Are you ready for NIS2? The EU’s updated cybersecurity laws roll out in October 2024 — noncompliance could mean fines and disruption.
The NIS2 Directive, set to be implemented into the cybersecurity laws of all EU member states by October 2024, represents a significant step toward strengthening Europe’s cybersecurity framework. To comply with this directive, businesses must ensure that their digital infrastructure and data management practices are secure, resilient, and adaptable to evolving threats.
Gart Solutions offers a comprehensive suite of services designed to help organizations achieve NIS2 compliance while optimizing their IT systems for future growth.
Infrastructure Architecture Design & Consulting
At Gart Solutions, we specialize in designing robust infrastructure architectures that are tailored to meet the unique needs of your business. Our infrastructure solutions ensure secure and transparent data flows, aligning with the stringent requirements of the NIS2 Directive. By building resilient and scalable architectures, we enable businesses to maintain compliance even as they grow and evolve.
Our IT Infrastructure Consulting services provide deep insights into how various components of your IT infrastructure interact, contributing to overall security and compliance. We deliver detailed reports that highlight opportunities for optimizing infrastructure performance, security, scalability, and efficiency, serving as a strategic guide for future IT decisions.
Case Study:
One of our recent projects involved maximizing the efficiency of a client’s IT infrastructure, resulting in significant improvements in security and operational performance, all while ensuring NIS2 compliance.
We reduced infrastructure vulnerabilities by 70%, cut monthly costs by 30%, and achieved full NIS2 compliance readiness in under 8 weeks.
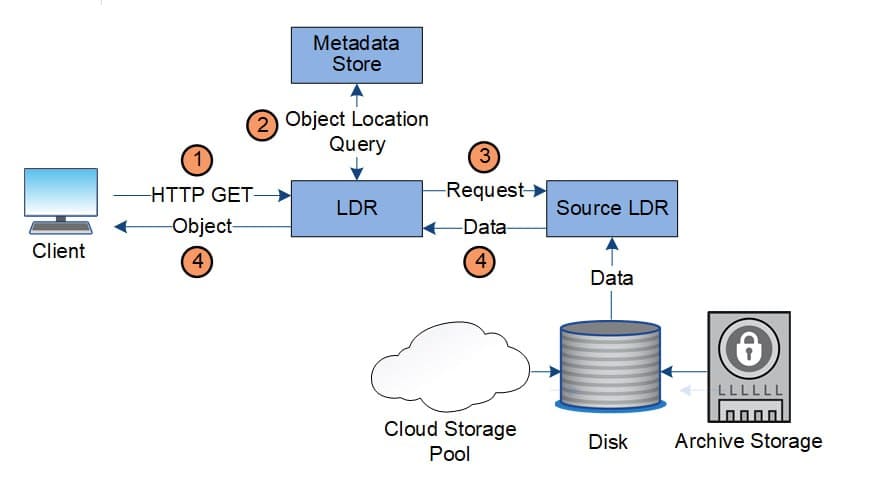
Private Cloud Migration
Migrating to a private cloud environment can significantly enhance your control over data management and security, both of which are critical for NIS2 compliance. Gart Solutions facilitates seamless transitions to private cloud environments, ensuring that your data is securely housed within the EU and meets the requirements of NIS2 and other relevant regulations.
Beyond compliance, private cloud migration offers the added benefits of reducing subscription costs and system maintenance expenses, making it a strategic choice for businesses looking to optimize their IT budgets.
Get expert advice on cloud migration strategies and approaches. Schedule a consultation here.
Data Privacy Audit & Consulting
Compliance with NIS2 requires more than just securing your data; it demands a comprehensive understanding of your data’s journey. Gart Solutions offers Data Privacy Audit & Consulting services to help you navigate the complexities of data protection legislation, including NIS2 and GDPR.
Our expert team provides actionable insights and guidance on how to protect your data throughout its lifecycle, ensuring that your business remains compliant with the latest regulatory requirements.
See how we can help to receive expert guidance on data privacy and NIS2 compliance.
Hybrid Cloud Architecture
For businesses that require the flexibility of both public and private cloud environments, Gart Solutions offers Hybrid Cloud Architecture solutions. These architectures allow you to leverage the benefits of both cloud types while ensuring that your data remains compliant with the NIS2 directive.
Our hybrid cloud solutions provide the perfect balance of security, scalability, and cost-efficiency, helping your business remain agile and compliant in a rapidly changing digital landscape.
Get a free consultation on hybrid cloud setups from Gart Solutions. Contact us.
Private vs. Hybrid Cloud Architecture for NIS2 Compliance
| Feature | Private Cloud | Hybrid Cloud |
|---|---|---|
| Definition | Cloud infrastructure used exclusively by one organization, typically hosted on-premises or in a dedicated EU-based facility. | Combination of private cloud (on-prem or hosted) with public cloud (e.g., AWS, Azure) connected for workload flexibility. |
| NIS2 Compliance Focus | Easier to enforce strict data residency, access controls, and audit logging within a closed environment. | Must ensure data exchanged between environments complies with NIS2 encryption, residency, and access requirements. |
| Data Residency | Data is stored exclusively within a controlled and typically EU-based environment. | Must ensure sensitive data remains in the private cloud or encrypted when crossing into public environments. |
| Security & Access Control | Full control over physical and logical security, access is tightly restricted and monitored. | Requires strong integration and governance across environments—identity federation, secure APIs, encrypted tunnels. |
| Cost | Higher initial setup and maintenance costs; ideal for critical systems requiring full control. | Cost-effective for organizations needing burst scalability or cloud-native services, with secure core operations on-premises. |
| Scalability | Limited to hardware capacity— requires CAPEX investment to scale. | Dynamically scalable through the public cloud for non-sensitive workloads or compute-heavy tasks. |
| Ideal For | Government, healthcare, finance —where data sovereignty and full control are paramount. | Enterprises with mixed workloads —needing both agility and regulatory adherence for sensitive operations. |
| Gart Solutions Services | – Private cloud design – Secure EU-hosted environments – Redundant storage & network isolation | – Hybrid architecture strategy – Secure data routing – Compliance-ready deployment models |
Which Architecture is Right for NIS2?
