ImplementationEncrypt sensitive data in transit and at rest to prevent unauthorized access.
Automated Compliance MonitoringUse DevOps practices to continuously scan for misconfigurations and vulnerabilities, resolving them in real time.
Audit Trail CreationDeploy logging and monitoring tools to track system activity and demonstrate compliance during audits.
Incident Response AutomationDevelop automated procedures to minimize breach impact and ensure fast compliance with HIPAA breach notification rules.
Risk Assessment and ManagementConduct thorough risk assessments, implement remediation plans, and monitor for ongoing compliance.
Backup and Disaster RecoverySet up secure backup systems and disaster recovery plans to ensure data is always recoverable.
Business Associate Agreements (BAA) ManagementHelp draft and maintain compliant BAAs with cloud vendors and business associates.
By partnering with Gart Solutions, you not only prepare for HIPAA audits but also build a resilient and secure IT environment that earns your patients’ trust and protects your business.
Gart Solutions can design and implement cloud infrastructure that adheres to HIPAA security and privacy standards. This includes ensuring that the architecture is secure, scalable, and meets the technical safeguards required for protected health information (PHI) handling.
One of the core requirements for HIPAA compliance is ensuring that sensitive data, such as PHI, is encrypted both in transit and at rest. Gart Solutions can implement encryption protocols on cloud services, ensuring that all data is protected from unauthorized access.
Using DevOps practices, Gart Solutions can automate the monitoring of cloud environments for HIPAA compliance. By setting up automated scans and alert systems, they can ensure that any misconfigurations or potential breaches are identified and resolved in real-time.
HIPAA requires that organizations maintain a record of access and activity for all systems handling PHI. Gart Solutions can deploy logging and monitoring tools to ensure a robust audit trail. This makes it easier to demonstrate compliance during an audit.
In case of a security incident, a fast and effective response is critical. Gart Solutions can automate incident response procedures, minimizing response time and ensuring that any HIPAA violations are addressed immediately.
Gart Solutions can conduct regular risk assessments, helping organizations identify vulnerabilities in their cloud infrastructure. They can then implement remediation plans and continuously monitor the environment to reduce the risk of non-compliance.
HIPAA requires that organizations have plans for backup and disaster recovery in place. Gart Solutions can set up automated, secure backups and disaster recovery solutions, ensuring that data is always recoverable and protected from loss.
For any cloud services provided to healthcare organizations, a BAA is required to establish responsibilities for HIPAA compliance. Gart Solutions can help navigate the process of drafting and maintaining BAAs with cloud vendors, ensuring proper legal protection and compliance.
These services ensure that organizations meet HIPAA requirements while maintaining efficient, secure cloud operations.
Conclusion
HIPAA serves as a cornerstone of healthcare privacy and security regulations, ensuring that individuals' health data is protected. Healthcare providers, insurance companies, and associated businesses must understand and adhere to HIPAA's rules to avoid heavy penalties and safeguard patient trust.

How can AI tools enhance DevOps efficiency?AI tools like ChatGPT, Claude, GitHub Copilot, and VZero are transforming DevOps by automating coding, streamlining infrastructure management, and accelerating UI prototyping. These tools reduce development time, minimize human error, and free up engineers for strategic tasks.
We’re long past the debate about whether AI will take over jobs. In DevOps, AI is already reshaping how we work—automating routine tasks, assisting in decision-making, and enhancing speed and productivity.
Just two years ago, using AI for code generation was off-limits in many companies. Today, it’s not only permitted — it’s encouraged. The shift has been fast and profound.
In this guide, I’ll share real-world use cases of how I use AI tools as a DevOps engineer and cloud architect, showing you where they fit into daily workflows and how they boost performance.
The Rise of AI Assistants in DevOps
Let's dive into something that’s been on everyone’s radar lately: AI assistants. But don’t worry, we’re not going to talk about AI taking over our jobs or debating its future in society. Instead, let’s get practical and look at how we’re already using AI assistants in our daily work routines.
Just two years ago, when ChatGPT 3.5 was launched, most people couldn’t have predicted just how quickly these tools would evolve. AI’s rapid progress has been especially game-changing for the IT field. It’s as if IT professionals decided, "Why not automate parts of our own jobs first?" And here we are, seeing the impact of that decision. In just two years, AI has made strides that feel almost unreal.
I remember when many companies had strict no-AI policies. Legal restrictions were everywhere—using AI to analyze or write code was off the table. Fast forward to now, and it’s a whole different story. Many companies not only allow AI; they actively encourage it, seeing it as a way to work faster and more effectively. Tasks that used to take days can now be handed off to AI, letting us focus on deeper engineering work.
Today, I want to take you through how I, as a DevOps engineer and cloud architect, am using AI assistants to streamline different parts of my job.
https://youtu.be/4FNyMRmHdTM?si=F2yOv89QU9gQ7Hif
Key AI Tools in DevOps and Their Use Cases
ChatGPT: Your All-in-One Assistant for DevOps
Let’s start with ChatGPT. By now, it’s a household name, probably the most recognized AI assistant and where so much of this tech revolution began. So, why do I rely on ChatGPT?
