About the Client
Spiral Technology is a Boston-based leader in augmented reality for industrial inspections. Their forward-thinking platform integrates augmented reality to optimize inspection processes. Committed to top-tier security and compliance, Spiral Technology partnered with Gart for expert guidance in ISO 27001 audits and cloud infrastructure design.
Challenge
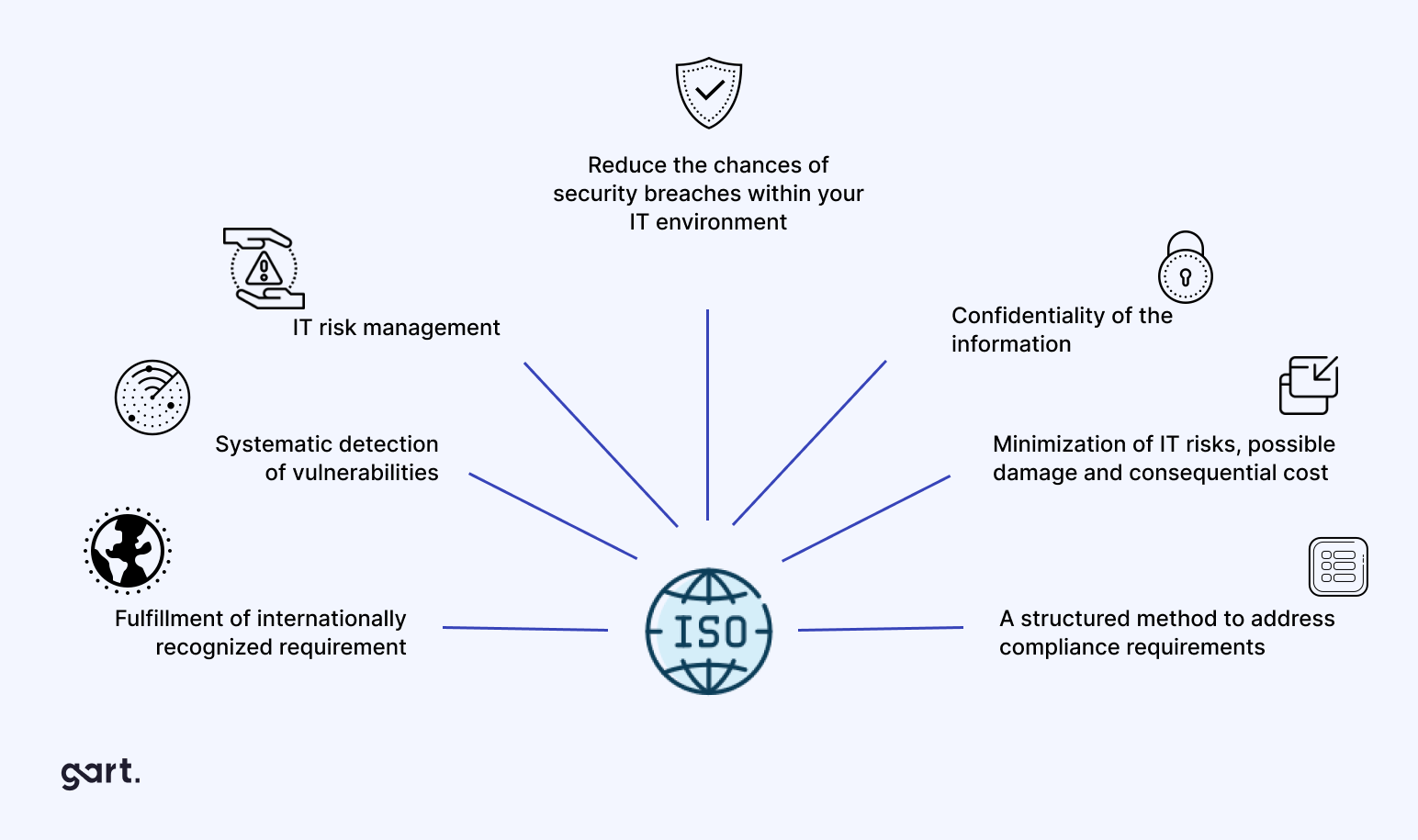
Spiral Technology, a leading Augmented Reality platform for industrial inspections, faced the critical challenge of preparing for ISO 27001 audits while concurrently launching a product for a significant customer. The complexity of aligning DevOps tasks, ensuring compliance, and migrating cloud infrastructure demanded expert assistance to navigate seamlessly.
