Client Background
Our client is a provider of a software platform designed to streamline and automate various operational tasks within golf clubs.
The software is primarily tailored for golf kiosks, which are self-service vending machines, offering integrated booking, intelligent payment processing, efficient user check-in, sophisticated discount management, seamless and rapid equipment rental, along with other associated services.
Business Challenge
The client engaged Gart with a specific request for a comprehensive Security Audit (due to a cybersecurity frameworks (NIST, ISO 27001 and ISO 27002, SOC2).
The main objective of this audit was to get a detailed report encompassing all identified vulnerabilities, prioritize the recommended measures, and proactively mitigate potential exposure to cyber threats.
Solution
During the security assessment (the 1st phase of our proposal), we conducted a review of application security vulnerabilities. We systematically categorized and stratified cyber threats based on their risk profiles. Subsequently, we undertook decisive actions fortifying the software code against potential cyber intrusions and malicious activities.
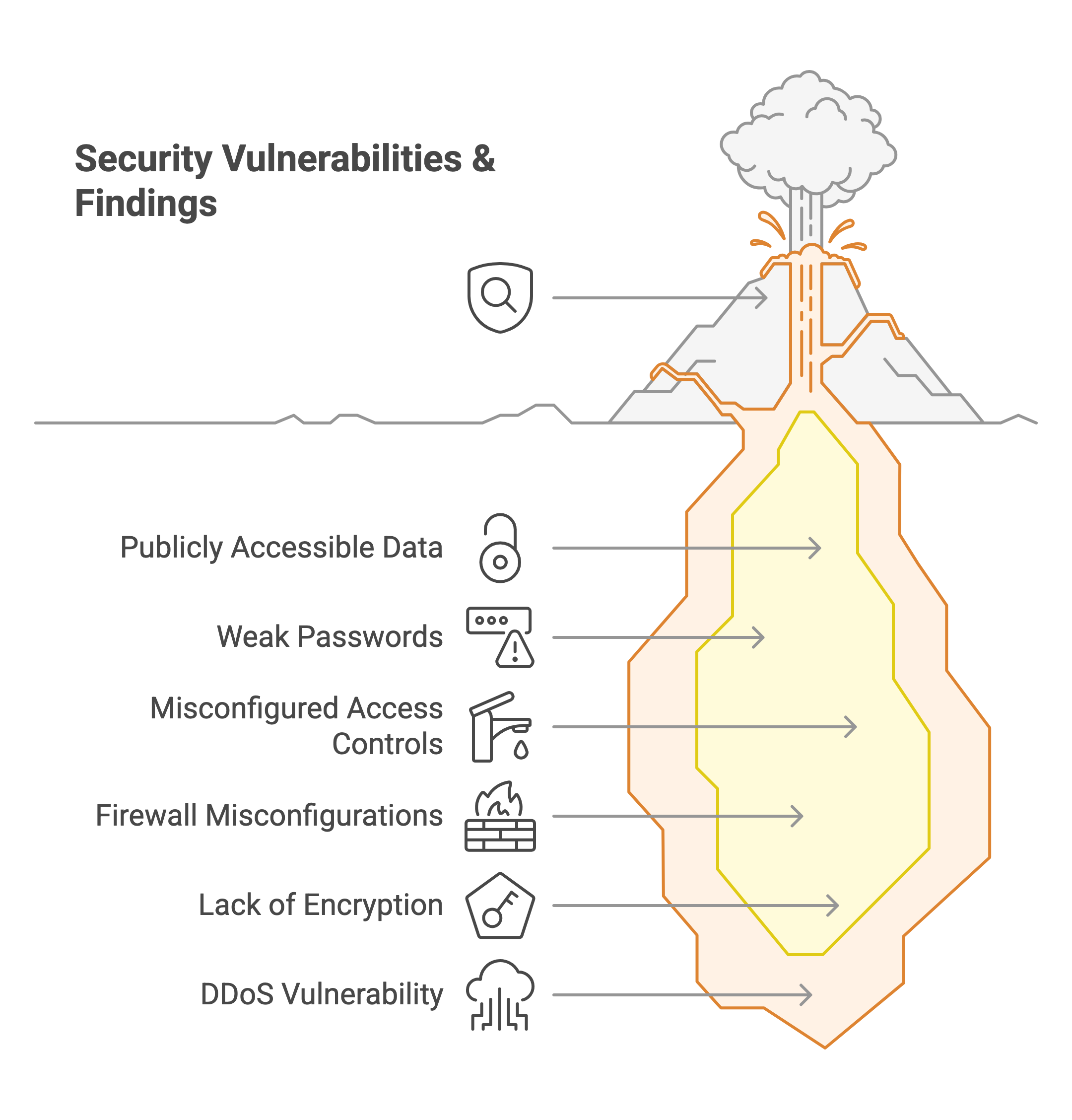
Key security findings included:
- Instances of publicly accessible addresses and passwords
- Instances of weak passwords
- Inadvertent access to databases and whitelists
- Instances of misconfigured firewalls
- The absence of robust encryption mechanisms.
The 2nd phase of our proposal pertains to the Infrastructure Assessment.
As an outgrowth of our security audit outcomes, we recommended an Infrastructure Migration strategy that capitalizes on cutting-edge technologies and services.
This includes the adoption of Dockerization and the assimilation of the five core tenets of DevOps, commonly referred to as the “Five C’s”: continuous integration, comprehensive testing, seamless delivery pipelines, efficient deployment practices, and monitoring protocols.