First off, it’s built on some of the largest AI models out there, often debuting groundbreaking updates. While it might feel more like a generalist than a specialist in niche areas, its capabilities for everyday tasks are impressive.
I won’t go into too much detail about ChatGPT itself, but let’s look at some recent updates that are genuinely game-changing.
For starters, ChatGPT 4.0 is now the new standard, replacing previous models 3.5 and 4. It’s a foundational model designed to handle just about any task, as they say.
But the real excitement comes with ChatGPT’s new Search feature. This is a huge leap forward, as the model can now browse the internet in real-time. Previously, it was limited to its last training cutoff, with only occasional updates. Now, it can look up current information directly from the web.
Here’s a quick example: You could ask, “What’s the current exchange rate for the Ukrainian hryvnia to the euro?” and ChatGPT will fetch the latest answer from the internet. It can even calculate taxes based on the most recent rates and regulations.
Even better, you can see the sources it uses, so you can double-check the information. This feature positions ChatGPT as a potential Google alternative for many professional questions.
Another exciting addition is ChatGPT Canvas, which offers a more visual and interactive way to collaborate with the AI. This feature lets you create and adjust diagrams, flowcharts, and other visuals directly in the chat interface. It’s perfect for brainstorming sessions, project planning, and breaking down complex ideas in a more visual format.
Personally, I use ChatGPT for a range of tasks — from quick questions to brainstorming sessions. With Search and Canvas, it’s evolving into an even more versatile tool that fits a variety of professional needs. It’s like having an all-in-one assistant.
To summarise, ChatGPT is good for:
🔍 Real-Time Web Access with Search
ChatGPT’s built-in browser now retrieves up-to-date information, making it more than a static assistant. Whether you're checking the latest AWS pricing or debugging region-specific issues, this tool has you covered.
🧠 Complex Task Handling
From brainstorming pipeline structures to writing Bash scripts, ChatGPT handles high-level logic, templating, and document writing.
🗂️ Canvas: Visualizing Ideas
With Canvas, you can sketch infrastructure diagrams, brainstorm architectures, or visually debug pipeline issues—all within the same AI environment.
Use it for:
YAML templating
Cost estimation
Visual breakdowns of infrastructure
Researching live documentation
Transform Your DevOps Process with Gart's Automation Solutions!
Take your DevOps to the next level with seamless automation. Contact us to learn how we can streamline your workflows.
Claude: AI for Project Context and Helm Charts
Claude’s project memory and file management capabilities make it ideal for large, structured DevOps tasks.
Let’s dive into a more specialized AI tool I use: Claude. Unlike other AI assistants, Claude is structured to manage files and data in a way that’s incredibly practical for DevOps. One of the best features? The ability to organize information into project-specific repositories. This setup is a huge help when juggling different environments and configurations, making it easier to pick up complex projects exactly where you left off.
Here’s a quick example. Imagine I need to create a new Helm chart for an app that’s been running on other machines.
My goal is to create a universal deployment in Kubernetes. With Claude, I can start a project called "Helm Chart Creation" and load it up with essential context—best practices, reference files, and so on. Claude’s “Project Knowledge” feature is a game-changer here, allowing me to add files and snippets it should remember. If I need references from Bitnami’s Helm charts, which have an extensive library, I can just feed them directly into Claude.
Now, say I want to convert a Docker Compose file into a Helm chart. I can input the Docker Compose file and relevant Helm chart references, and Claude will scaffold the YAML files for me. Sure, it sometimes needs a bit of tweaking, but the initial output is structured, logical, and saves a massive amount of time.
In a recent project, we had to create Helm charts for a large number of services. A task that would’ve previously taken a team of two to four people several months now took just one person a few weeks, thanks to Claude’s ability to handle most of the code organization and structuring.
The only downside? You can only upload up to five files per request. But even with that limitation, Claude is a powerful tool that genuinely understands project context and writes better code.
To summarise, Claude is good for:
🧾 Project Knowledge Management
Organize your tasks by repository or project. Claude remembers past inputs and references, making it useful for tasks like:
Converting Docker Compose to Helm
Creating reusable Helm charts
Structuring Kubernetes deployments
GitHub Copilot for Code Generation
Next up, let’s talk about Copilot for Visual Studio. I’ve been using it since the early days when it was just GitHub Copilot, and it’s come a long way since then. The latest version introduces some great new features that make coding even more efficient.
One small change is that Copilot now opens on the right side of the Visual Studio window—just a layout tweak, but it keeps everything organized. More importantly, it now taps into both OpenAI models and Microsoft’s proprietary AI, plus it integrates with Azure. This means it can work directly within your cloud environment, which is super useful.