Solution
In their pursuit of a trusted ally, Spiral Technology discovered Gart through an online search. Our dedicated team, consisting of 2 experts, embarked on a thorough engagement. We tackled over 55 pending ISO 27001 compliance tasks, meticulously reviewed DevOps settings, and orchestrated a seamless migration from Google Cloud Platform (GCP) to Azure, leveraging Terraform and automation tools.
The 55 pending ISO 27001 compliance tasks were categorized into three levels: Infrastructure and Cloud Security, Personal Security, and Code Security.
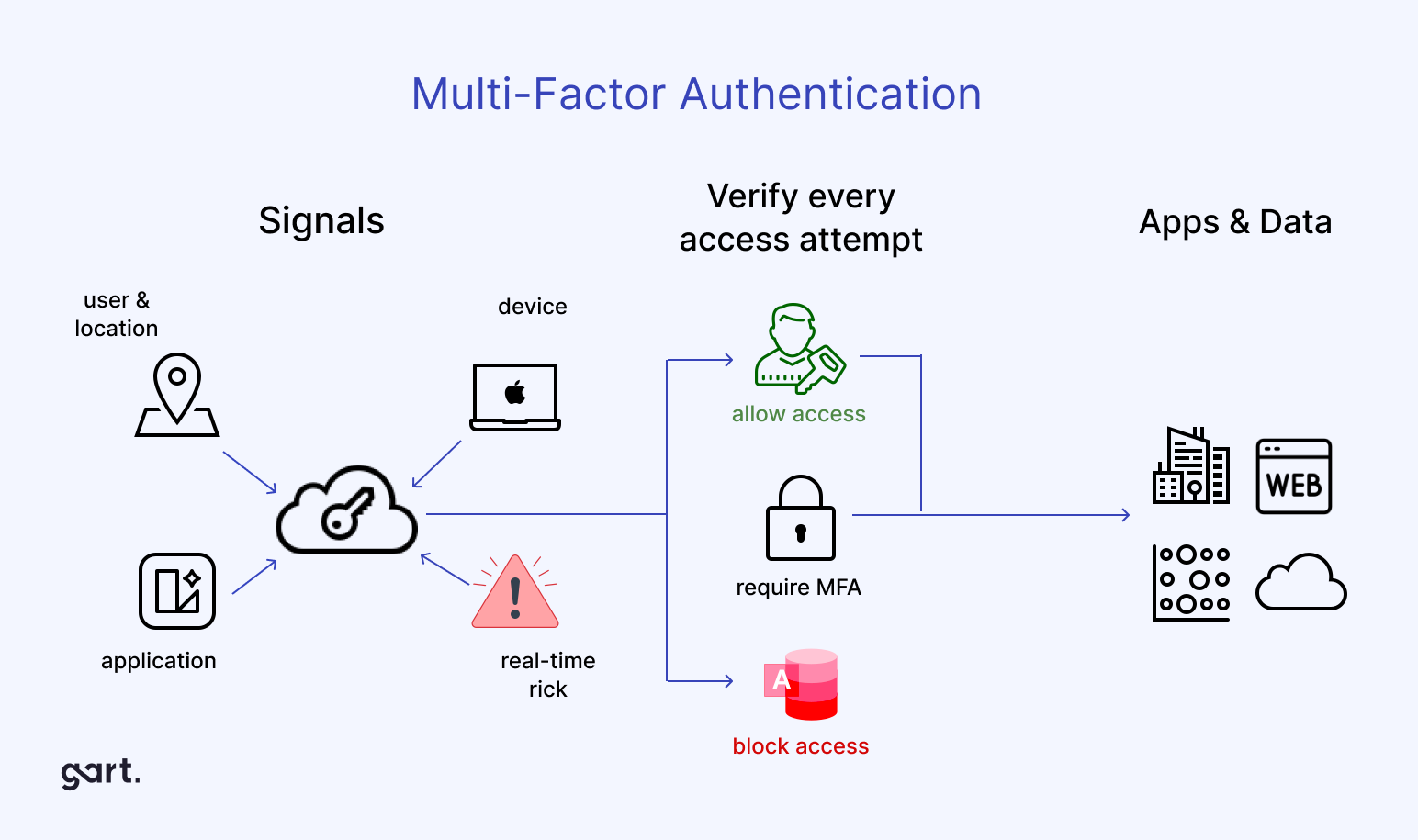
Cloud Security
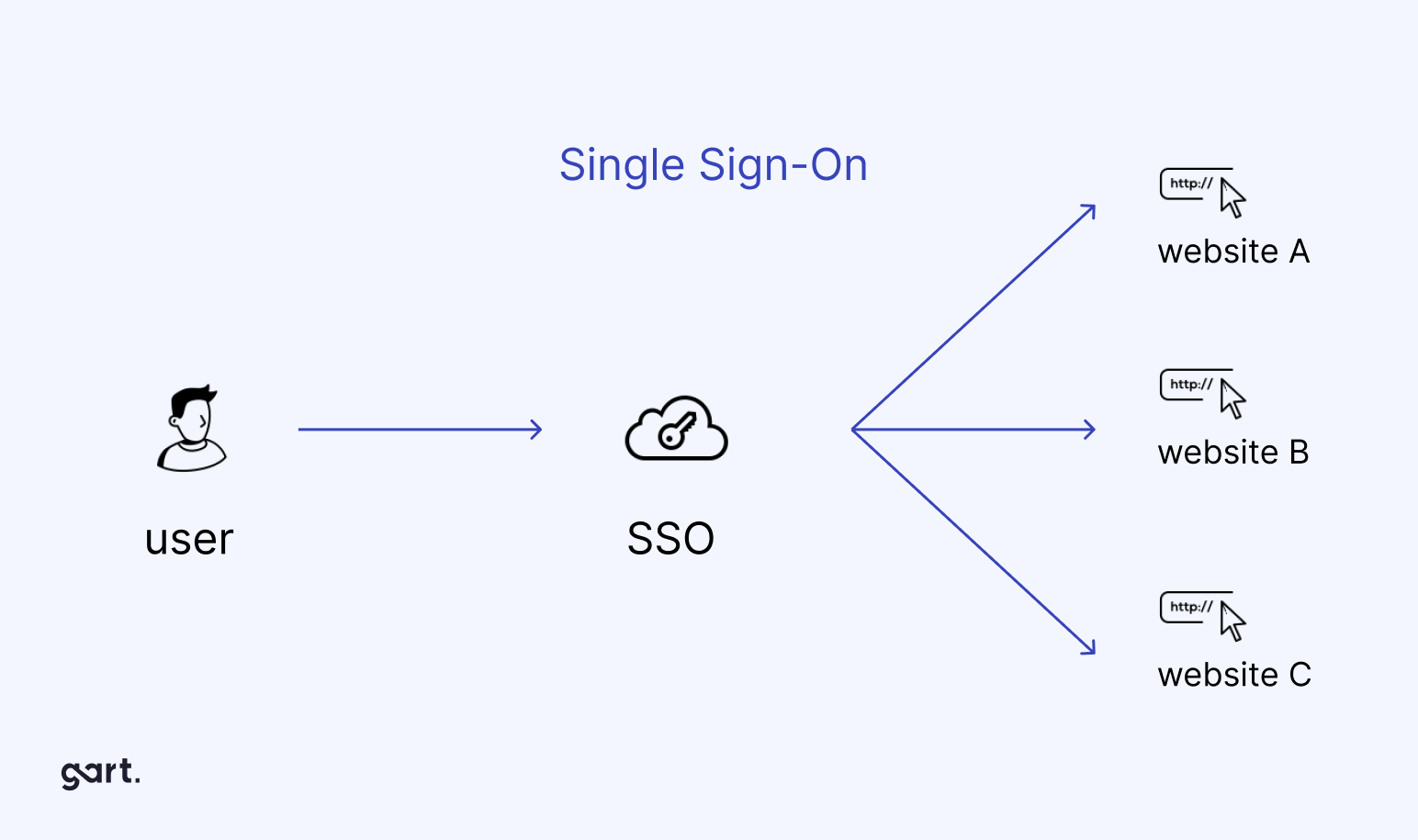
In the realm of cloud security, the initial assessment of the Google Cloud Platform (GCP) revealed open configurations. Gart’s experts configured security groups and firewalls to restrict public access to services. Single Sign-On (SSO) integration with GCP’s Google Workspace enhanced overall security management. This allowed centralized control, including the implementation of Multi-Factor Authentication (MFA) for all GCP access.
The client’s code repository, hosted on GitLab, underwent similar enhancements. MFA was enforced, and access levels were configured based on roles, distinguishing between developers and administrators.