- Choose Private Cloud if your operations involve highly sensitive data, strict national regulations, or limited tolerance for third-party risk.
- Choose Hybrid Cloud if your business requires cloud-native scalability while keeping sensitive workloads under strict NIS2-aligned control.
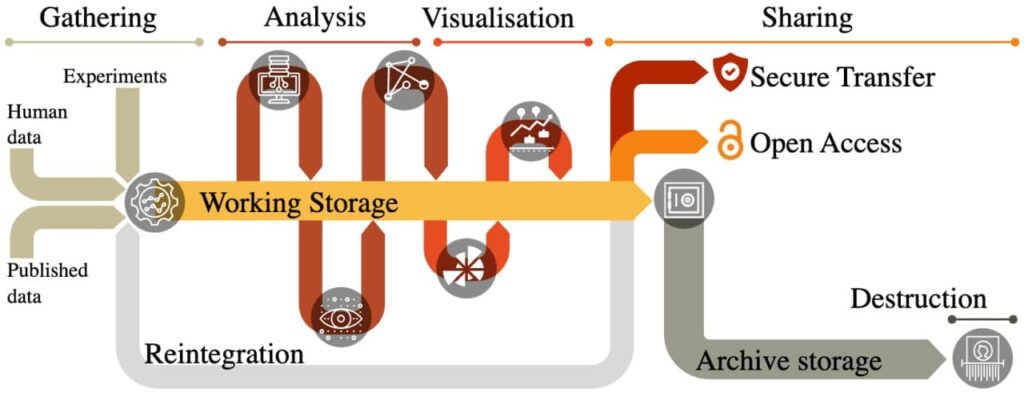
Data Store Management for AI Projects
Effective data storage is crucial for supporting AI projects, ensuring that data is accessible, secure, and efficiently managed throughout its lifecycle. Gart Solutions provides comprehensive Data Store Management services for AI projects, addressing the unique challenges posed by diverse data types and complex workflows.
We help businesses manage AI-driven projects with a focus on security and NIS2 compliance, ensuring that your data storage solutions are optimized for both performance and regulatory adherence.
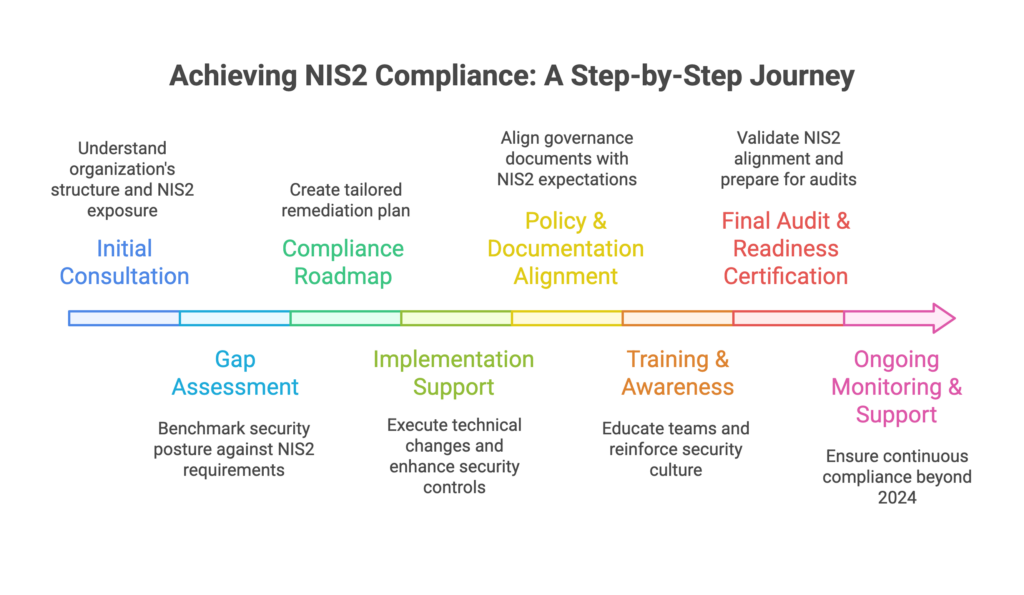
NIS2 Readiness Process with Gart Solutions
Our NIS2 compliance process starts with a free consultation to identify your organization’s exposure and readiness level.
We then perform a gap assessment against NIS2 requirements and develop a tailored roadmap outlining necessary improvements across infrastructure, policies, and security controls.
Next, we implement technical upgrades, like secure cloud environments, access controls, and monitoring systems, followed by aligning your policies and documentation for audit readiness.
We provide team training, conduct a final internal audit, and prepare you for external certification.
Post-compliance, we offer continuous monitoring and support to keep you aligned with evolving EU regulations.
Final Words
At Gart Solutions, we are committed to helping businesses navigate the challenges of building a compliant infrastructure for NIS2, preparing for NIS2 compliance while optimizing it for future growth. Our tailored services ensure that your business is not only compliant with the latest regulations but also equipped to thrive in a rapidly evolving digital landscape.
To get started – here is a Checklist that will help you to be prepared for NIS2 Compliance Update.
Download our free NIS2 readiness checklist now.
See how we can help to comply with the latest NIS2 requirements