Copilot also gets smart about your project setup, reading the structure and indexing files so it understands what you’re working on. For example, if I need to spin up a Terraform project for Azure with a Terraform Cloud backend, I can just ask Copilot, and it’ll generate the necessary code and config files.
It’s great for speeding up code writing, starting new projects, and even handling cloud services, all while helping troubleshoot errors as you go. One of my favorite features is the “Explain” option. If I’m stuck on a piece of code, I can ask Copilot to break it down for me, which saves me from searching online or guessing. It’s a real timesaver, especially when working with unfamiliar languages or code snippets.
GitHub Copilot is good for:
🚀 Cloud-Specific Code Generation
Copilot now understands infrastructure-as-code contexts:
Launch a Terraform project for Azure in minutes
Create config files and debug errors automatically
💬 Code Explainability
One standout feature is the “Explain this code” function. If you're unfamiliar with a script, Copilot explains it clearly—perfect for onboarding or refactoring.
Use it for:
Cloud provisioning
Writing CI/CD scripts
Boilerplate code in unfamiliar languages
Effortless DevOps Automation with Gart!
Let us handle the heavy lifting in DevOps. Reach out to see how Gart can simplify and accelerate your processes.
VZero for UI and Front-End Prototyping
Finally, let’s take a look at VZero from Vercel. I don’t use it as often as other tools, but it’s impressive enough that it definitely deserves a mention.
VZero is an AI-powered tool that makes creating UI forms and interfaces fast and easy. For someone like me—who isn’t a frontend developer—it’s perfect for quickly putting together a UI concept. Whether I need to show a UI idea to a dev team, share a concept with contractors, or visualize something for stakeholders, VZero makes it simple.
For example, if I need a page to display infrastructure audit results, I can start by giving VZero a basic prompt, like “I want a page that shows infrastructure audit results.” Even with this minimal direction, VZero can create a functional, attractive UI.
One of the best things about VZero is how well it handles design context. I can upload screenshots or examples from our existing website, and it’ll match the design language—think color schemes, styles, and layout. This means the UI it generates not only works but also looks consistent with our brand.
The tool even generates real-time editable code, so if I need to make a quick tweak—like removing an extra menu or adjusting the layout—it’s easy to do. I can just ask VZero to make the change, and it updates the UI instantly.
There are two main ways I use VZero:
Prototyping: When I have a rough idea and want a quick prototype, VZero lets me visualize it without having to dive into frontend code. Then, I can pass it along to frontend developers to build out further.
Creating Simple Forms: Sometimes, I need a quick form for a specific task, like automating a workflow or gathering input for a DevOps process. VZero lets me create these forms without needing deep frontend expertise.
Since VZero is built on Vercel’s platform, the generated code is optimized for modern frameworks like React and Next.js, making it easy to integrate with existing projects. By using AI, VZero cuts down the time and effort needed to go from idea to working UI, making frontend design more accessible to non-experts.
VZero is good for:
✨ Design Context Awareness
Upload a screenshot of your existing product, and VZero will generate matching UI components. It mimics style guides, layouts, and brand consistency.
🧩 Use Cases:
Prototyping admin dashboards
Mocking audit interfaces
Creating forms for automation workflows
Built on modern React/Next.js frameworks, it outputs usable code for immediate integration.
AI’s Impact on Productivity and Efficiency
The cumulative impact of these AI tools on DevOps workflows is significant. What used to take entire teams months to complete can now be accomplished by a single engineer within weeks, thanks to AI-driven automation and structured project management. The cost-effectiveness of these tools is also noteworthy; a typical monthly subscription to all mentioned AI tools averages around $70. Given the efficiency gains, this represents a valuable investment for both individual professionals and organizations.
How to Use AI in DevOps Without Sacrificing Quality
To maximize AI’s potential, DevOps professionals must go beyond simple code generation and understand how to fully integrate these tools into their workflows. Successful use of AI involves knowing:
When to rely on AI versus manual coding for accuracy and efficiency.
How to assess AI-generated results critically to avoid errors.
The importance of providing comprehensive prompts and reference materials to get the best outcomes.
To maximize value:
🔍 Review AI output like you would a junior developer’s code.
🧠 Prompt engineering matters—give context, not just commands.
⚠️ Don’t outsource critical logic—review security and environment-specific settings carefully.
By mastering these skills, DevOps teams can ensure that AI tools support their goals effectively, adding value without compromising quality.
Conclusion
AI tools have become indispensable in DevOps, transforming how engineers approach their work and enabling them to focus on higher-level tasks. As these tools continue to evolve, they are likely to become even more integral to development operations, offering ever more refined support for complex workflows. Embracing AI in DevOps is no longer a choice but a necessity, and those who learn to use it wisely will enjoy substantial advantages in productivity, adaptability, and career growth.
If you’re not leveraging AI in DevOps yet, you're falling behind.Want to scale your DevOps efficiency with AI-backed automation?Connect with Gart Solutions to modernize your pipelines today.