Infrastructure Security
Addressing infrastructure security, data encryption was implemented, securing the database. External access to all application endpoints was restricted, permitting entry only through a virtual private network (VPN). Backup strategies for databases were devised, ensuring data integrity and availability. Additionally, a comprehensive Backup and Disaster Recovery plan was developed and tested, complete with scenarios, response methods, and a stringent 40-minute Service Level Agreement (SLA).
Personal Security
ISO 27001 places a strong emphasis on personal security. A centralized system was established to manage and control devices used in development. A curated list of approved software for development was created, ensuring adherence to security standards.
Code Security
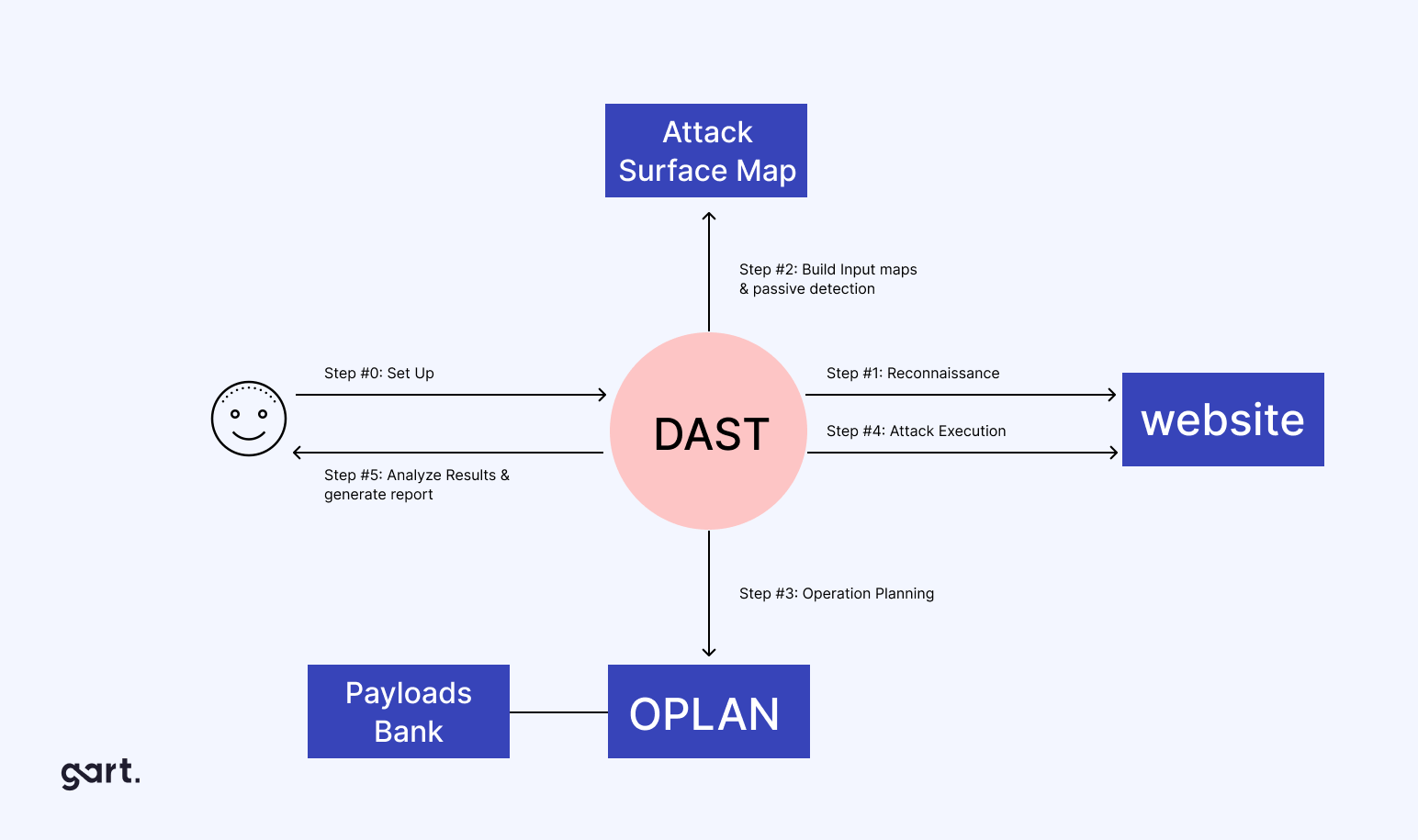
For code security, the GitLab repository played a pivotal role. It was configured securely, granting access only to those who required it. Branch protection was enforced, and Dynamic Application Security Testing (DAST) and vulnerability scans were introduced to enhance the security posture.